While Checking Out the latest Release Notes for Termix,
i saw that it now had support for WarpGate warp-tech/warpgate: Fully transparent SSH, HTTPS, MySQL and Postgres bastion/PAM that doesn’t need additional client-side software Which i decided to CheckOut.
WarpGate is a The last bastion. of Secure access / PAM for your internal SSH, HTTPS, MySQL and Postgres servers with SSO and RBAC.
No client apps needed.
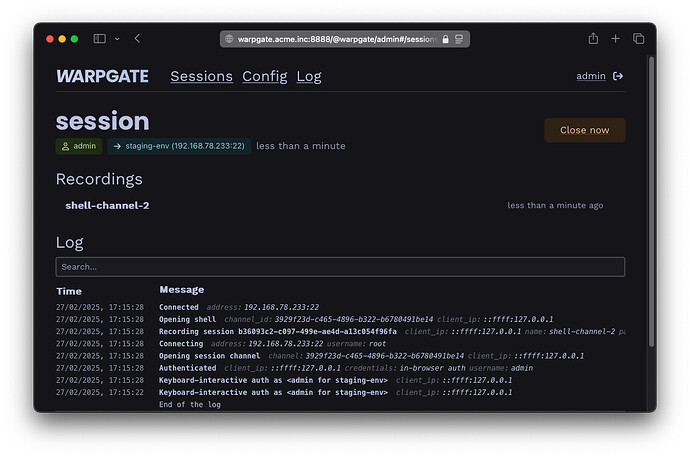
Warpgate directly exposes native SSH, HTTPS, MySQL and Postgres listeners, handling Authentication, and then transparently forwards the connection to the target server, while making a live recording for auditing.
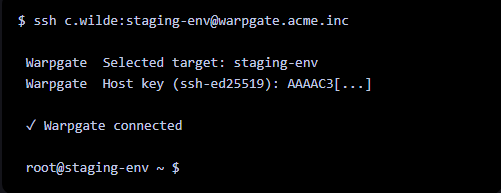
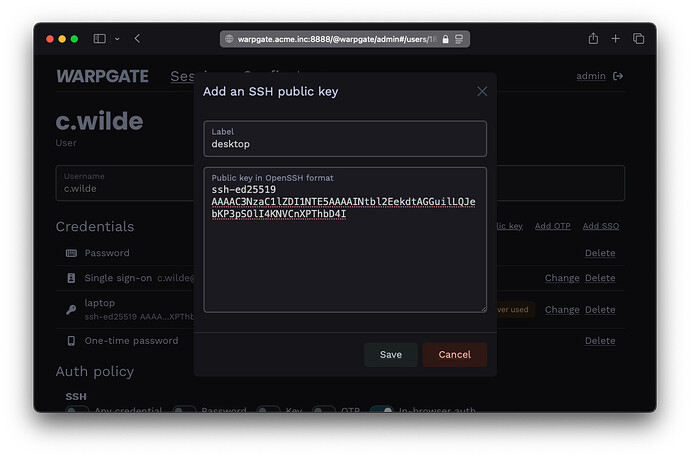
You can Then Conect to the target server, using specialised User credentials
After configuring, the host server, and ssh
It Even Allows you to use OIDC SSO, for Authentication, meaning you can use any SSO solution, to connect to your servers internally, and offers Audit trail (Authentik supports this natively tough)
It Should be possible to Implement this in NEthserver 8, through simplified compose file
services:
warpgate:
image: ghcr.io/warp-tech/warpgate
ports:
- 2222:2222
- 8888:8888
- 33306:33306
volumes:
- ./data:/data
stdin_open: true
tty: true
Then you Would be able to provide even more security, if connecting directly via ssh, or termix, or any other ssh client.
Here are the Nifty Docs for the same Docker - Warpgate