We are happy to announce that Threat shield  has been empowered with DNS blacklist
has been empowered with DNS blacklist  .
.
Thanks to @giacomo and @edoardo_spadoni for the great work 
DNS blacklist
Threat shield already protects your NethServer by blocking all connections from/towards malicious IP addresses… From now on you can add and extra layer of protection by blocking DNS requests to malicious domains.
DNS blacklist is implemented as a DNS sinkhole and uses Pi-Hole FTLDNS under the hood. All DNS requests are redirected to the DNS sinkhole that, in case of malicious domain, returns 0.0.0.0 instead of the real IP address associated to the domain.
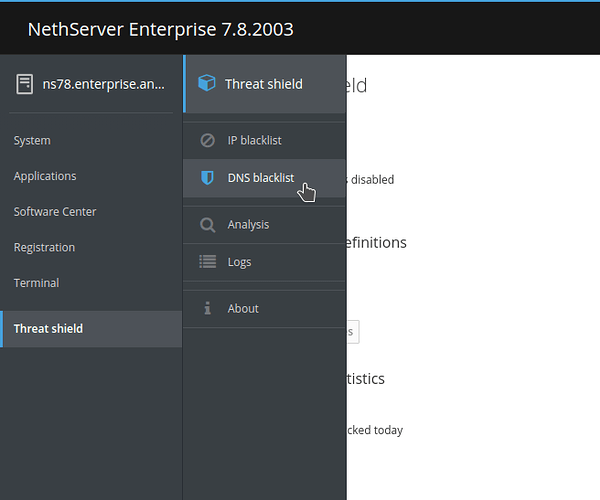
Threat shield Cockpit application has been refactored to include the new feature. The old Settings page is now called IP blacklist, and a new page DNS blacklist has been added to the menu:
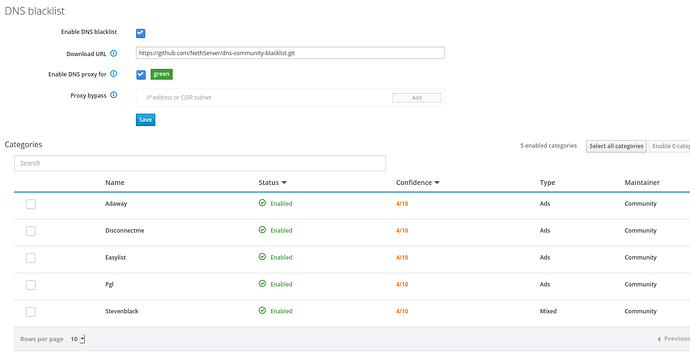
For the sake of simplicity, the new DNS blacklist page looks a lot like IP blacklist page:
You have UI controls to:
- Enable the blacklist
- Set the GIT URL where blacklisted domains and blacklist categories will be downloaded from (more info below)
- Set the network zones where DNS blacklist is enabled
- Allow certain hosts or CIDR subnets to bypass DNS proxy
At the bottom of the page you can choose which categories of domains should be blocked. The list of categories is retrieved by the GIT repository set in Download URL.
Dashboard
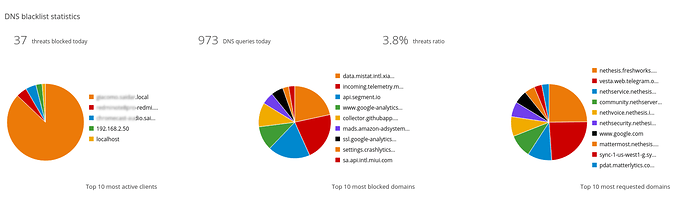
Dashboard page now provides an overview on current status of IP and DNS blacklists and displays graphical information about blocked attacks. DNS blacklist statistics provides:
- Today’s total number of threats blocked
- Today’s total number of DNS requests
- Today’s threats percentage
- Top 10 clients performing most DNS requests
- Top 10 blocked domains
- Top 10 requested domains
Analysis
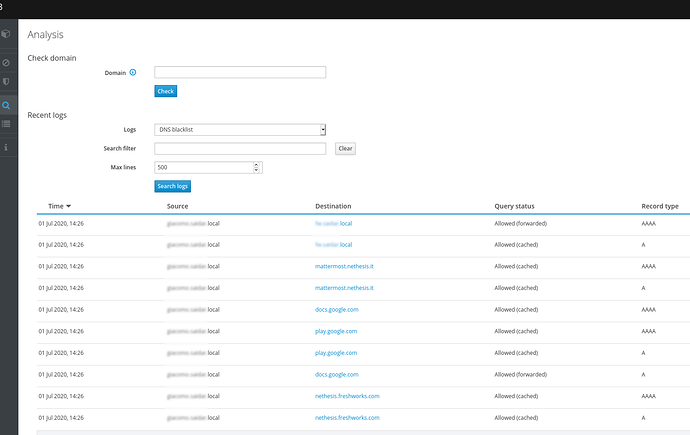
Analysis page has been redesigned to allow you to analyze both IP and DNS blacklist activity, providing:
- prettified logs about blocked IP connections or DNS requests
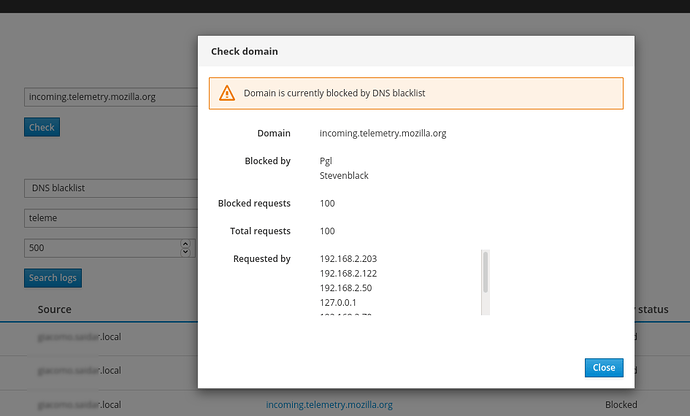
- a tool to check if a domain or an IP address is currently blocked by IP or DNS blacklist
Logs
You can access DNS blacklist raw logs accessing Logs page and selecting /var/log/pihole-FTL.log
DNS blacklist repository
The set of malicious domains is retrieved from a GIT repository. This repository is organized in one or more .dns files, and each of them represents a blacklist category.
A category file includes:
- a list of malicious domains (one per line)
- meta-data about the blacklist category, such as the name of the maintainer, the type of domains listed (e.g. ads, malware, …) and the level of confidence (an estimate of false-positives frequency)
NethServer Community users can use (and possibly maintain  ) this URL: https://github.com/NethServer/dns-community-blacklist.
) this URL: https://github.com/NethServer/dns-community-blacklist.
NethServer Enterprise users have access to highly reliable professional-grade DNS blacklists provided by Yoroi.
How to install
Threat shield with DNS blacklist feature is available in nethserver-testing repository:
yum install --enablerepo=nethserver-testing nethserver-blacklist
Try it and let us know what you think about it, any feedback is welcome!