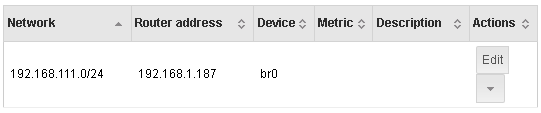
I tested again and as described in the link above all you need is a static route on your Dell sonicwall tz300 to reach the VPN network 192.168.111.0/24 via the VPN server. The sonicwall blocks because it doesn’t know the VPN network.
On a Nethserver it would look like this: