NethServer Version: NethServer release 7.9.2009 (final)
Module: Network
Hello all again, its been a while! I will be online more often now, since i´m back to networking and linux.
My network is simple:
Red Interface (192.168.0.x) <-em1
Green Interface (172.16.1.x) <- br0
Its all working fine, but my client needs a Guests Network now, i normally would add a new NIC and setup a Blue Interface, but that is not possible, old server and other issues.
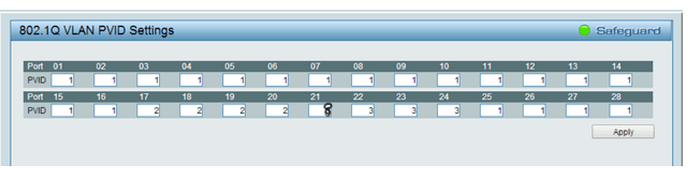
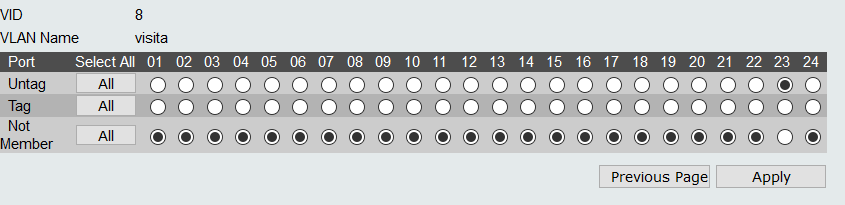
I was thinking about a VLAN, as he has a Dlink DGS 1210-24, its a smart switch, and his Access Point has the option to add a new SSID binded to a VLAN ID.
So, this is the first time i do this! 
At first i thought:
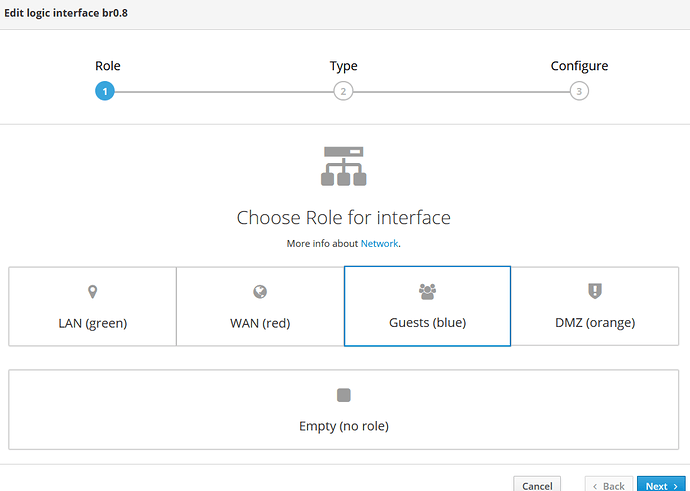
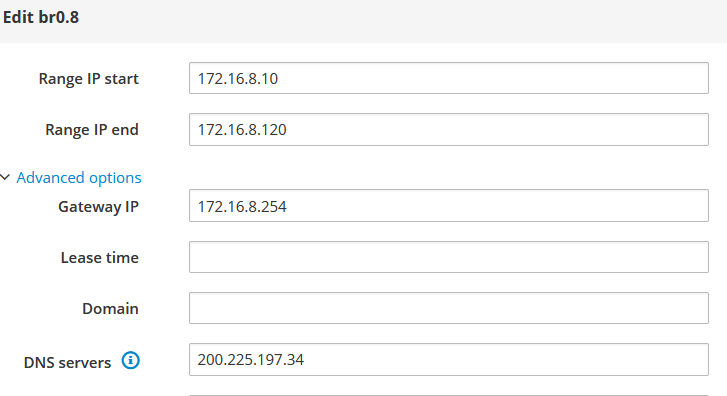
Set a new Blue Logic Interface as VLAN.
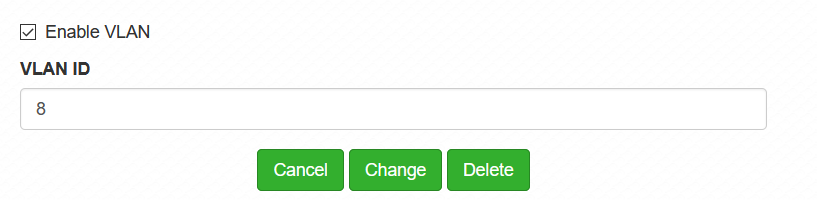
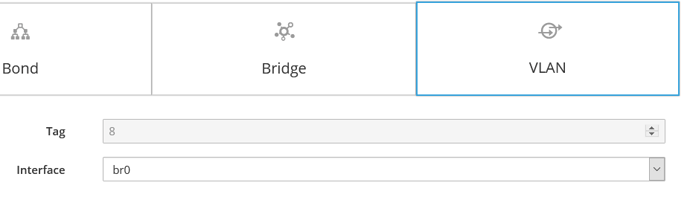
Tag: 8 (why? why not, my lucky number lol)
Interface: br0
IP: 172.16.100.254
Mask: 255.255.255.0
Enabled DHCP on that
And would go to the AP set the VLAN ID to 8, and voilá… it would work…
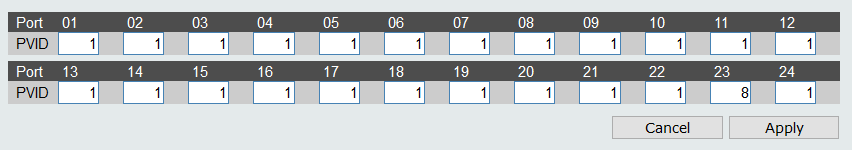
But not… lol, then i managed to get into the switch and played around the VLAN stuff, i lost access to that 
Now i will have to reset, and i ask you guys, what should i follow and read to make this work?
Thanks in advance, and i missed all that (servers and networking)