Hello guys!
I’m back after a while in this amazing place!
I don’t know for how many time, but now I’m happy to be here again with you.
I’m running two Nethserver (6.9) installation (one as firewall role and the other as fileserver for the network) and I’m stubled in the same issue presented by @Carlos_Estrada.
I’ve followed the gread suggestions gives by @filippo_carletti, @giacomo, @enzoturri and @douglasdiasn in the thread and I’ve made the following steps without solving the problem.
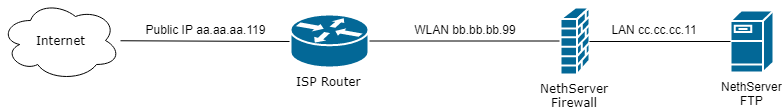
This is the diagram of my network.
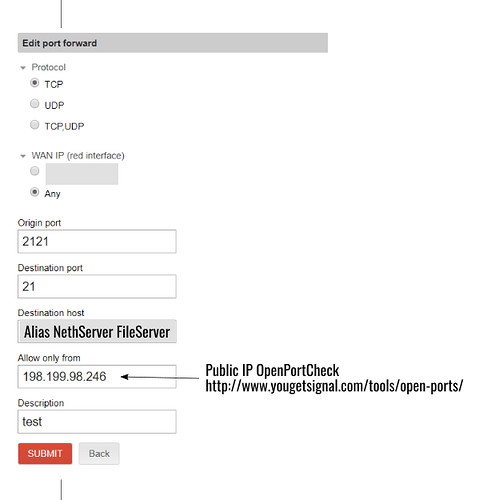
In the Nethserver Firewall I’ve cofigurated this Port Forwarding Rule
Namely: the port forwording of the 2121 public port to the 21 port of the FileServer (configurated with ftp enabled)
Then, before starting the check via yougetsignal.com tool, I’ve open three console for monitoring the connection:
-
One console on the firewall with tcpdump listening on port 2121
[root@fw ~]# tcpdump -i eth1 'port 2121'
-
Another console on the firewall monitoring firewall.log
[root@fw ~]# tail -f /var/log/firewall.log | grep DPT=2121
-
A console on fileserver with tcpdump listening on the standard ftp port
[root@fileserver ~]# tcpdump -i eth0 'port 21'
Well… the result is that:
- I see the tcp traffic on the firewall port 2121, this is a part of the log
16:41:26.765800 IP 198.199.98.246.45482 > bb.bb.bb.99.scientia-ssdb: Flags [S], seq 2146193354, win 14600, options [mss 1440,sackOK,TS val 4245816580 ecr 0,nop,wscale 8], length 0 16:41:27.763137 IP 198.199.98.246.45482 > bb.bb.bb.99.scientia-ssdb: Flags [S], seq 2146193354, win 14600, options [mss 1440,sackOK,TS val 4245816830 ecr 0,nop,wscale 8], length 0 16:41:27.764842 IP 198.199.98.246.45486 > bb.bb.bb.99.scientia-ssdb: Flags [S], seq 2210218090, win 14600, options [mss 1440,sackOK,TS val 4245816830 ecr 0,nop,wscale 8], length 0 16:41:28.762467 IP 198.199.98.246.45486 > bb.bb.bb.99.scientia-ssdb: Flags [S], seq 2210218090, win 14600, options [mss 1440,sackOK,TS val 4245817080 ecr 0,nop,wscale 8], length 0
-
The firewall doesn’t log any DROP action in the firewall.log (at this point I suppose to see some kind on traffic on the tcpdump on the FileServer…) 
-
The tcpdump command on port 21 of the server doesn’t log nothing! (Damn!) 
And the result of the public port testing tool is that the port is closed…
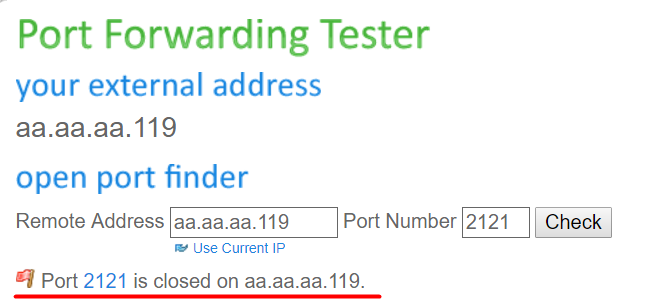
Supposing that this is the way to check the path of the port forwarding connection… I haven’t solved the problem, but I hope in your help to find where is the issue.
Thank you in advance