Beta1 is here! 
Our firewall has reached a new level of maturity as it enters the Beta1 version, with a lot of new features and enhancements for our vibrant community.
This beta release signals a significant shift to a new UI as the primary configuration interface, while still maintaining the versatility of Luci for specific configurations and verification purposes.
Key Highlights
New Configuration Interface
The new UI is now the primary configuration interface, streamlining the configuration experience. The old Luci interface remains active for configurations not yet available in the new UI and for verification purposes.
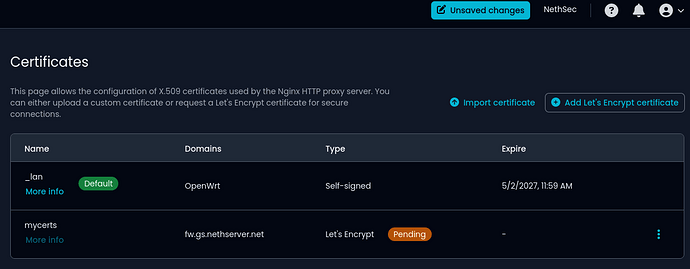
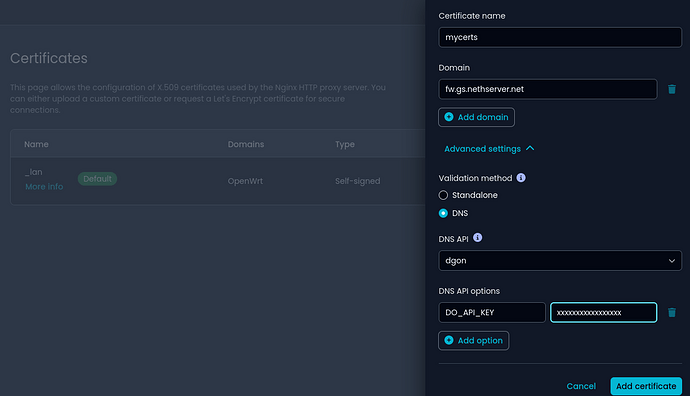
Certificate and Reverse Proxy Management
Navigate a dedicated page for easy management of certificates and reverse proxy settings. The import process for both configurations has been significantly improved. Now, you can also use DNS verification to request Let’s Encrypt certificates, supporting wildcard certificates.
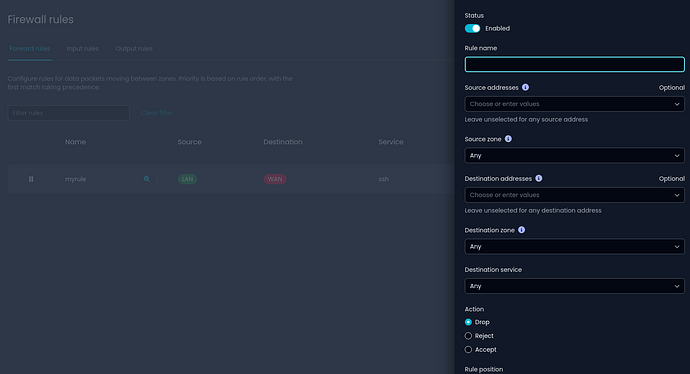
Firewall Rules Configuration
Added a new page for configuring firewall rules, offering enhanced control. Users are encouraged to use this page for compatibility and optimal performance.
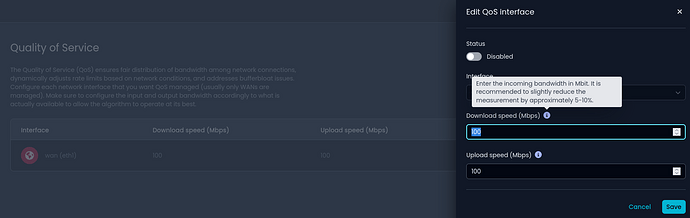
Quality of Service (QoS) Configuration
Tailor your network traffic management with a newly introduced QoS configuration page, ensuring a seamless online experience.
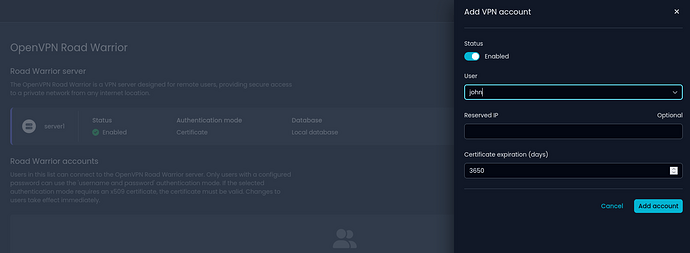
OpenVPN Roadwarrior Configuration
Dive into the convenience of a dedicated page for configuring OpenVPN Roadwarrior. The migration process for the new implementation has been diligently updated.
Other Changes in Beta1
-
Log Storage on Main Disk Partition
Optimized storage resources by utilizing a partition of the main disk for logs, offering a flexible solution. -
Migration and Compatibility Improvements
Improved migration processes for multiwan and OpenVPN tunnels, enhancing overall system compatibility. -
Upgrade and Migration Management
Streamlined management experience for upgrades and migrations, ensuring a smoother transition for users. -
Versioning System
More clarity with our new versioning system, uniquely identifying each image to simplify tracking releases. -
Usability Enhancements
Benefit from numerous usability improvements and issue fixes across existing pages, providing a more user-friendly environment.
Try it!
Follow the instructions, download and try it
Download ![]()
Documentation
Read about all features, migration from NS7 and more inside the official documentation
We need your feedback
Known bugs in the new interface can be found here. Your input is invaluable in shaping the future of NethSecurity.
Explore the new interface confidently, but if you encounter bugs, please report them in a new thread.
Your feedback during this beta phase is crucial for refining NethSecurity.
Please open a new topic in the NethSecurity category
Add tags like feature bug support
We invite you to explore the Beta1 release, share your feedback, and be a part of the NethSecurity community. Thank you for your continued support and dedication to open-source excellence!
Happy exploring ![]() !
!
The NethSecurity Team