After Attempting a Migration into Nethserver 8 hee: Nethserve r7 to Ns8 Migration, With external AD - Support - NethServer Community
And failing to achieve the same due to not being able to connect to my NS7 AD instance from NS8, i resolved to migrate the Entire AD to NS8. then All other NS7 servers currently running other soluitons as well.
The problem was, I am using LLNG for SSO user Authentication, and because of this, Migrating the Entire AD seemed like an unlikely choice.
I opted to Build an SSO Module, Based on Authentik
- This would allow me to Deploy a New NS8 instance that would serve as the AD server.
- MIgrate my AD to the new NS8 instance
- Install the SSO module, connect all apps i am using SSO with to the new SSO platform,
- Migrate the other NS7 Instances to NS8 with being connected to the
Why Authentik? Because from face value, it seemed like an easy Implementation, and Boy was i Wrong.
HEre is the Module Repo: compgeniuses/ns8-goauthentik: NEthserver 8 Module for authetik goauthentik.io (github.com)
There are 2 Branches Mainly: main AND certgen
Each can be installed via
for main
add-module ghcr.io/compgeniuses/goauthentik:main 1
AND
for certgen
add-module ghcr.io/compgeniuses/goauthentik:certgen 1
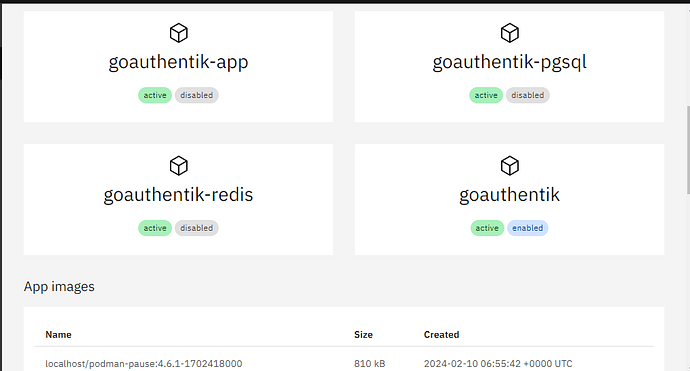
From the MAin branch, the module install correctly, configures and even starts all the services,
Accessing the url of the configured modules, gives me a bad gateway error.
Digging through the logs, I couldn’t help but notice the following error persisting.
2024-02-10T09:57:49+03:00 [1:goauthentik10:goauthentik-app] {"app_name": "authentik.crypto", "event": "Failed to run reconcile", "exc": "ProgrammingError('relation \"authentik_crypto_certificatekeypair\" does not exist\\nLINE 1: ...hentik_crypto_certificatekeypair\".\"key_data\" FROM \"authentik...\\n ^')", "level": "warning", "logger": "authentik.blueprints.apps", "name": "managed_jwt_cert", "pid": 2, "timestamp": "2024-02-10T06:57:49.610196"}
2024-02-10T09:57:49+03:00 [1:goauthentik10:goauthentik-pgsql] 2024-02-10 06:57:49.612 UTC [24] ERROR: relation "authentik_crypto_certificatekeypair" does not exist at character 22
2024-02-10T09:57:49+03:00 [1:goauthentik10:goauthentik-pgsql] 2024-02-10 06:57:49.612 UTC [24] STATEMENT: SELECT 1 AS "a" FROM "authentik_crypto_certificatekeypair" WHERE "authentik_crypto_certificatekeypair"."name" = 'authentik Self-signed Certificate' LIMIT 1
2024-02-10T09:57:49+03:00 [1:goauthentik10:goauthentik-pgsql] 2024-02-10 06:57:49.657 UTC [24] ERROR: relation "authentik_outposts_outpost" does not exist at character 257
2024-02-10T09:57:49+03:00 [1:goauthentik10:goauthentik-app] {"app_name": "authentik.outposts", "event": "Failed to run reconcile", "exc": "ProgrammingError('relation \"authentik_outposts_outpost\" does not exist\\nLINE 1: ..._id\", \"authentik_outposts_outpost\".\"_config\" FROM \"authentik...\\n ^')", "level": "warning", "logger": "authentik.blueprints.apps", "name": "embedded_outpost", "pid": 2, "timestamp": "2024-02-10T06:57:49.657862"}
After reading Some documentations on Authentik, I notice i am supposed to provide some certificates.
THis is what PRompted me to Implement a Second branch, that Implements the certificate generation, as well as Importing the certificates into authentik using the ak commands.
After numerous varied attemtps, i kept getting this error in logs
2024-02-10T10:19:39+03:00 [1:goauthentik11:goauthentik-app] {"event": "Enabled authentik enterprise", "level": "info", "logger": "authentik.lib.config", "timestamp": 1707549579.569877}
2024-02-10T10:19:42+03:00 [1:goauthentik11:goauthentik-app] {"event": "Loaded GeoIP database", "last_write": 1706549214.0, "level": "info", "logger": "authentik.events.geo", "pid": 2, "timestamp": "2024-02-10T07:19:42.131885"}
2024-02-10T10:19:43+03:00 [1:goauthentik11:goauthentik-pgsql] 2024-02-10 07:19:43.704 UTC [24] ERROR: relation "authentik_crypto_certificatekeypair" does not exist at character 367
2024-02-10T10:19:43+03:00 [1:goauthentik11:goauthentik-pgsql] 2024-02-10 07:19:43.712 UTC [24] ERROR: relation "authentik_crypto_certificatekeypair" does not exist at character 22
2024-02-10T10:19:43+03:00 [1:goauthentik11:goauthentik-pgsql] 2024-02-10 07:19:43.712 UTC [24] STATEMENT: SELECT 1 AS "a" FROM "authentik_crypto_certificatekeypair" WHERE "authentik_crypto_certificatekeypair"."name" = 'authentik Self-signed Certificate' LIMIT 1
2024-02-10T10:19:43+03:00 [1:goauthentik11:goauthentik-app] {"app_name": "authentik.crypto", "event": "Failed to run reconcile", "exc": "ProgrammingError('relation \"authentik_crypto_certificatekeypair\" does not exist\\nLINE 1: SELECT 1 AS \"a\" FROM \"authentik_crypto_certificatekeypair\" W...\\n ^')", "level": "warning", "logger": "authentik.blueprints.apps", "name": "self_signed", "pid": 2, "timestamp": "2024-02-10T07:19:43.712874"}
2024-02-10T10:19:43+03:00 [1:goauthentik11:goauthentik-pgsql] 2024-02-10 07:19:43.787 UTC [24] ERROR: relation "authentik_outposts_outpost" does not exist at character 257
2024-02-10T10:19:43+03:00 [1:goauthentik11:goauthentik-pgsql] 2024-02-10 07:19:43.787 UTC [24] STATEMENT: SELECT "authentik_outposts_outpost"."managed", "authentik_outposts_outpost"."uuid", "authentik_outposts_outpost"."name", "authentik_outposts_outpost"."type", "authentik_outposts_outpost"."service_connection_id", "authentik_outposts_outpost"."_config" FROM "authentik_outposts_outpost" WHERE ("authentik_outposts_outpost"."managed" = '' AND "authentik_outposts_outpost"."name" = 'authentik Embedded Outpost') ORDER BY "authentik_outposts_outpost"."uuid" ASC LIMIT 1
At the moment, I have no idea on how to resolve the errors and issues being faced, and how to geth the said product to work as a NS8 Module
I would be Happy to take an PR that resolves the errors in the module, but at the moment, ill just leave it at that with tag (not Enough Experience)
IF anyone in @dev_team would be willing to take a look, i would be glad.But as it is, Back to Square 1