Hello everybody,
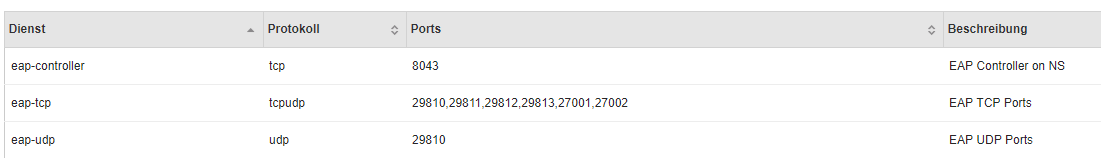
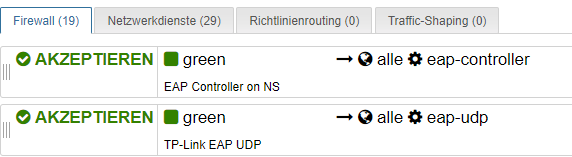
in my company adopt TP-link EAP access point (model: EAP225 - EAP110 - EAP120) for distribuite tagged network wifi (Principal, Guest, Admin, PLC, Voip).
a few simple steps to follow
wget https://static.tp-link.com/resources/software/EAP_Controller_v2.5.3_linux_x64.tar.gz
tar -zxvf EAP_Controller_v2.5.3_linux_x64.tar.gz
cd EAP_Controller_v2.5.3_linux_x64
./install.sh
[root@proxy EAP_Controller_v2.5.3_linux_x64]# ./install.sh
EAP Controller will be installed in [/opt/tplink/EAPController] (y/n): y
========================
Installation start ...
Install succeeded!
========================
EAP Controller will start up with system boot. You can also control it by [/usr/bin/tpeap].
Starting EAP Controller .........................
Start successfully.
You can browse URL http://127.0.0.1:8088 for more.
========================
[root@proxy EAP_Controller_v2.5.3_linux_x64]#
mkdir -p /etc/e-smith/db/configuration/defaults/tpeap
echo "service" > /etc/e-smith/db/configuration/defaults/tpeap/type
echo "enabled" > /etc/e-smith/db/configuration/defaults/tpeap/status
config set tpeap service status enabled
signal-event runlevel-adjust
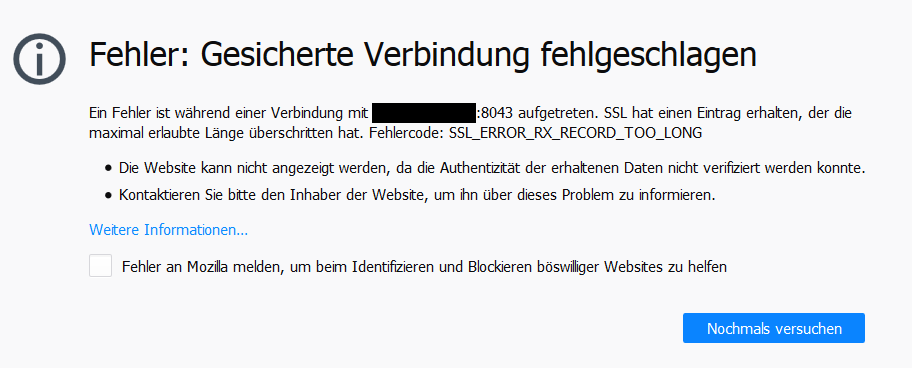
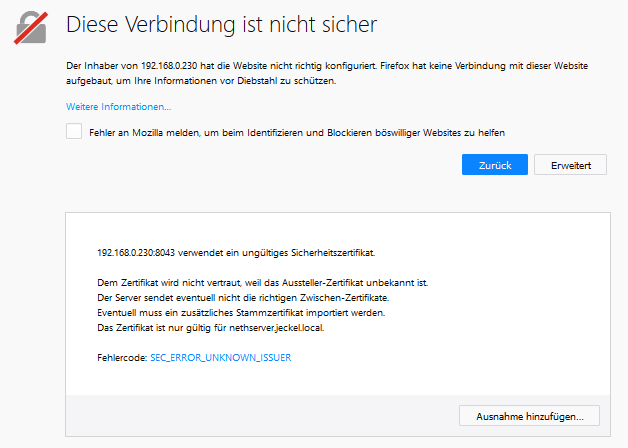
The server listen on https://0.0.0.0:8043.
I have try to proxy request via https server Letsencrypt certificate, like @mrmarkuz on Howto install guacamole, but without subfolder there are problem with redirect.