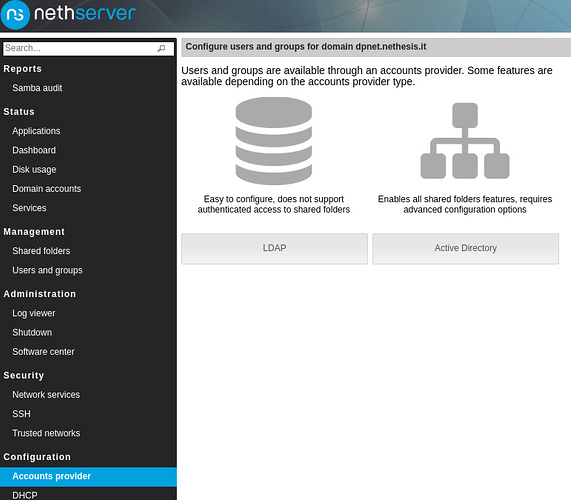
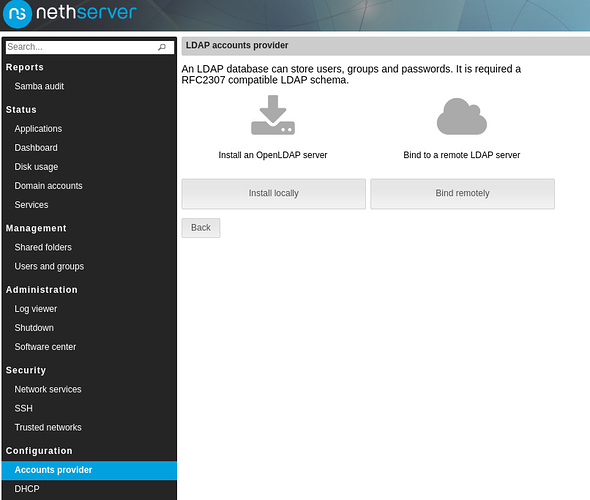
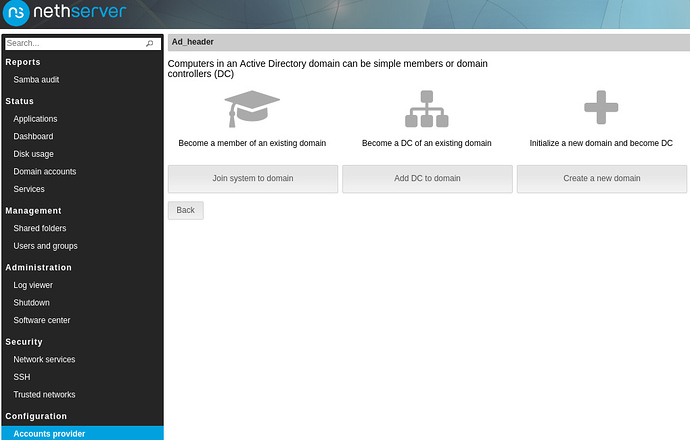
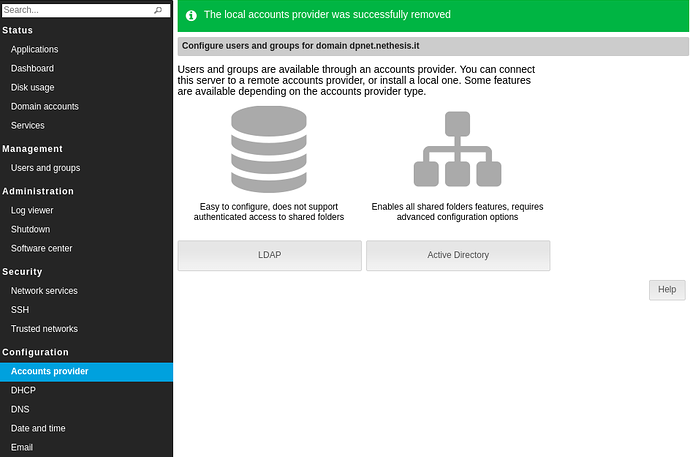
I was talking with @giacomo and @filippo_carletti about the Accounts provider page and all around. We would like to improve it, by adding (or exposing) some useful features and make the resulting server configuration more flexible.
Please, join this discussion and provide your thoughts!
Set a custom Realm name in local DC configuration
Today the Realm has the same value of the domain suffix of the machine FQDN. Let’s say the FQDN is seven.nethserver.org, the domain suffix is nethserver.org and the AD Realm is forced be the same.
If the Realm becomes a separate parameter, a new AD forest could be provisioned with an invented nethserver.local realm or a separate third level domain, like ad.nethserver.org. This would help to solve many DNS configuration issues!
Moreover, the same parameter helps with existing AD environments and mail server configuration. It would be easy to configure predefined mailboxes like user@nethserver.org, and limit AD to its specific DNS zone.
Who comes from ns6 already knows this kind of configuration!
Install/Uninstall a local accounts provider
During the development of the upgrade procedure for ns6 we implemented some uninstall procedures! We can now generalize them and expose on the UI too.
An import_users script from CSV already exist in nethserver-sssd package. We could dump the users and groups lists to a CSV file when the accounts provider is uninstalled, so that they can be re-imported to a different one. Passwords cannot be migrated between LDAP and AD because are encrypted with one-way algorithms.
Moreover, we would like to install a local account provider directly from the Accounts provider page. Going to Software center should not be a pre-requisite to install a local accounts provider!
Add NethServer DC to an existing AD forest
We must verify the new Samba release (4.6) compatibility. Some successful cases have been already reported with 4.4 and we are positive!
Change the IP of the nsdc Linux Container
A manual procedure is already documented. We can expose it on the UI!
Other improvements to Server Manager
- Add GSSAPI authentication method to Server Manager LDAP client, to retrieve Users and Groups lists without requiring an additional account with remote AD accounts provider
- Raise the maximum number of entries retrieved by the Server Manager LDAP client to a configurable parameter (like RSAT tools do)
- Upgrade the Samba DC to 4.6. Make available updates visible from Server Manager (shown as a “todo”?).
References
There are many support requests that turn around the current Active Directory configuration. This is a brief list:
- Alternative UPN Suffix
- Domaincontroller with Samba AD - activation fails
- Samba DNS updates from DHCP
- Custom email address nethserver 7 final
- Multiple addresses when connecting to AD Server
- [Solved] How do you manage your DNS records?
- How to begin NethServer Active Directory logins from Fedora25 Client OS
- Questions about AD join
- Nethserver Web UI port 980 "This site can't be reached"
- NTP time synchronization with Samba DC
- Changing the Domain Controller Instructions
- SET Default Email Domain