Hi,
This package provides integration for FreeRADIUS in NethServer. It turns your server into a centralized network authentication server, so you can easily control what devices can access the network. The authentication server is prepared to control network access using MAC address, IEEE802.1X or both.
The authentication server provided by this package is only one component of the three elements a RADIUS infrastructure is made of. The other two elements (the authenticator and the supplicant) are not configured by this package. That is something you must do first, before you can enjoy a successful RADIUS infrastructure.
Web Integration
Development
- https://github.com/areguera/nethserver-7-freeradius
- https://github.com/areguera/nethserver-6-freeradius
Installation
To install nethserver-freeradius package, run the following command (as the root user):
yum --enablerepo=nethforge-testing install nethserver-freeradius
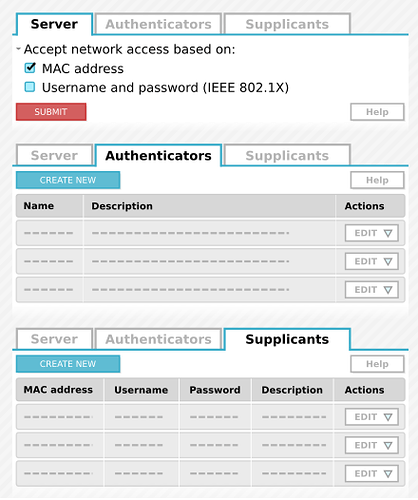
After installation look for “FreeRADIUS” panel in the “Configuration” section of NethServer web interface. It should provide three tabs named “Authentication Server”, “Authenticators”, and “Supplicants”.
Configuration
In normal operation, the system administrator does the following:
-
Use the authentication server tab in FreeRADIUS panel to configure how authenticators will allow supplicants to access the network. Possible options include MAC address, IEEE802.1X or a combination of them both. See
/etc/raddb/sites-available/defaultfile. -
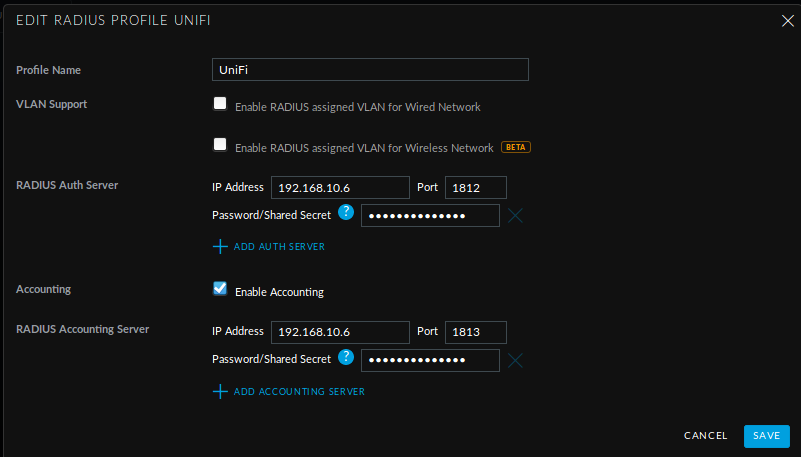
Use the authenticator tab in FreeRADIUS panel to define what authenticator devices (e.g., access points, smart switches) can send access requests to the authentication server. See
/etc/raddb/clients.conffile. -
Use the supplicants tab in FreeRADIUS panel to define the MAC address and credentials (i.e., username and password) final users must set in their devices (e.g., wireless stations) to access the network. See
/etc/raddb/authorized_macsand/etc/raddb/usersfiles.
In addition to these basic steps, the system administrator might also do the following:
-
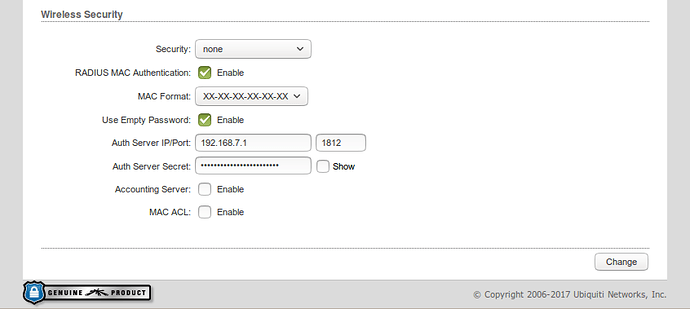
Configure authenticator devices (e.g., access points, smart switches) as authenticator of the authentication server (i.e., to accept authentication requests from supplicants and request access to the centralized authentication server based on them).
-
Configure supplicant devices (e.g., wireless stations) to send authentication requests to authenticator devices.
-
Communicate final users (e.g., using a sealed letter) the credentials they must use in order to access the network.
The configuration of authenticator and supplicant devices is specific to each of them. Here is how to configure specific authenticator and supplicant devices to work with nethserver-freeradius integration module:
Use Case
This package might be useful for system administrators needing to control the network access of its users as well as provide mobility to them. For example, consider local wireless communities made of NanoStation devices in which one line of these devices is configured as access points and the rest of them as client stations. The access points, here, are configured as authenticators of a central authentication server (running nethserver-freeradius). The client stations (supplicants) are configured to send access requests to the authenticators using IEEE802.1X.
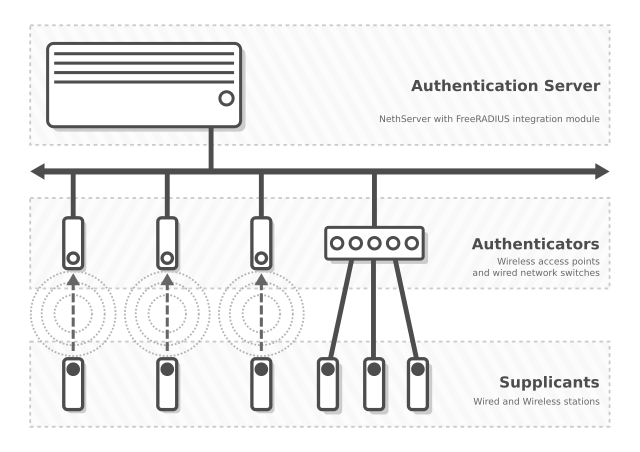
In this infrastructure:
-
The supplicant sends an Access-Request to the authenticator it connects to, using IEEE802.1X (e.g., EAP-MD5 or EAP-TTLS). The Access-Request includes the supplicant’s MAC address as well as the “User-Name” and “User-Password” attributes.
-
The authenticator sends the Access-Request to the centralized authentication server.
-
The authentication server decides whether or not to accept the supplicant Access-Request and responds to the authenticator accordingly.
-
The authenticator enforces the authentication server decision to supplicant.
Cheers,