Tried all the VMWare images and unfortunately could not get any of the work correctly. Here are the results I found:
Alma: Boots, then the stops during the boot process with:
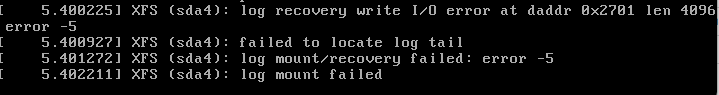
Centos: Boot halts with: Probing EDD (edd=off to disable)
Researching this it can be fixed by adding “edd=off” at the boot. However, running in VMWare I can’t get to the console in the split second needed to interrupt the boot process.
Debian: This one boots to completion. At this point trying to connect via a browser gives ‘ERR_CONNECTION_REFUSED’. The server does respond to a ping.
Trying to login via a console was also problematic. It didn’t accept the admin/Nethesis,1234 combination. It did accept root/Nethesis,1234 and then immediately asked to change the password. Except after giving the old/new/new passwords it took me back to a login where it would only accept root/Nethesis,1234 again and asking me to change it again. Wash, rinse, repeat.
Rocky: This also stopped at the Probing EDD.
There was one other quirk I noticed, but this might be VMWare playing up. I could add any of the images to a profile and save it, but then any additional attempts to edit the profile failed, saying it couldn’t find the disk. So every time I needed to edit, I had to delete the disk, save, and the add again along with the change I was trying to make.
You might add a comment to the Images section to let folks know they are all IDE based. Or better still, provide OVF or OVA files.
Cheers.