Single SignOn Has been a sticky Discussion in these forums: Search results for 'SSO #feature' - NethServer Community
We are Happy to Present Zitadel SSO is Now Nethserver App;
An Alternative to Authentik Equally Robust, But completely Free and OSS. No premium versions
Zitadel Can Infinitely Scale with CockroachDB
However Our Setup Uses PgSQL, which i felt was a Simpler Option for NS8 Clusters and Users
Pre-Installation
Create Normal and WildCard DNS record like
auth.domain.tld
*.auth.domain.tld
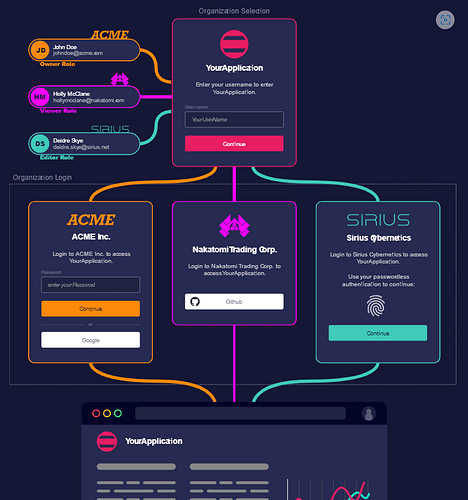
Zitadel Is Multi Tenant By Design, for SaaS B2B Cases thus, for each New Organization Created, we tend to have orgName.zitadel.domain.tld
Installation
Install our Repo through https://forge.genius.ke/
Once Installed and Enabled, locate Zitadel from the UI
After Installation, configure Zitadel, and Access your domain
Default Login Details
USERNAME: zitadel-admin@zitadel.fqdn
PWD: Password1!
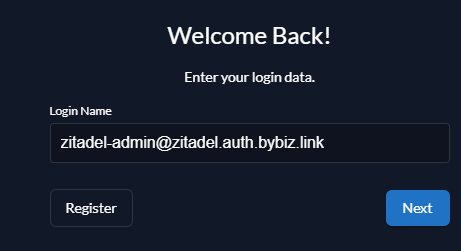
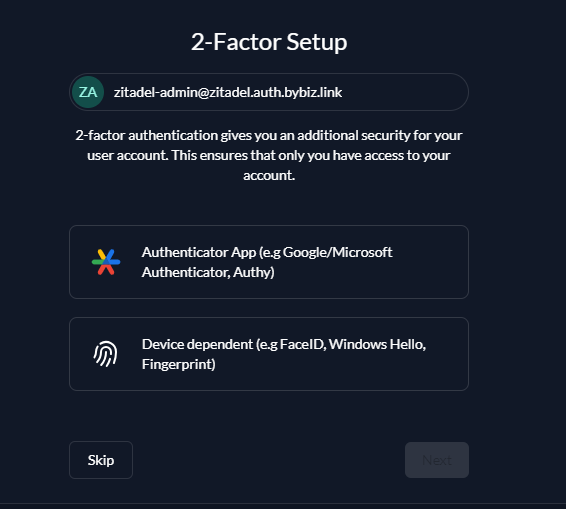
IF correct Should take you to Password Page
Skip or Setup 2FA
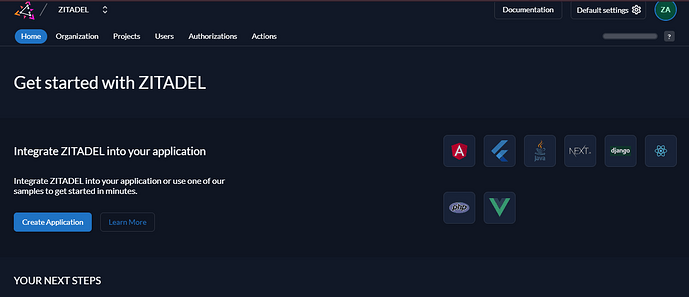
After changing Default Password, you should be able to see your dashboard
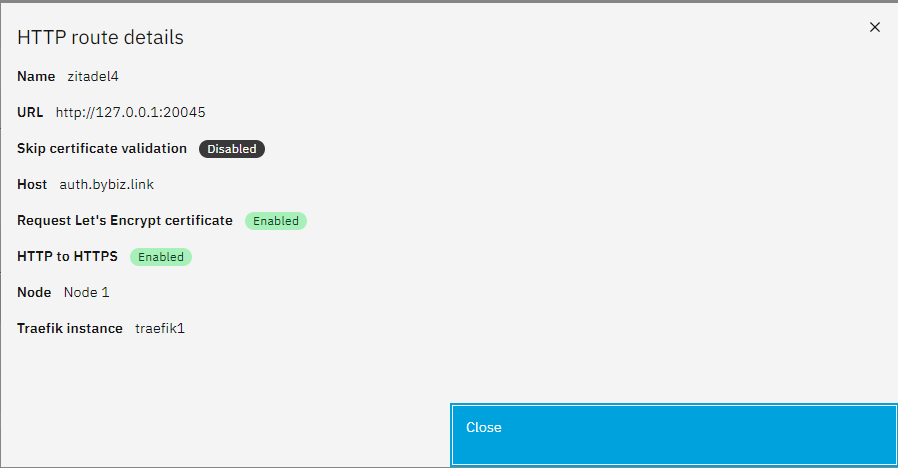
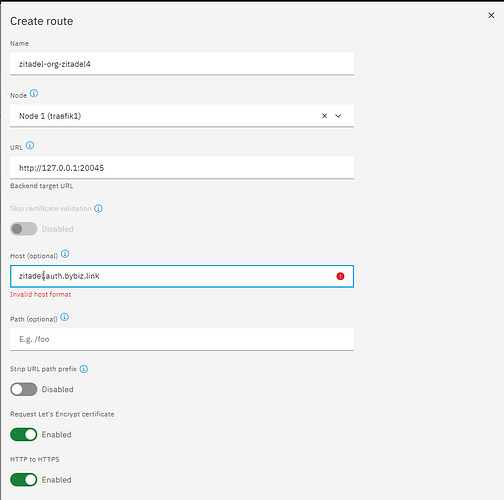
Locate Zitadel Http Routes in settings
Create Wildcard http Routes, Defind by your Wildcard Domain defined for zitadel
IN my Tests it was impossble to define a wildcard route

SO i defined the First Available orgName
Above is meant to deal with External ZITADEL Access | ZITADEL Docs
However i still need to figure out the setup for
If you run ZITADEL behind a reverse proxy, you need to ensure that it sends the correct request headers to ZITADEL. The proxy must either ensure that
- the original Host header value is assigned to the Forwarded headers host directive.
- the original requests Host header value is unchanged by the proxy.
Zitadel Configs with Traefik are here: Configure ZITADEL with Traefik | ZITADEL Docs
Tested Apps with Ready Tutorials
Nextcloud is support here: Use ZITADEL as SSO provider for self-hosting
Configuration for Zitadel
In Zitadel, go to Instance > Settings for instance-wide LDAP setup or <Organization Name> > Settings for organization-wide LDAP setup.
Identity Providers Setup
Click Identity Providers and select Active Directory/LDAP.
Group filter is not supported in Zitadel at the time of writing.
Replace every instance of dc=example,dc=com with your configured domain.
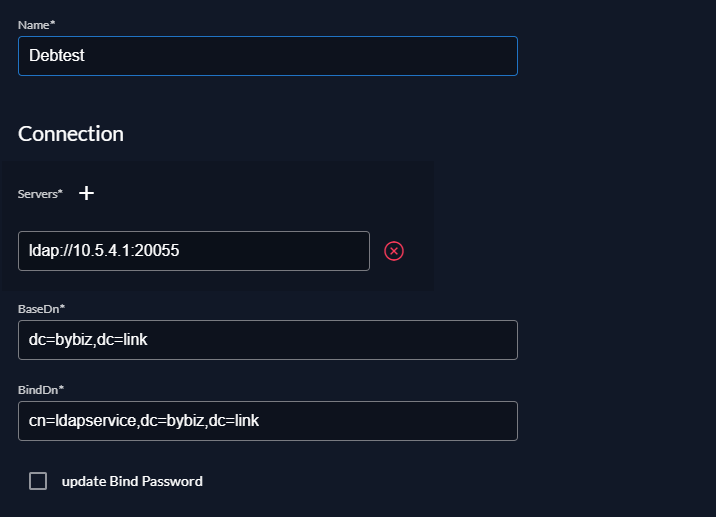
Connection
- Name: The name to identify your identity provider
- Servers:
ldaps://<FQDN or Host IP>:<Port for LADPS>orldap://<FQDN or Host IP>:<Port for LADP> - BaseDn:
dc=example,dc=com - BindDn:
cn=admin,ou=people,dc=example,dc=com. It is recommended that you create a separate user account (e.g,bind_user) instead ofadminfor sharing Bind credentials with other services. Thebind_usershould be a member of thelldap_strict_readonlygroup to limit access to your LDAP configuration in LLDAP. - Bind Password:
<user password>
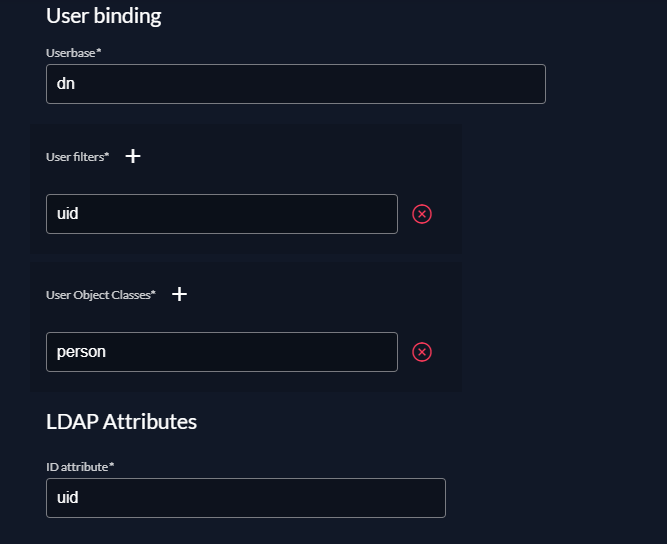
User binding
- Userbase:
dn - User filters:
uid.mailwill not work. - User Object Classes:
person
LDAP Attributes
- ID attribute:
uid - displayName attribute:
cn - Email attribute:
mail - Given name attribute:
givenName - Family name attribute:
lastName - Preferred username attribute:
uid
optional
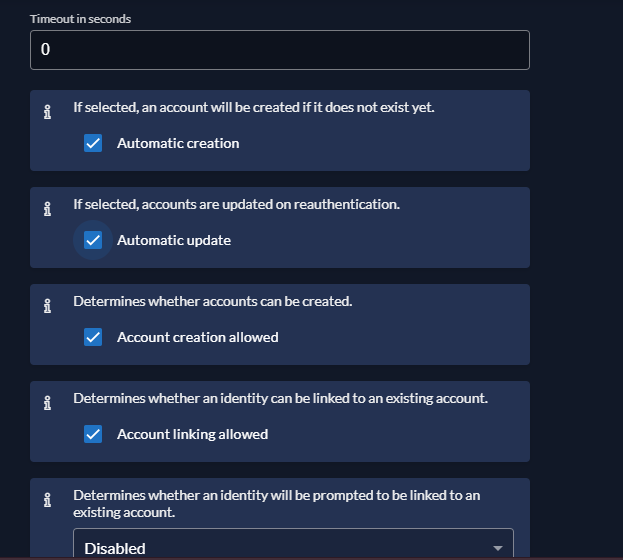
The following section applied to Zitadel only, nothing will change on LLDAP side.
- Account creation allowed
- Account linking allowed
Either one of them or both of them must be enabled
DO NOT enable Automatic update if you haven’t setup a smtp server. Zitadel will update account’s email and sent a verification code to verify the address.
If you don’t have a smtp server setup correctly and the email adress of ZITADEL Admin is changed, you are permanently locked out.
Automatic creation can automatically create a new account without user interaction when Given name attribute, Family name attribute, Email attribute, and Preferred username attribute are presented.
Enable Identity Provider
After clicking Save, you will be redirected to Identity Providers page.
Enable the LDAP by hovering onto the item and clicking the checkmark (set as available)
Enable LDAP Login
Under Settings, select Login Behavior and Security
Under Advanced, enable External IDP allowed
Thank you for testing in Advance.