Installing Guacamole 1.1.0 with NethServer AD/LDAP & Fail2Ban
Apache Guacamole is a clientless remote desktop gateway supporting multiple protocols (VNC, SSH, RDP to name a few) via a web browser. This How To builds primarily on the work of @mrmarkuz and is meant to document a common hypothetical deployment process. This guide continues on from the Installing NethServer 7.7 on XCP-NG 8.0 via Xen Orchestra (XOA).
Prerequisites:
NethServer 7.7 installed& updated with at least 1 NIC/Static IP
Fail2Ban installed from Software Center - optional
Let’s Encrypt certificate and TLD (example.com) - optional
NethServer as the SAMBA4/AD Account Provider - optional
Assumptions & Scope:
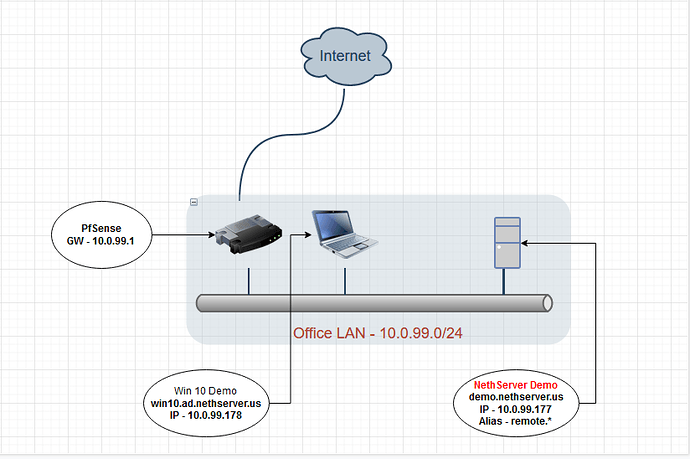
Office LAN Network: 10.0.99.0/24
PfSense Gateway - 10.0.99.1
NethServer VM 1 NIC - Static IP 10.0.99.177
-
Host Name - demo.nethserver.us (ns-example.yourdomain.com)
-
Alias Name - remote.nethserver.us
NethServer SAMBA4/AD Settings
-
Change built in ‘admin’ account password - (set to Nethdemo)
-
Create 2 user accounts & passwords (users ‘test1’ & ‘test2’ with password testtest)
-
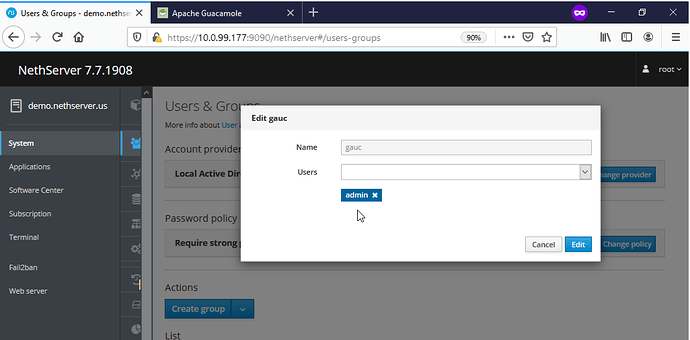
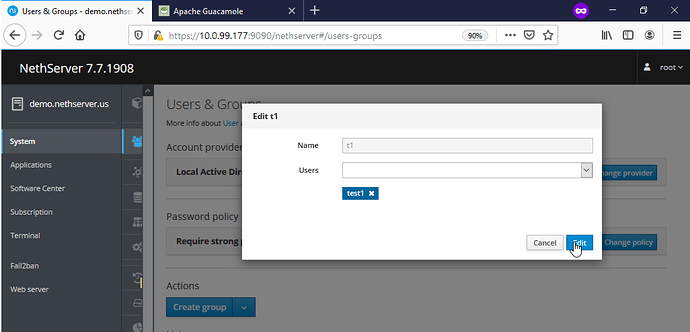
Create a new group ‘guac’ with user ‘admin@’ assigned & a new group called ‘t1’ with user ‘test1@’ assigned
Installing Guacamole via Cockpit
Open a web browser and log into your NethServer install at https://10.0.99.177:9090 (https://demo.example.com:9090) and navigate to the Terminal tab.
Add the Mrmarkuz repository to NethServer by Copy & Pasting (Shift + Insert) the following below into the terminal and press Enter:
yum -y install https://mrmarkuz.dynu.net/mirror/mrmarkuz/7/noarch/nethserver-mrmarkuz-0.0.1-4.ns7.noarch.rpm
After confirming that the repository was successfully added the next step is to install NethServer-guacamole by Copy & Pasting (Shift + Insert) the following below into the terminal and press Enter:
yum install -y https://mrmarkuz.dynu.net/mirror/devtest/nethserver-guacamole-0.0.1-1.ns7.noarch.rpm
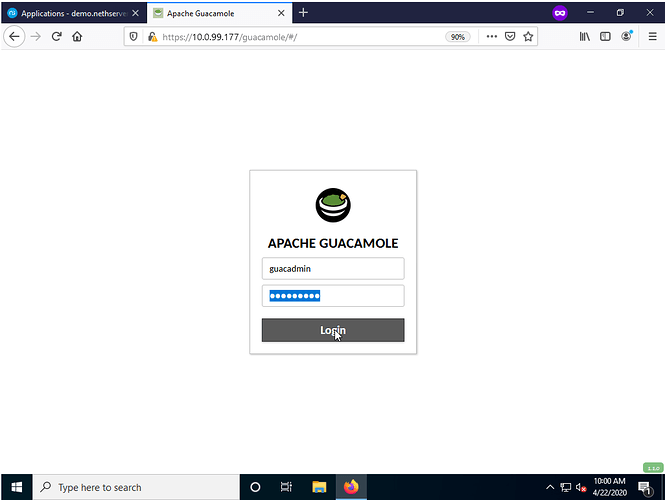
After confirming the installation process has completed, access to the Guacamole service can be reached at https://YOURNETHSERVER/guacamole (https://10.0.99.177/guacamole for this demo) with the credentials below:
Username: guacadmin
Password: guacadmin
Redirect Guacamole Web URL via Virtual Host - Optional
Change how you access the Guacamole web URL from https://example1.com/guacamole (https://demo.nethserver.us/guacamole in this example) to https://anotherexample.com (https://remote.nethserver.us in this example) by Copy & Pasting (Shift + Insert) the following below into the terminal and press Enter:
config setprop guacd VirtualHost remote.nethserver.us
signal-event nethserver-guacamole-update
Setup & Enable Guacamole Fail2Ban Jail - Optional
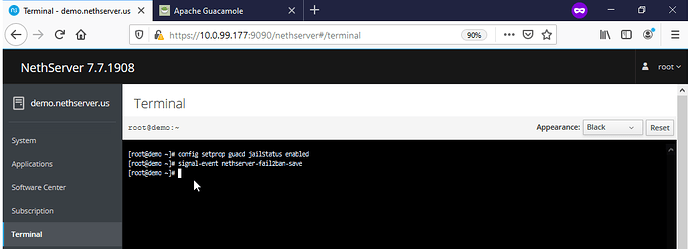
Create and enable a Fail2Ban jail for Guacamole within the same Terminal used in the previous steps by Copy & Pasting (Shift + Insert) the following below into the terminal and press Enter:
config setprop guacd jailStatus enabled
signal-event nethserver-fail2ban-save
You can disable the Guacamole jail by Copy & Pasting (Shift + Insert) the following below into the terminal and press Enter:
config setprop guacd jailStatus disabled
signal-event nethserver-fail2ban-save
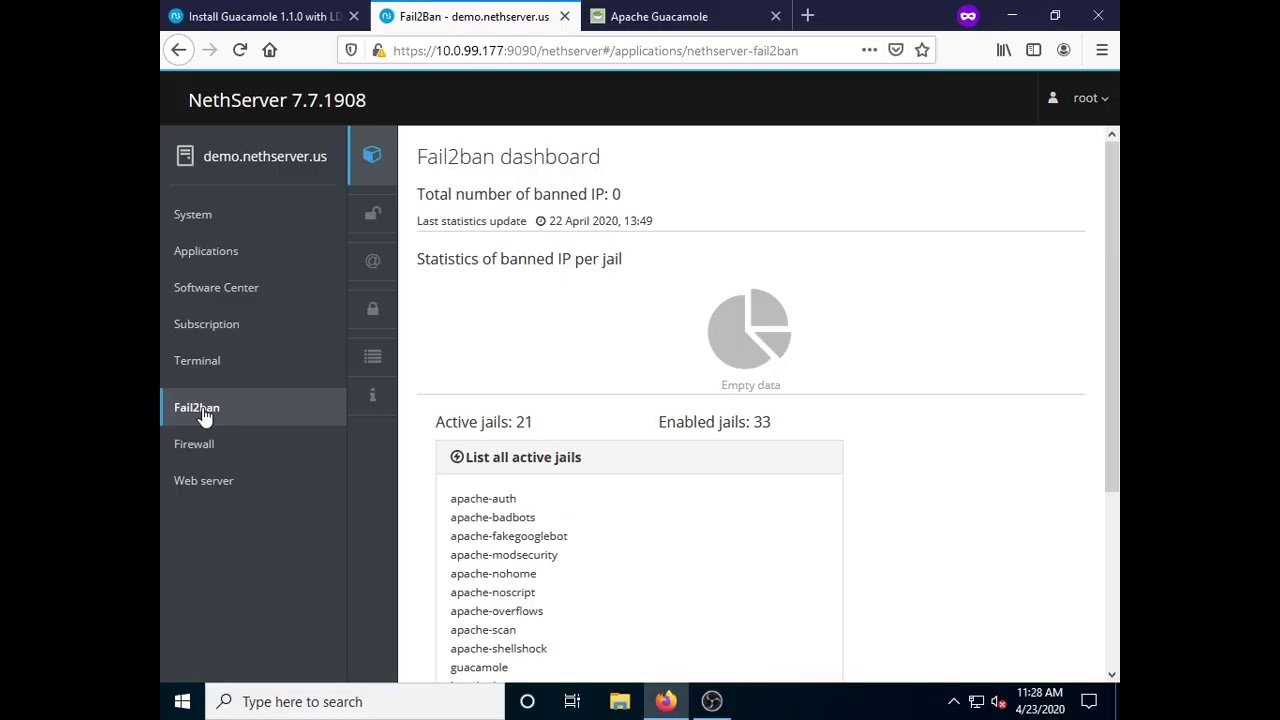
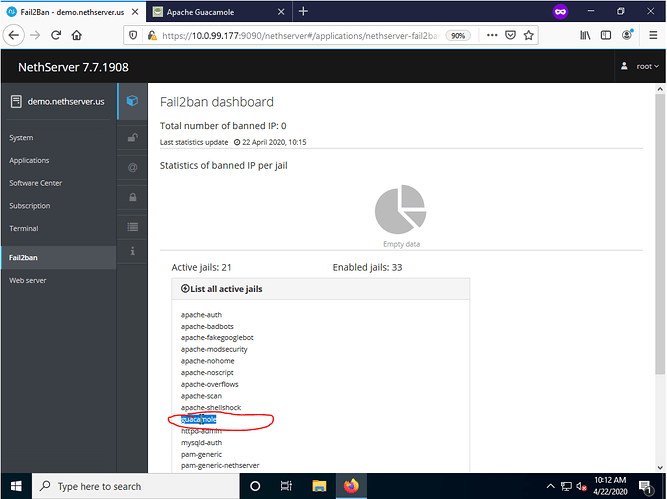
You can visually confirm the jail is active by navigating to the Fail2Ban dashboard and viewing the list of active jails. NOTE - Fail2Ban’s default login threshold is 3 attempts before lockout. Be conscious of this when testing/new users accessing this service and adjust your Fail2Ban settings accordingly.
Prepare Guacamole for NethServer AD/LDAP Authentication - Optional
To have Guacamole authenticate users against NethServer AD/LDAP users we need to configure NS to disable strong authentication and correct LDAP settings using he same Terminal used in the previous steps by Copy & Pasting (Shift + Insert) the following below into the terminal and press Enter:
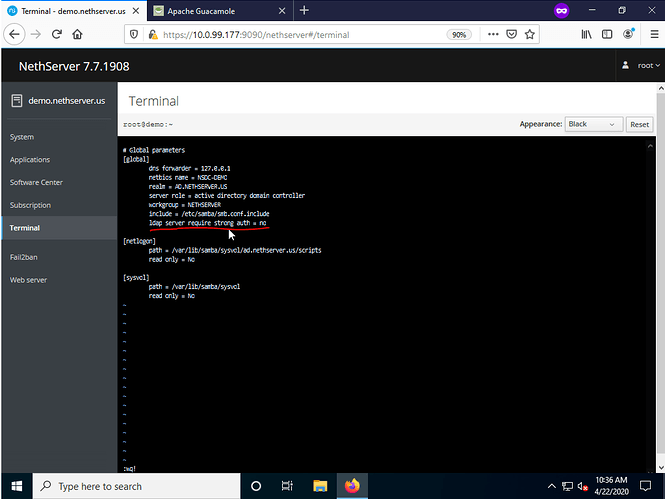
vi /var/lib/machines/nsdc/etc/samba/smb.conf
Add the following under the [global] section(see picture) and save:
ldap server require strong auth = no
After confirming the modification, restart the SAMBA4/AD service by Copy & Pasting (Shift + Insert) the following below into the terminal and press Enter:
systemctl -M nsdc restart samba
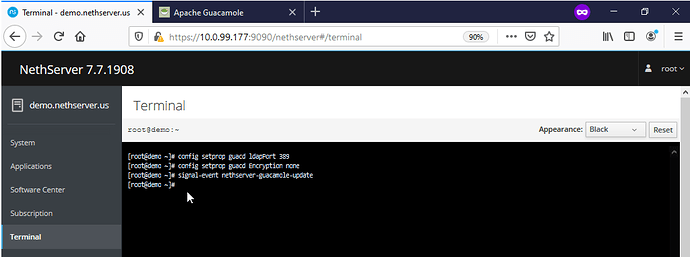
Lastly, set the correct following LDAP settings for Guacamole by Copy & Pasting (Shift + Insert) the following below into the terminal and press Enter:
config setprop guacd ldapPort 389
config setprop guacd Encryption none
signal-event nethserver-guacamole-update
Connect Guacamole to NS AD/LDAP Backend - Optional
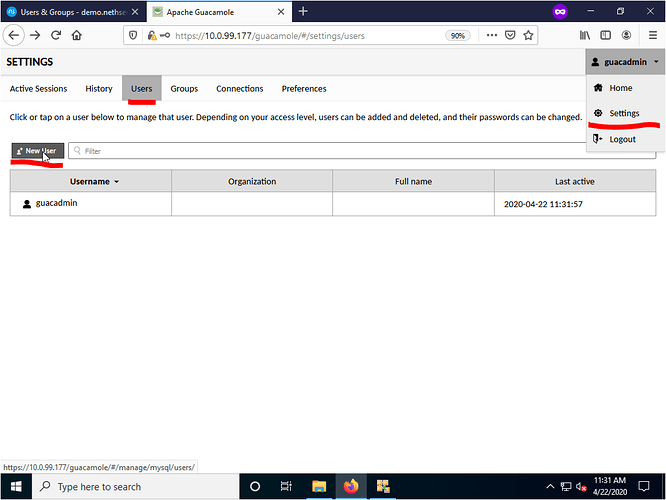
Open a web browser and log into your Guacamole setup by navigating to https://YOURNETHSERVER/guacamole (https://10.0.99.177/guacamole for this demo) with the credentials listed above and navigate to the Settings from the top right hand corner drop down menu. From there select the Users tab and select New User.
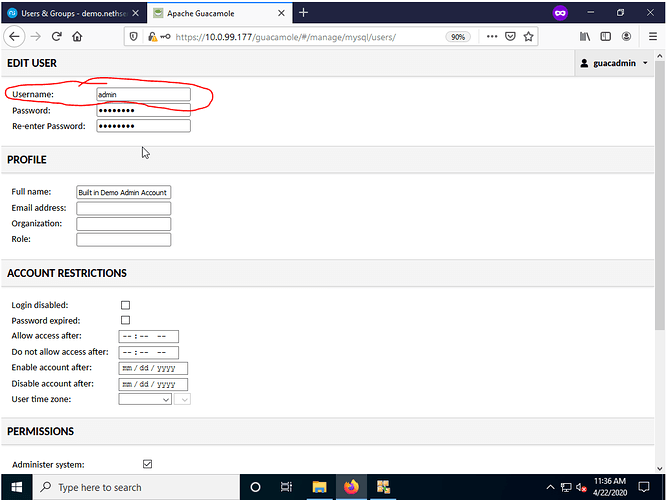
From the New User page create a new user named admin with the password Nethdemo with the appropriate permissions and select save when done . NOTE - This is the only one time SAMBA/LDAP account you must manually create. All other LDAP accounts (test1@ad.yourdomain.com for example) do NOT need to be manually entered after the initial configuration is complete.
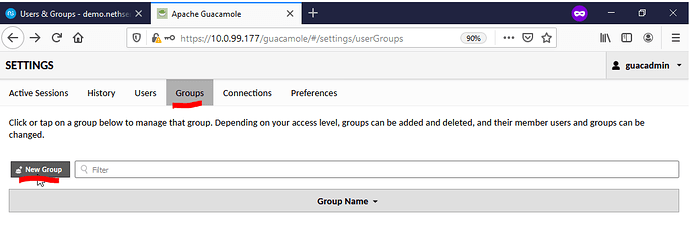
After creating the new user within Guacamole select the Groups tab within Settings and press on New Group to create a new group.
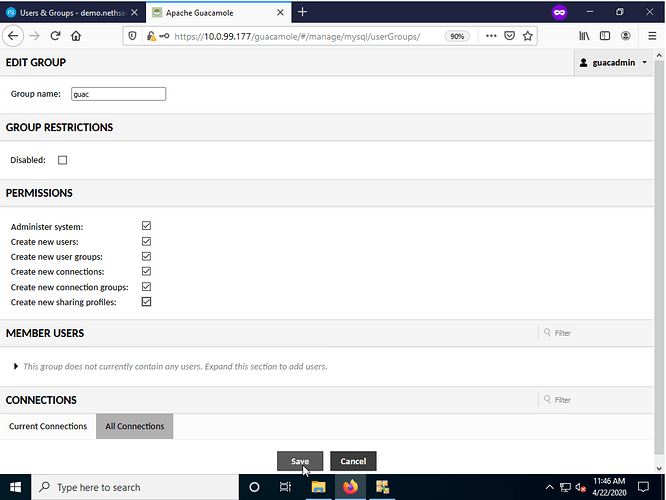
After selecting the New Group button, enter the group name and desired permissions and press save. NOTE - the group name MUST mach the group name created on the NS SAMBA4/AD AND those NS SAMBA4/AD user(s) MUST also be added as members. For this demo we created the group guac with users admin as a member while user test1 & test2 are not.
Log into Guacamole with the admin account and navigate to the Settings → Users tab. You should now see listed all LDAP users within the Users tab and all LDAP groups within the Groups tab. From this point on you can configure and control the permissions users/groups/connections have all from within the Guacamole web interface.
To-Do List
Add YouTube Video of process - Completed 3/23/2020