@pauldiggsjazz
Hi Paul
And Welcome to the NethServer Community!
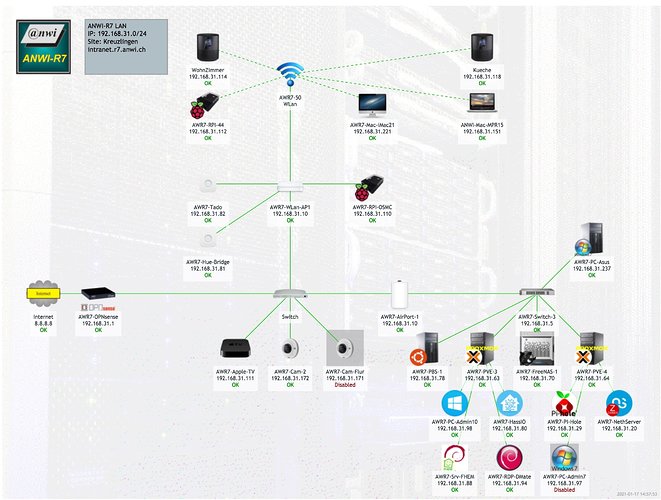
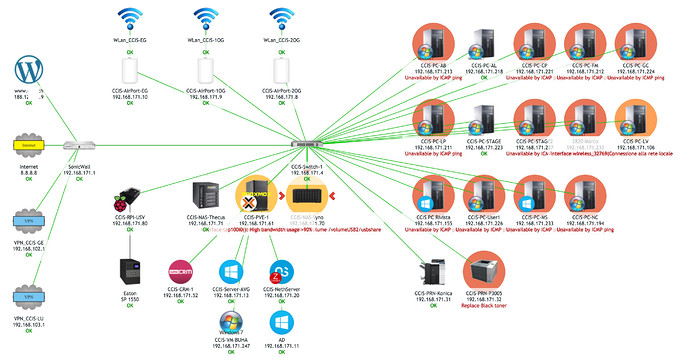
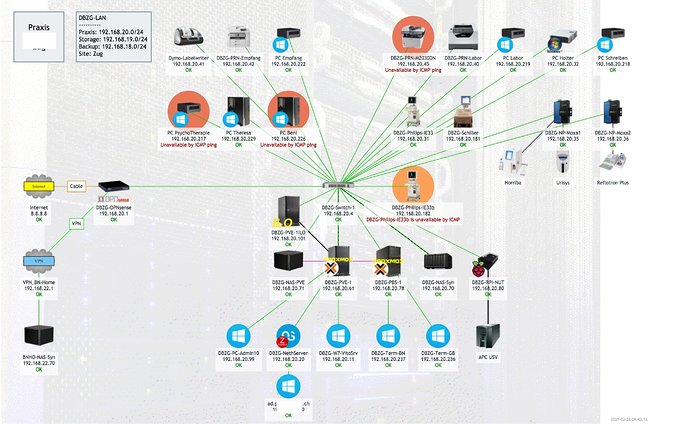
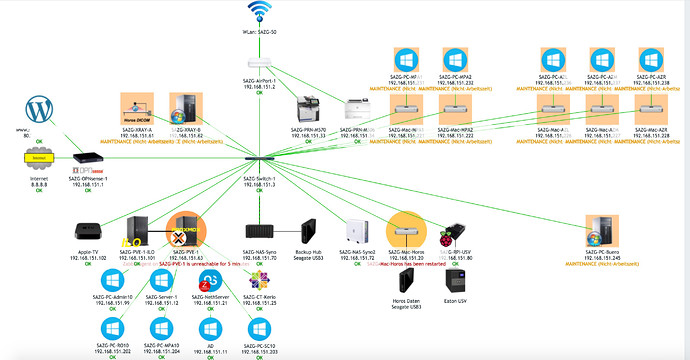
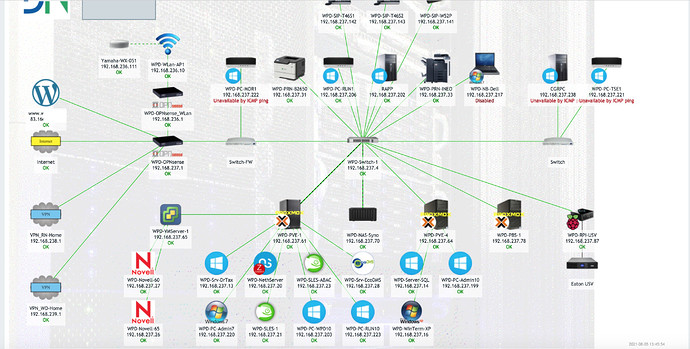
I’m using the combination OPNsense (hardware) + NethServer (VM) + Proxmox (Hypervisor) - and for some larger clients started using PBS Proxmox Backup Server.
All my clients only run virtualized servers, something I’d strongly suggest for you. You get so much more features - not all you might need, but the bottom line is much better availability. Features like Live Backups (NethServer does it’s Backups, Proxmox does its…), but also fast Snapshots (Nice before a critical upgrade)… Sensational fast disaster recovery! Proxmox is as free as NethServer & OPNsense.
Nowadays, most people suggest using VMs for server, and I can confirm this. No Hardware dependencies! And 5 years NO issues!
Among my clients there’s also a law office using the above setup - and a Windows “Member Server” for their law “software”…
Now to your original question:
OpenVPN on OPNsense or NethServer?
I’d suggest using OpenVPN on OPNsense! Mind you, during tests I have confirmed that NethServer’s OpenVPN implementation is rock solid, but as you, My clients and I prefer that running on the gateway / firewall, and my clients also want a dedicated box for this. Maybe swiss mentality? But It works great!
NethServer profits from the - in my Opinion - best communities in OpenSource! Plenty of know-how and good will amassed here - enough to tackle almost ANY problem, not necessarily NethServer related!
And, as you, I also used SME for around 10+ years - before switching to NethServer! Never regretted the move!
I’d strongly suggest using LetsEncrypt for correct SSL, something which will give you much less headaches with Mail-Clients, but also NethServer / NextCloud. Almost anything web-available nowadays NEED SSL. Mail will often NOT work (Outlook!) with a custom certificate (Self generated incl. CA)…
Lets Encrypt is free and works well on NethServer (Or OPNsense).
My 2 cents
Andy