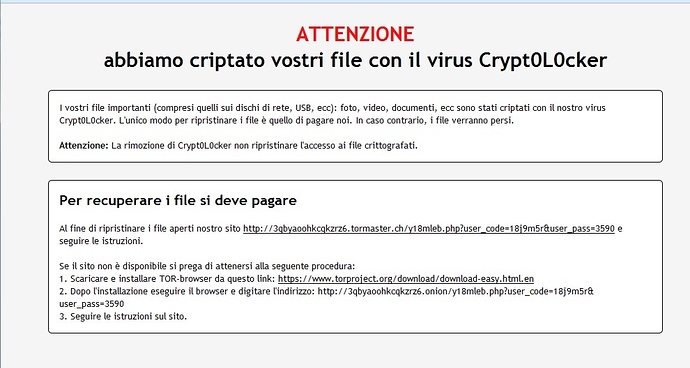
Help or took me to a virus that encrypted files I had in Samba are all crepitati
How can I recover the files or inside the Nethserver server?
If you were to delete the folders that are infected are sure it will not cause damage to some high inside the servers?
How can I fix the problem ?
All files contain the following files that I enclose
Unfortunately you cannot do anything.
Attention! Can encrypt all shared files or folders!
There is no way to decrypt if you have not the key.
Only a good AV set to the highest level of protection can prevent infection and encryption.
After encryption, the virus destroy itself and no AV cannot detect anything.
https://www.pcrisk.com/removal-guides/8930-crypt0l0cker-virus
EDIT (I don’t know if it works):
http://www.2-remove-virus.com/remove-crypt0l0cker/
EDIT 2:
As @GG_jr said, for now there is no way to decrypt the files without the key.
If you decide to keep a copy of the encrypted files, a good place to look for future solutions is BleepingComputer.
This is my guess…
Affected files:
- Files on the infected computer
- Files on shared folders
- Files on network drives
Most likely (non-shared) NethServer files were unaffected.
In general terms, possible ways to recover the files are:
- Restore files from recent backups, if any (prefered method).
- If a file cloud service was in use (owncloud, dropbox…), recover files from recent file versions (shared files might not be included).
- If filesystem snapshots were in use, recover files from them.
- Recover computer’s files from shadow copies:
- The ransomware deletes shadow file copies, but If the infected computer was shutdown in the middle of the encryption process, there is a small chance for recovery (after removing the ransomware).
- This might not be the case for network drives and shared folders, where shadow copies are usually not in use.
Sadly, chances are low 
Hi. I had cryptolocker on many customers PCs. There was no way to restore files. Sorry.
As solution for secure backup I started using Seafile (or OwnCloud). I think AV is not enought, because first is virus and then is antivirus, so you have a change to get virus anyway. Personal cloud is better way. And I don’t trust big companies, so I use my own cloud Seafile.
Back up your files and one-click restore.
BTW,I just found that this article (LINK REMOVED) might give you some instruction. Hope this helps!
Did you actually read their instructions:
Right click on Taskbar and click Start Task Manager
Click any suspicious process, and then click End Process (No suggestions given)
Type regedit and click OK.
Search and delete all malicious keys of Cryptolocker Virus in all folders (Again no suggestions given)
Although they do offer a download of their “Automatic Virus Removal Tool”. Probably better known as Cryptolocker-2. ![]()
Cheers.
Ehi Danny, welcome aboard!
I think that a better solution might be a good backup module for workstation like urbackup
Forgive me for reviving this thread. 
@k1000, if you couldn’t retrieve the files but kept a bakcup of the encrypted ones, you may contact Dr. Web, as they are able to decrypt some versions of this Ransomware, at least they do from some weeks/months ago.
This again proves why we should disable SMBv1 
@alefattorini i REAAALLYYY urge, or beg you to look into this!
We will see more issues like this, with these recent NSA hacks becoming public.
you’d really take a deep breath and relax… samba is already patched, your issue is with windows… and if a windows client is vulnerable, all shares on lan (where the connected user has write permission) are vulnerable…
this is how samba works…
samba is not vulnerable by server to server virus spreading
Depending on what version you got infected with (look at the extension), you can try to recover with those tools:
https://www.nomoreransom.org/decryption-tools.html
or
https://www.symantec.com/connect/articles/recovering-ransomlocked-files-using-built-windows-tools
If i would be you i would actually try to make sure you got rid of the infection, by finding the pc that got infected in the first place, and make sure i block the path it used. Here are the steps that are usually a good best practice:
-
Find the virus: Apart from the recent wannacy ransomware, which is using windows vulnerability and spreads through port 445, 80% of the infection arrives through a mail, where someone clicks on a fake pdf or an excel/word doc with macro, and the infection is done. If you find this file, i would urge to submit it to any of the major AV company to have a definition against it. Also you can check on virustotlal.com, to see if any AV company does have protection against it already, and then use their trial version to scan your environment.
-
The best way is to prevent those to come into your environment in the first place. Ransomware normally contacts a remote server once an infection took place, to get further keys which is used for encrypting. A decent IPS/IDS could potentially block that traffic, so installing suricata from the software center could be your friend.
-
Configure you Mailserver properly, as it is the main gateway into your environment for ransomware. Even if you dont install any AV software that integrates into your mailserver, try to block common extensions that have totally nothing todo in a mail: .exe, .js etc…
-
As many said before, use a good backup is critical
-
Harden your endpoints and restrict user access to remote share
Here are some good tips from security experts:
Hardening Your Environment Against Ransomware
https://www.symantec.com/connect/articles/hardening-your-environment-against-ransomware
Good luck