Has anyone looked into installing Zerotier on Neth? Though I haven’t looked into it in much detail yet, what have seen looks like an easy-to-administer VPN with some nice NAT-traversal capabilities. They’re a commercial operation with a free tier, and the free tier is probably enough for a good many users (it allows up to 100 connected devices, on any number of virtual networks). However, it’s GPL’d Free Software, and it’s apparently possible to set up your own controller for free. Looks like it could be a useful feature.
So here’s a very rough version of how to do it:
curl -s 'https://pgp.mit.edu/pks/lookup?op=get&search=0x1657198823E52A61' | gpg --import && \
if z=$(curl -s 'https://install.zerotier.com/' | gpg); then echo "$z" | sudo bash; fi
yum install https://download.key-networks.com/el7/ztncui/1/ztncui-release-1-1.noarch.rpm
yum install ztncui
config set fw_ztncui service status enabled TCPPort 3443 access green
signal-event firewall-adjust
echo 'HTTPS_PORT=3443' > /opt/key-networks/ztncui/.env
systemctl restart ztncui
Browse to https://yourserver:3443, log in with admin/password. Change the password immediately, of course.
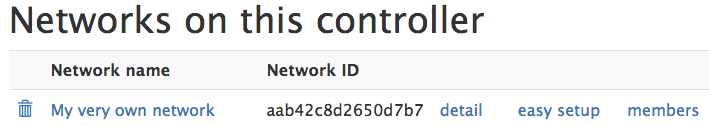
Once you’re logged in, click Add Network:
Give it a name and click Create Network:
Click Easy Setup next to your network:
Enter the network address and start/end of the pool, or just click the Generate network address button to generate them, then click Submit:
Now, from a system you want to join as a member (that already has ZeroTier installed), run
root@freenas[~]# zerotier-cli join aab42c8d2650d7b7
200 join OK
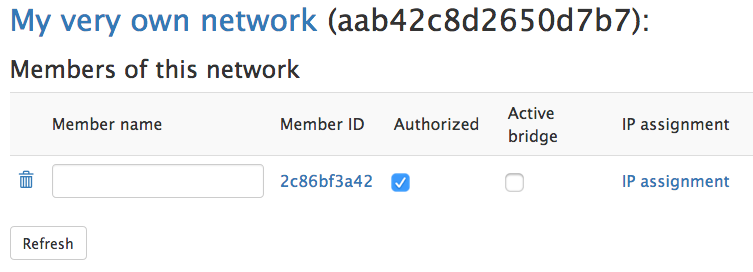
Back at the Networks page on the GUI, click Members. You’ll see your new machine listed there. Check the box for Authorized:
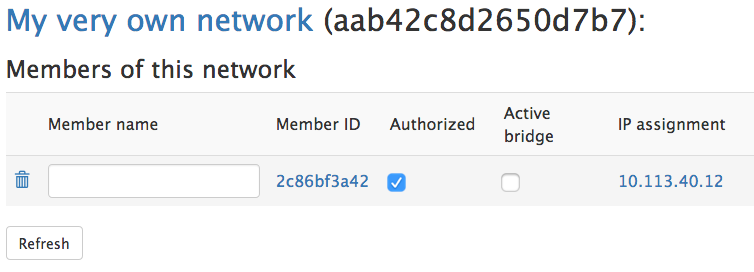
Then click Refresh. You’ll see the new IP assignment for that member. Give it a name if you like.
TODO:
- At a minimum, integrate with the system’s existing TLS certificate.
- Probably set up a reverse proxy to provide TLS termination, and to avoid the need for the special port.
Great work again! ![]() This is a nice VPN solution that supports all relevant systems.
This is a nice VPN solution that supports all relevant systems.
I successfully connected an Android mobile to a Windows PC via Nethserver controller.
The virtualhost reverse proxy works, the path reverseproxy doesn’t (missing CSS/login doesn’t work).
Yeah, I see there’s an issue about that on github. Bother.
@danb35 which zone goes for ZeroTier interface?
For the controller? The instructions above limit access to green.
Ok, did someone mention an easy VPN.
but after reading this post, and also visiting the website the information I have seems to confuse me even more.
@danb35 could kindly explain what zeroTier does in a use case scenario in an organization with many users, and with many softwares they need to login to hosted in the cloud.
That way I can get a grasp of what it actually does and how it can help.
There’s a virtual network adapter for connect the server installation to ZeroTier. This drivers should “fall” into one of network zones.
Which one?
I don’t think there is:
[root@phabricator ~]# ifconfig
dummy0: flags=195<UP,BROADCAST,RUNNING,NOARP> mtu 1500
inet 192.168.5.1 netmask 255.255.255.0 broadcast 192.168.5.255
inet6 fe80::80c6:d1ff:fe5d:e0fd prefixlen 64 scopeid 0x20<link>
ether 82:c6:d1:5d:e0:fd txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 406137 bytes 72697542 (69.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet (masked) netmask 255.255.255.0 broadcast (masked)
inet6 (masked) prefixlen 64 scopeid 0x20<link>
ether 00:50:56:3d:c7:0a txqueuelen 1000 (Ethernet)
RX packets 1153574048 bytes 72430829050 (67.4 GiB)
RX errors 0 dropped 5 overruns 0 frame 0
TX packets 4555570 bytes 6392335835 (5.9 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 228114 bytes 44421392 (42.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 228114 bytes 44421392 (42.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 192.168.3.110 netmask 255.255.255.0 destination 192.168.3.110
inet6 fe80::f2d5:9e0a:31e1:68d6 prefixlen 64 scopeid 0x20<link>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 11696 bytes 987498 (964.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 20617 bytes 27667194 (26.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@phabricator ~]#
Now, if you join your nethserver to a zerotier network (using zerotier-cli join aab42c8d2650d7b7), then at that point you’ll see a virtual network adapter:
zte6jlh34h: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 2800
inet 10.10.126.152 netmask 255.255.255.0 broadcast 10.10.126.255
inet6 fe80::a0c8:2bff:fe0a:a prefixlen 64 scopeid 0x20<link>
ether a2:c8:2b:0a:00:0a txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 8 bytes 648 (648.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
If you want it to be part of any particular zone, you’ll need to set it at the cli using db networks set....
The new interface do not appear into nethgui? Seems bad…
I don’t think the general idea is that the controller would be part of any network. And if it isn’t part of a network, there isn’t an interface to appear in the GUI. If you do decide to join the controller itself to a network, then a network is created. Why it doesn’t appear in the GUI is down to the vagaries of the GUI, though I’d expect it will show if you manually add it using db networks set zte6jlh34h ethernet role green ....
Edit: In fact, joining the controller machine to one of its networks seems to break the controller. I’m not sure if this is due to a flaw in my setup, if it’s by design, or if it’s a bug somewhere.
I’m not sure it would be useful in that scenario. The use case I see (and it sounds like there’s much more it could do, but I’m still pretty new to the system as well) is for setting up ad hoc, peer-to-peer, private networks. For one example (the one that pointed me to ZeroTier in the first place), I have a FreeNAS server that I want to back up offsite. The best way to do that is via ZFS replication, if you have a suitable target. So I put a target machine at a friend’s house. But how to connect that to my FreeNAS box?
- I could port-forward from my friend’s router to the target machine. Big security hole though, and might conflict with whatever my friend’s doing on his own network.
- I could use IPSec or OpenVPN to set up an ordinary VPN connection. The problem is that these connections are either net-to-net (giving me complete access to my friend’s LAN, and vice versa), or host-to-net (still exposing far more than necessary).
- I can create a ZeroTier network (either using this walkthrough, on my.zerotier.com, or somewhere else), and join the FreeNAS box and the target machine to it. They’re the only two members of that network, and can communicate freely on that network as needed.
The latter seems the most secure, and also the simplest to administer.
thank you @danb35 I think now I have perfect idea of the best use case scenarios for this kind of tool. ill also play around with it and post anything new or challenges.
While I recognise this is an old topic, thanks @danb35 as the controller setup still works well. I’m surprised that this hasn’t developed further. I’ve been using zerotier significantly in other areas and find it a fantastic solution.
In most cases, I’ve been using OpnSense router to set it up and get ‘vpn’ connectivity back into the local network. I’m now looking at landing direct on the NethServer and utilising AD/fileshare over zerotier.
While I have remote connectivity via Zerotier to Nethserver, with that interface in the LAN (green) zone and added as a trusted network, I still have to disable shorewall to get a response from the LAN IP and can’t get across it to other devices on the LAN.
Nethserver is in standalone server mode and I would prefer to keep that as opposed to running a gateway.
It would be nice to have a GUI capability to ‘bridge’/route between the LAN and Zerotier defined network (or am I missing something and it should be occurring). Has anyone progressed with or looked at further integration via cockpit etc? Personally, I see it as a better VPN solution than other offerings - and even better having your own controller as setup here.
Klaus.
whats progress on this.
had posted this Distributed Hosting and Networks - Community - NethServer Community only to realise it had been mentioned earlier on
I haven’t worked further on it–the target device I was intending to use wasn’t very easy to get working with ZFS, and Zerotier support has been removed from FreeNAS/TrueNAS in the interim. But it should be straightforward enough to set up a virtual host-based reverse proxy through the GUI, which would address both of these issues.
seems this error was resolved. anyone checked?