LAM (LDAP Account Manager) is an LDAP management user interface, similar to phpLDAPadmin. I configured it to manage my local Samba4 AD accounts provider.
Note: I installed also Roundcube, some PHP dependencies could be pulled by it.
-1- Download the Fedora/CentOS RPM from https://www.ldap-account-manager.org/lamcms/releases
-2- Install the RPM
yum localinstall ldap-account-manager-5.6-0.fedora.1.noarch.rpm
-3- Go to https://<serverip>/lam, click on LAM configuration
-4- Click “Edit server profiles”, the default password is lam
-5- In a shell type the following command to get the current NethServer setup:
[root@vm5 ~]# account-provider-test dump
{
"startTls" : "",
"bindUser" : "VM5$",
"userDN" : "dc=dpnet,dc=nethesis,dc=it",
"port" : 636,
"isAD" : "1",
"host" : "dpnet.nethesis.it",
"groupDN" : "dc=dpnet,dc=nethesis,dc=it",
"isLdap" : "",
"ldapURI" : "ldaps://dpnet.nethesis.it",
"baseDN" : "dc=dpnet,dc=nethesis,dc=it",
"bindPassword" : "secret",
"bindDN" : "DPNET\\VM5$"
}
-6.a- Copy the values above in the server profile form
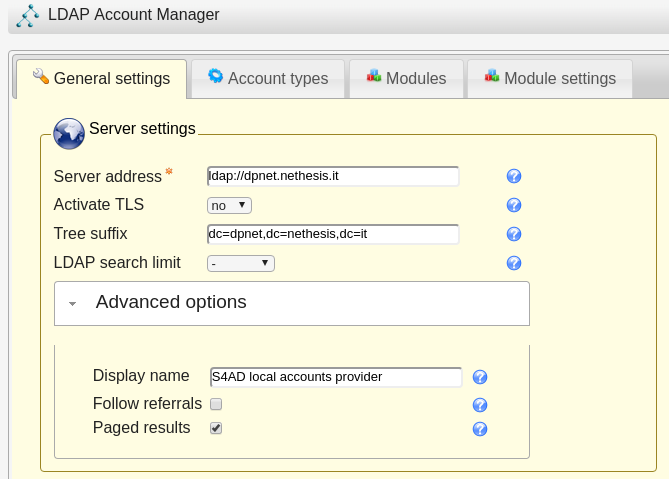
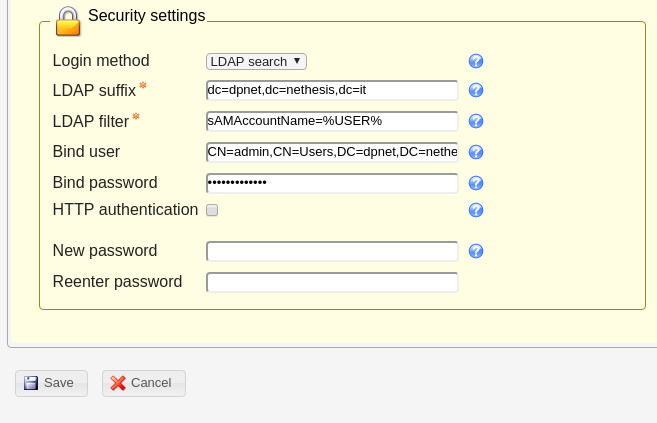
-6.b- Scroll down, fill security settings and save
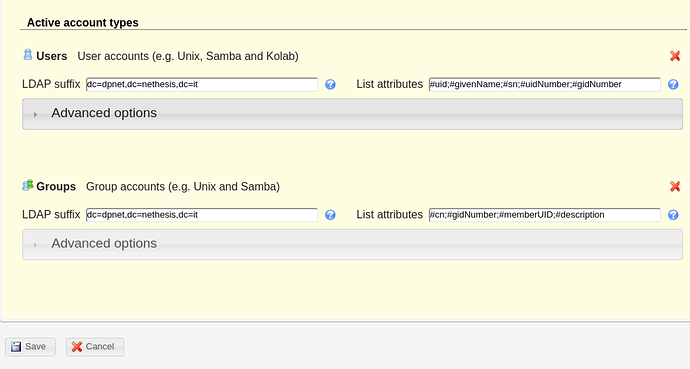
-7.a- Go to “Account types” tab, and fill the form like the following screenshot. Then save
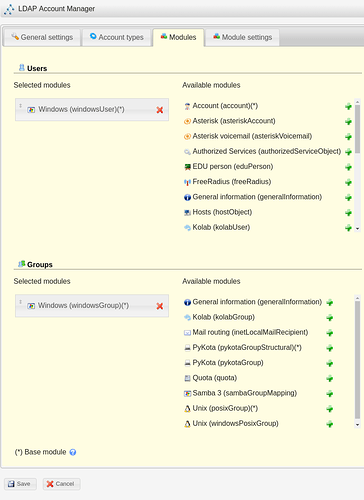
-7.b- Edit the “Modules” tab, by selecting windows modules, then save
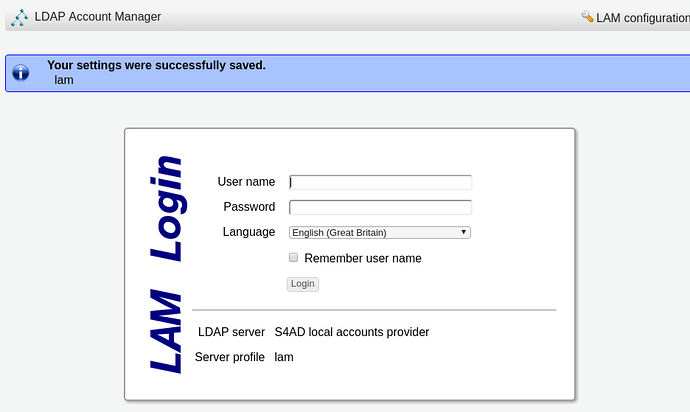
-8.a- After saving, the login form is displayed.
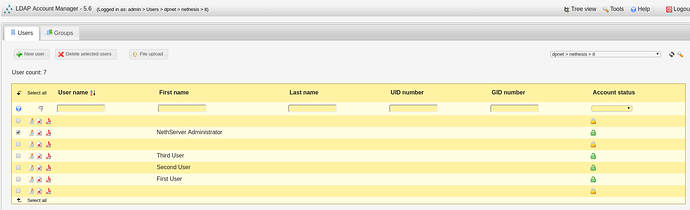
-8.b- Log in as “admin/adminpass”. This is the result
Additional information is on TFM: