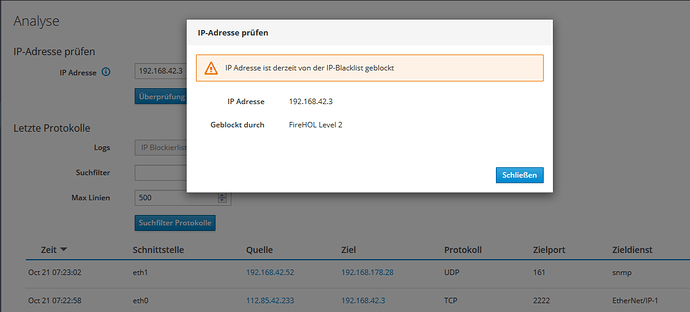
The internal network is 192.168.42.0/24. If I check any address from this internal network, ThreadShield says it is blocked Is this correct? Shouldn’t the internal addresses be excluded from blocking? Do I have to add the internal network to the whitelist (or at least the internal servers which have ports forwarded to them)?
The tools just searches the given IP inside the lists.
You should ask the maintainer of the lists why that CIDR is inside the geoblocklist 
1 Like
@carsten I can’t reproduce your issue.
My test system has FireHOL Level 2 enabled in Threat shield and 192.168.42.3 is not blocked.
This is very strange, let’s check the date of the file:
[root@ns7-ent ~]# ls -l /usr/share/nethserver-blacklist/ipsets/firehol_level2.netset
-rw-r--r-- 1 root root 308610 Oct 22 21:41 /usr/share/nethserver-blacklist/ipsets/firehol_level2.netset
You can also look inside the file and search for 192.168.
To force download, press the Check for updates button in the dashboard.
To debug run: sh -x /usr/share/nethserver-blacklist/download ipsets
2 Likes