NethServer Version: 7.8.2003
Hi guys.
Today my letsencrypt certificate expired. When I request new certificate I have this error:
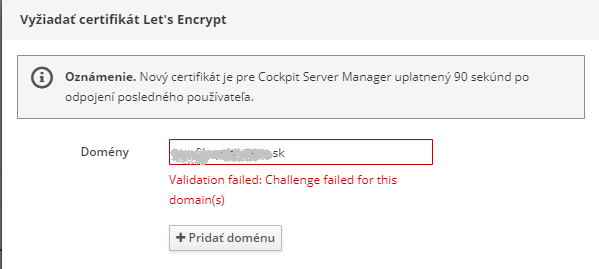
Can somebody help?
Thank you.
NethServer Version: 7.8.2003
Hi guys.
Today my letsencrypt certificate expired. When I request new certificate I have this error:

Can somebody help?
Thank you.
Not without more information. You should find the log in /var/log/letsencrypt–what’s in the most recent file there?
This is from letsencrypt.log One more thing. I want certificate for server alias with reverse proxy for https.
2020-09-10 19:14:02,829:DEBUG:certbot._internal.main:certbot version: 1.7.0
2020-09-10 19:14:02,829:DEBUG:certbot._internal.main:Arguments: [’–webroot’, ‘–webroot-path’, ‘/var/www/html/’, ‘–text’, '–non-inter$
2020-09-10 19:14:02,829:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#manual,PluginEntryPoint#null,P$
2020-09-10 19:14:02,859:DEBUG:certbot._internal.log:Root logging level set at 30
2020-09-10 19:14:02,859:INFO:certbot._internal.log:Saving debug log to /var/log/letsencrypt/letsencrypt.log
2020-09-10 19:14:02,860:DEBUG:certbot._internal.plugins.selection:Requested authenticator webroot and installer None
2020-09-10 19:14:02,861:DEBUG:certbot._internal.plugins.selection:Single candidate plugin: * webroot
Description: Place files in webroot directory
Interfaces: IAuthenticator, IPlugin
Entry point: webroot = certbot._internal.plugins.webroot:Authenticator
Initialized: <certbot._internal.plugins.webroot.Authenticator object at 0x7f1e2de29710>
Prep: True
2020-09-10 19:14:02,861:DEBUG:certbot._internal.plugins.selection:Selected authenticator <certbot._internal.plugins.webroot.Authenticato$
2020-09-10 19:14:02,861:INFO:certbot._internal.plugins.selection:Plugins selected: Authenticator webroot, Installer None
2020-09-10 19:14:02,970:DEBUG:acme.client:Sending GET request to https://acme-staging-v02.api.letsencrypt.org/directory.
2020-09-10 19:14:02,979:INFO:urllib3.connectionpool:Starting new HTTPS connection (1): acme-staging-v02.api.letsencrypt.org
2020-09-10 19:14:03,677:DEBUG:urllib3.connectionpool:“GET /directory HTTP/1.1” 200 724
2020-09-10 19:14:03,678:DEBUG:acme.client:Received response:
HTTP 200
content-length: 724
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
cache-control: public, max-age=0, no-cache
date: Thu, 10 Sep 2020 17:14:03 GMT
x-frame-options: DENY
content-type: application/json
{
“7GdrFqxaqyo”: “https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417”,
“keyChange”: “https://acme-staging-v02.api.letsencrypt.org/acme/key-change”,
“meta”: {
“caaIdentities”: [
First, don’t copy/paste out of nano; it cuts off the end of lines and could exclude important information. Second, there has to be more to this.
Sorry, you are right.
There is full log with changed IP and alias
2020-09-10 19:14:02,829:DEBUG:certbot._internal.main:certbot version: 1.7.0
2020-09-10 19:14:02,829:DEBUG:certbot._internal.main:Arguments: ['--webroot', '--webroot-path', '/var/www/html/', '--text', '--non-interactive', '--agree-tos', '--email', 'mail@mail.sk', '-d', 'alias.servername.sk', '--test-cert', '--quiet']
2020-09-10 19:14:02,829:DEBUG:certbot._internal.main:Discovered plugins: PluginsRegistry(PluginEntryPoint#manual,PluginEntryPoint#null,PluginEntryPoint#standalone,PluginEntryPoint#webroot)
2020-09-10 19:14:02,859:DEBUG:certbot._internal.log:Root logging level set at 30
2020-09-10 19:14:02,859:INFO:certbot._internal.log:Saving debug log to /var/log/letsencrypt/letsencrypt.log
2020-09-10 19:14:02,860:DEBUG:certbot._internal.plugins.selection:Requested authenticator webroot and installer None
2020-09-10 19:14:02,861:DEBUG:certbot._internal.plugins.selection:Single candidate plugin: * webroot
Description: Place files in webroot directory
Interfaces: IAuthenticator, IPlugin
Entry point: webroot = certbot._internal.plugins.webroot:Authenticator
Initialized: <certbot._internal.plugins.webroot.Authenticator object at 0x7f1e2de29710>
Prep: True
2020-09-10 19:14:02,861:DEBUG:certbot._internal.plugins.selection:Selected authenticator <certbot._internal.plugins.webroot.Authenticator object at 0x7f1e2de29710> and installer None
2020-09-10 19:14:02,861:INFO:certbot._internal.plugins.selection:Plugins selected: Authenticator webroot, Installer None
2020-09-10 19:14:02,970:DEBUG:acme.client:Sending GET request to https://acme-staging-v02.api.letsencrypt.org/directory.
2020-09-10 19:14:02,979:INFO:urllib3.connectionpool:Starting new HTTPS connection (1): acme-staging-v02.api.letsencrypt.org
2020-09-10 19:14:03,677:DEBUG:urllib3.connectionpool:"GET /directory HTTP/1.1" 200 724
2020-09-10 19:14:03,678:DEBUG:acme.client:Received response:
HTTP 200
content-length: 724
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
cache-control: public, max-age=0, no-cache
date: Thu, 10 Sep 2020 17:14:03 GMT
x-frame-options: DENY
content-type: application/json
{
"7GdrFqxaqyo": "https://community.letsencrypt.org/t/adding-random-entries-to-the-directory/33417",
"keyChange": "https://acme-staging-v02.api.letsencrypt.org/acme/key-change",
"meta": {
"caaIdentities": [
"letsencrypt.org"
],
"termsOfService": "https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf",
"website": "https://letsencrypt.org/docs/staging-environment/"
},
"newAccount": "https://acme-staging-v02.api.letsencrypt.org/acme/new-acct",
"newNonce": "https://acme-staging-v02.api.letsencrypt.org/acme/new-nonce",
"newOrder": "https://acme-staging-v02.api.letsencrypt.org/acme/new-order",
"revokeCert": "https://acme-staging-v02.api.letsencrypt.org/acme/revoke-cert"
}
2020-09-10 19:14:03,678:DEBUG:acme.client:Requesting fresh nonce
2020-09-10 19:14:03,678:DEBUG:acme.client:Sending HEAD request to https://acme-staging-v02.api.letsencrypt.org/acme/new-nonce.
2020-09-10 19:14:03,846:DEBUG:urllib3.connectionpool:"HEAD /acme/new-nonce HTTP/1.1" 200 0
2020-09-10 19:14:03,847:DEBUG:acme.client:Received response:
HTTP 200
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index"
cache-control: public, max-age=0, no-cache
date: Thu, 10 Sep 2020 17:14:03 GMT
x-frame-options: DENY
replay-nonce: 0002frba12wRGJgNfKPpXHCsyIwrt0gVaNml7eLXYvW4fKw
2020-09-10 19:14:03,847:DEBUG:acme.client:Storing nonce: 0002frba12wRGJgNfKPpXHCsyIwrt0gVaNml7eLXYvW4fKw
2020-09-10 19:14:03,847:DEBUG:acme.client:JWS payload:
{
"termsOfServiceAgreed": true,
"contact": [
"mailto:mail@mail.sk"
]
}
2020-09-10 19:14:03,852:DEBUG:acme.client:Sending POST request to https://acme-staging-v02.api.letsencrypt.org/acme/new-acct:
{
"protected": "eyJub25jZSI6ICIwMDAyZnJiYTEyd1JHSmdOZktQcFhIQ3N5SXdydDBnVmFObWw3ZUxYWXZXNGZLdyIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9uZXctYWNjdCIsICJqd2siOiB7ImUiOiAiQVFBQiIsICJrdHkiOiAiUlNBIiwgIm4iOiAiclRaeHhwNVZrZXA1cjdFZUppYUdNc281MERqTmM5eXlvNzFaQzhPWEJlZ001UnNJNzUtTGNFM19faGl2ZUctUTRFaWZkQldRaXdrMndLclpfZ0s3Q1AzQlBRTkJnaS04dFdjQlpqa0hZMVlsUGxWam9qc2xQWW1wRlZvTG51WlB5UlFFNE15Q3dGN25ScGkyel9rYnVDTlZkU0RnSmNSdF90dXlCc1dzT1U2STlFOGlrLTNoV2hTazFObXRKQ1hMVXRkSHlGX2JyZEFDZEVJR1B0UUt2NVFSZ20yY1llVTdsci12Tzl0Tm16d2xGd1NIVVRFaERWZVAyVjJSMWhSOUxreVhVbGlXVF9mQ0QtejU5T2JoYVVWM09KZVE0eE5JRkVaX0lRUjlDZnRRNUtQdFFBUjQ0WjExdXFtYmItN1dQeGJDMThHWWxYc0JJMUJOMTdmcVBRIn0sICJhbGciOiAiUlMyNTYifQ",
"payload": "ewogICJ0ZXJtc09mU2VydmljZUFncmVlZCI6IHRydWUsIAogICJjb250YWN0IjogWwogICAgIm1haWx0bzptYXhjb21wdXRlcnNAbWF4Y29tcHV0ZXJzLnNrIgogIF0KfQ",
"signature": "ECGGgLMoxk4TLL5OEPx0wP4gPtZMAAPlbMatLew6TkB3Cur_UcjTGSCgcejc8TKhdltgj2I8MKJzayJ3Nmuo-gRxLiO2eW8Y6-_aQDcCmekmo6FNNz7iQTcaiDckPzdjs14ruGdUbZG3e37b8s1vYMyBgbVs-0NrKLNRQPlmKD4eWGZKtqH063cW6fB7LZCLnkK8b0yz8E7AE6Lf_Nn57oZfkadrJlA7MJTrou9vK1ftUeRqWhDRdacbYMk5BCC8GaU3ZK_7WcuEG4N5hZY7f-hUX0p6DdI-aVyLkbB-KkRYFw_n5l_PaugvuDRxKWeis0LL-V_OaU5pYQ4_nKbZKQ"
}
2020-09-10 19:14:04,032:DEBUG:urllib3.connectionpool:"POST /acme/new-acct HTTP/1.1" 201 570
2020-09-10 19:14:04,033:DEBUG:acme.client:Received response:
HTTP 201
content-length: 570
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index", <https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf>;rel="terms-of-service"
location: https://acme-staging-v02.api.letsencrypt.org/acme/acct/15580560
boulder-requester: 15580560
date: Thu, 10 Sep 2020 17:14:03 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0001prnDUMkAEy9Yj_83WGONyrrU5bRWMbzle7SMv1QGD7k
{
"key": {
"kty": "RSA",
"n": "rTZxxp5Vkep5r7EeJiaGMso50DjNc9yyo71ZC8OXBegM5RsI75-LcE3__hiveG-Q4EifdBWQiwk2wKrZ_gK7CP3BPQNBgi-8tWcBZjkHY1YlPlVjojslPYmpFVoLnuZPyRQE4MyCwF7nRpi2z_kbuCNVdSDgJcRt_tuyBsWsOU6I9E8ik-3hWhSk1NmtJCXLUtdHyF_brdACdEIGPtQKv5QRgm2cYeU7lr-vO9tNmzwlFwSHUTEhDVeP2V2R1hR9LkyXUliWT_fCD-z59ObhaUV3OJeQ4xNIFEZ_IQR9CftQ5KPtQAR44Z11uqmbb-7WPxbC18GYlXsBI1BN17fqPQ",
"e": "AQAB"
},
"contact": [
"mailto: mail@mail.sk"
],
"initialIp": "my_public_IP",
"createdAt": "2020-09-10T17:14:03.942121002Z",
"status": "valid"
}
2020-09-10 19:14:04,033:DEBUG:acme.client:Storing nonce: 0001prnDUMkAEy9Yj_83WGONyrrU5bRWMbzle7SMv1QGD7k
2020-09-10 19:14:04,035:DEBUG:certbot._internal.reporter:Reporting to user: Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal.
2020-09-10 19:14:04,036:DEBUG:certbot._internal.main:Picked account: <Account(RegistrationResource(body=Registration(status=u'valid', terms_of_service_agreed=None, agreement=None, only_return_existing=None, contact=(u'mailto:mail@mail.sk',), key=JWKRSA(key=<ComparableRSAKey(<cryptography.hazmat.backends.openssl.rsa._RSAPublicKey object at 0x7f1e2d9f3210>)>), external_account_binding=None), uri='https://acme-staging-v02.api.letsencrypt.org/acme/acct/15580560', new_authzr_uri=None, terms_of_service='https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf'), ce9906d418870cc9051390e9fc9cdd84, Meta(creation_host='original_name.servername.sk', register_to_eff=None, creation_dt=datetime.datetime(2020, 9, 10, 17, 14, 4, tzinfo=<UTC>)))>
2020-09-10 19:14:04,037:INFO:certbot._internal.main:Obtaining a new certificate
2020-09-10 19:14:04,144:DEBUG:certbot.crypto_util:Generating key (2048 bits): /etc/letsencrypt/keys/0000_key-certbot.pem
2020-09-10 19:14:04,147:DEBUG:certbot.crypto_util:Creating CSR: /etc/letsencrypt/csr/0000_csr-certbot.pem
2020-09-10 19:14:04,148:DEBUG:acme.client:JWS payload:
{
"identifiers": [
{
"type": "dns",
"value": "alias.servername.sk"
}
]
}
2020-09-10 19:14:04,151:DEBUG:acme.client:Sending POST request to https://acme-staging-v02.api.letsencrypt.org/acme/new-order:
{
"protected": "eyJub25jZSI6ICIwMDAxcHJuRFVNa0FFeTlZal84M1dHT055cnJVNWJSV01iemxlN1NNdjFRR0Q3ayIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9uZXctb3JkZXIiLCAia2lkIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xNTU4MDU2MCIsICJhbGciOiAiUlMyNTYifQ",
"payload": "ewogICJpZGVudGlmaWVycyI6IFsKICAgIHsKICAgICAgInR5cGUiOiAiZG5zIiwgCiAgICAgICJ2YWx1ZSI6ICJzZWFmaWxlLnByb210LW10LnNrIgogICAgfQogIF0KfQ",
"signature": "VgCWlwl5L6w3zzJsEzw2GkkwGHluCaQ5GAu4VkVUeWjAdPxV54XKaLWYH_67YMZVGNdjVLpwSq6B5WC_eaHt2N4yN7OlKzD9iWa3ml7-orDOWbpH3vAJ6xfF9ESxr0ZNRGoJE6s_AlPnMPA0XRmjDCbgqGOwfrYI3RztjSRHCtYg11j40-XW5t1PbBCH2HWHEZgUwprJZpU0b6NbD2jGn2T_0R9spT0RlsFSCTklMmoV_vnNHx4INx0j6gdck_MzBLplTi_ppmOE6sxgNhmgnv6SOaykW4Bn5Iyb6JNXtUBSPGzz_H2ByQ6TGolkkx8pqW-nJ15QES_ZTvcqdwKLQg"
}
2020-09-10 19:14:04,340:DEBUG:urllib3.connectionpool:"POST /acme/new-order HTTP/1.1" 201 363
2020-09-10 19:14:04,341:DEBUG:acme.client:Received response:
HTTP 201
content-length: 363
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index"
location: https://acme-staging-v02.api.letsencrypt.org/acme/order/15580560/146769259
boulder-requester: 15580560
date: Thu, 10 Sep 2020 17:14:04 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0002yO1CoucWvAsKbmfgbXkkWHhNJu2zWKB6BG2VrQoJj4A
{
"status": "pending",
"expires": "2020-09-17T17:14:04.243835803Z",
"identifiers": [
{
"type": "dns",
"value": "alias.servername.sk"
}
],
"authorizations": [
"https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/109322691"
],
"finalize": "https://acme-staging-v02.api.letsencrypt.org/acme/finalize/15580560/146769259"
}
2020-09-10 19:14:04,341:DEBUG:acme.client:Storing nonce: 0002yO1CoucWvAsKbmfgbXkkWHhNJu2zWKB6BG2VrQoJj4A
2020-09-10 19:14:04,343:DEBUG:acme.client:JWS payload:
2020-09-10 19:14:04,346:DEBUG:acme.client:Sending POST request to https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/109322691:
{
"protected": "eyJub25jZSI6ICIwMDAyeU8xQ291Y1d2QXNLYm1mZ2JYa2tXSGhOSnUyeldLQjZCRzJWclFvSmo0QSIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hdXRoei12My8xMDkzMjI2OTEiLCAia2lkIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xNTU4MDU2MCIsICJhbGciOiAiUlMyNTYifQ",
"payload": "",
"signature": "o5fgSTKDPAeWOpJMXKKoWSNw5lmQbYBhx5TlCbkElND_6v69Zp-H1o4SmrZAC7j6yK3N36LrC0PIlzFUKpasJGdbK-M0DdqZRYqlk1JlvrCfnoc2DxidQldsfvRYWLVPSj6gqf1CWFxcCsxPtefsBpkVaRQvD2jMlunp6vLeuQdAWlUaEgJLaEjM6ZeYqId4Jz3kNSNOXiurZQWa0PynalD4A895PYuHI3x3DdNFuGXxvVxf3cxlMF-KWfuVWU7GAILjv9s1OBBVnjibj-qzMzot18XlOG2f-5PZhOe1zP43khORz4sKdjq8gakUyEm5pusbrsdiLPabx-o3Tbt1fA"
}
2020-09-10 19:14:04,517:DEBUG:urllib3.connectionpool:"POST /acme/authz-v3/109322691 HTTP/1.1" 200 818
2020-09-10 19:14:04,518:DEBUG:acme.client:Received response:
HTTP 200
content-length: 818
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index"
boulder-requester: 15580560
date: Thu, 10 Sep 2020 17:14:04 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0001g8m-qft4foHccMeQ7twNdyfm6l1MA5YB37V70Aaqq5M
{
"identifier": {
"type": "dns",
"value": "alias.servername.sk"
},
"status": "pending",
"expires": "2020-09-17T17:14:04Z",
"challenges": [
{
"type": "http-01",
"status": "pending",
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/fwxcqg",
"token": "PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo"
},
{
"type": "dns-01",
"status": "pending",
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/s4qotQ",
"token": "PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo"
},
{
"type": "tls-alpn-01",
"status": "pending",
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/reqI3A",
"token": "PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo"
}
]
}
2020-09-10 19:14:04,518:DEBUG:acme.client:Storing nonce: 0001g8m-qft4foHccMeQ7twNdyfm6l1MA5YB37V70Aaqq5M
2020-09-10 19:14:04,519:INFO:certbot._internal.auth_handler:Performing the following challenges:
2020-09-10 19:14:04,519:INFO:certbot._internal.auth_handler:http-01 challenge for alias.servername.sk
2020-09-10 19:14:04,519:INFO:certbot._internal.plugins.webroot:Using the webroot path /var/www/html for all unmatched domains.
2020-09-10 19:14:04,519:DEBUG:certbot._internal.plugins.webroot:Creating root challenges validation dir at /var/www/html/.well-known/acme-challenge
2020-09-10 19:14:04,524:DEBUG:certbot._internal.plugins.webroot:Attempting to save validation to /var/www/html/.well-known/acme-challenge/PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo
2020-09-10 19:14:04,524:INFO:certbot._internal.auth_handler:Waiting for verification...
2020-09-10 19:14:04,525:DEBUG:acme.client:JWS payload:
{}
2020-09-10 19:14:04,527:DEBUG:acme.client:Sending POST request to https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/fwxcqg:
{
"protected": "eyJub25jZSI6ICIwMDAxZzhtLXFmdDRmb0hjY01lUTd0d05keWZtNmwxTUE1WUIzN1Y3MEFhcXE1TSIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9jaGFsbC12My8xMDkzMjI2OTEvZnd4Y3FnIiwgImtpZCI6ICJodHRwczovL2FjbWUtc3RhZ2luZy12MDIuYXBpLmxldHNlbmNyeXB0Lm9yZy9hY21lL2FjY3QvMTU1ODA1NjAiLCAiYWxnIjogIlJTMjU2In0",
"payload": "e30",
"signature": "Ns4eMYLIVFkLjGg5jxW2yep_xjZXYfCT0-LmUJhFuKqY3nxSGnXF2Bf-Do9fzrzBAA2JXeZfSSp0raQsqYFW-yxONmWXt_iBLobO6HoLsozsM5W6Y8T7QFOAUsIkBKGcNqEwzk_MaErEuJF8N2DvQoaIIrKNIcK3Ttr135DCLk2aa6hYwOQsujFYhWKUhJgc__Ug3gu_RIUdQNxfjZaOai6-MJNtcUT1cZi3mdPmlt9dh0kE73My-Luv0PNmnxhStl-g5gQz8V8VsEdUj-Mp0ZO57diuGKD69EB3HcWxczbnKANJnvgnU2eRBRiEJOa5ESkEnvazB6e_84LZMhBgfw"
}
2020-09-10 19:14:04,700:DEBUG:urllib3.connectionpool:"POST /acme/chall-v3/109322691/fwxcqg HTTP/1.1" 200 192
2020-09-10 19:14:04,701:DEBUG:acme.client:Received response:
HTTP 200
content-length: 192
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index", <https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/109322691>;rel="up"
location: https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/fwxcqg
boulder-requester: 15580560
date: Thu, 10 Sep 2020 17:14:04 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0001Jk9St1HHdGk7Ypv0aGiQHliYodC03fSswzwbiJmY7Ag
{
"type": "http-01",
"status": "pending",
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/fwxcqg",
"token": "PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo"
}
2020-09-10 19:14:04,701:DEBUG:acme.client:Storing nonce: 0001Jk9St1HHdGk7Ypv0aGiQHliYodC03fSswzwbiJmY7Ag
2020-09-10 19:14:05,702:DEBUG:acme.client:JWS payload:
2020-09-10 19:14:05,705:DEBUG:acme.client:Sending POST request to https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/109322691:
{
"protected": "eyJub25jZSI6ICIwMDAxSms5U3QxSEhkR2s3WXB2MGFHaVFIbGlZb2RDMDNmU3N3endiaUptWTdBZyIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hdXRoei12My8xMDkzMjI2OTEiLCAia2lkIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xNTU4MDU2MCIsICJhbGciOiAiUlMyNTYifQ",
"payload": "",
"signature": "J_5nwJGh5s_3lCCEwNxH9xJDSfTFbdFIo8EnlUrH4p7G9GHQqZYG-lThKyKDgZqr8YStwn9esQD_Pi7F1zxYCn58IYlF7e1MOe3b8e2Ge6mbEg71nKGKC8R3ytWnVMo2B8uC1fnCZ4O1SpG0LpwIAaGbLoyHAKey4Qu4QsTmF6vWeN0UrsJllT-1mf_qKnGZO8Iycx0UIx021-o40DirECHWoLn2f8Fbk8UXmgPHYvI4u2a51xHHLufuCtPlVcDLpXYtbFkwB6sINO_on41R_NuLl2oHlLkKsyjGJWCPouhl7S8gu9qZHB3_4cfNpjdkXqczzyYUblq3u-GBP8epYA"
}
2020-09-10 19:14:05,876:DEBUG:urllib3.connectionpool:"POST /acme/authz-v3/109322691 HTTP/1.1" 200 818
2020-09-10 19:14:05,877:DEBUG:acme.client:Received response:
HTTP 200
content-length: 818
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index"
boulder-requester: 15580560
date: Thu, 10 Sep 2020 17:14:05 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0001LiLEitRuOF5G1EPZKsntYy_2Ug7i5nN-4SzshbCXhS0
{
"identifier": {
"type": "dns",
"value": "alias.servername.sk"
},
"status": "pending",
"expires": "2020-09-17T17:14:04Z",
"challenges": [
{
"type": "http-01",
"status": "pending",
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/fwxcqg",
"token": "PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo"
},
{
"type": "dns-01",
"status": "pending",
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/s4qotQ",
"token": "PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo"
},
{
"type": "tls-alpn-01",
"status": "pending",
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/reqI3A",
"token": "PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo"
}
]
}
2020-09-10 19:14:05,877:DEBUG:acme.client:Storing nonce: 0001LiLEitRuOF5G1EPZKsntYy_2Ug7i5nN-4SzshbCXhS0
2020-09-10 19:14:08,881:DEBUG:acme.client:JWS payload:
2020-09-10 19:14:08,884:DEBUG:acme.client:Sending POST request to https://acme-staging-v02.api.letsencrypt.org/acme/authz-v3/109322691:
{
"protected": "eyJub25jZSI6ICIwMDAxTGlMRWl0UnVPRjVHMUVQWktzbnRZeV8yVWc3aTVuTi00U3pzaGJDWGhTMCIsICJ1cmwiOiAiaHR0cHM6Ly9hY21lLXN0YWdpbmctdjAyLmFwaS5sZXRzZW5jcnlwdC5vcmcvYWNtZS9hdXRoei12My8xMDkzMjI2OTEiLCAia2lkIjogImh0dHBzOi8vYWNtZS1zdGFnaW5nLXYwMi5hcGkubGV0c2VuY3J5cHQub3JnL2FjbWUvYWNjdC8xNTU4MDU2MCIsICJhbGciOiAiUlMyNTYifQ",
"payload": "",
"signature": "S19-zdSlYkShkv4rce37bGhiCQhSTs7AUwk71X3DVmBeTDn4pIqxlrX9Bq2M9aq__QcYIqC-55iX7nUlbmakLFyi4BaV-4Fv9WscAiO17lCEnqt9rtH82uaafC6z25glCBxnAa89ah-Gcs0eOXlwxpf7TercIGz_ke9ecwMHYjb603SdD8-jsWxM8OWxTW4JpqZdNTj6cS9hPgDS7rj28ZfJTkHbIsShKCiim501U05IRb1KcWYChy6-kfH7SWs3nHXVioknYFH3xveGw-TwcNV7LMoVRXOf0Lllnq4lcqfiOmyCrw897C9jrrWdSJNLvA3QNS3e6a3KV6LTeL1VoA"
}
2020-09-10 19:14:09,055:DEBUG:urllib3.connectionpool:"POST /acme/authz-v3/109322691 HTTP/1.1" 200 1539
2020-09-10 19:14:09,055:DEBUG:acme.client:Received response:
HTTP 200
content-length: 1539
cache-control: public, max-age=0, no-cache
strict-transport-security: max-age=604800
server: nginx
connection: keep-alive
link: <https://acme-staging-v02.api.letsencrypt.org/directory>;rel="index"
boulder-requester: 15580560
date: Thu, 10 Sep 2020 17:14:08 GMT
x-frame-options: DENY
content-type: application/json
replay-nonce: 0002t9W9qMAnlXMozk0qntvMWbqojh4fYMX2OGHjM9baWnI
{
"identifier": {
"type": "dns",
"value": "alias.servername.sk"
},
"status": "invalid",
"expires": "2020-09-17T17:14:04Z",
"challenges": [
{
"type": "http-01",
"status": "invalid",
"error": {
"type": "urn:ietf:params:acme:error:unauthorized",
"detail": "Invalid response from https://alias.servername.sk/.well-known/acme-challenge/PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo [publicIP]: \"\\n\\n\u003c!DOCTYPE html\u003e\\n\u003chtml lang=\\\"en\\\"\u003e\\n\u003chead\u003e\\n\u003ctitle\u003ePROMT seafile\u003c/title\u003e\\n\u003cmeta http-equiv=\\\"Content-type\\\" content=\\\"text/html; chars\"",
"status": 403
},
"url": "https://acme-staging-v02.api.letsencrypt.org/acme/chall-v3/109322691/fwxcqg",
"token": "PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo",
"validationRecord": [
{
"url": "http://alias.servername.sk/.well-known/acme-challenge/PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo",
"hostname": "alias.servername.sk",
"port": "80",
"addressesResolved": [
"publicIP"
],
"addressUsed": "publicIP"
},
{
"url": "https://alias.servername.sk/.well-known/acme-challenge/PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo",
"hostname": "alias.servername.sk",
"port": "443",
"addressesResolved": [
"publicIP"
],
"addressUsed": "publicIP"
}
]
}
]
}
2020-09-10 19:14:09,056:DEBUG:acme.client:Storing nonce: 0002t9W9qMAnlXMozk0qntvMWbqojh4fYMX2OGHjM9baWnI
2020-09-10 19:14:09,056:WARNING:certbot._internal.auth_handler:Challenge failed for domain alias.servername.sk
2020-09-10 19:14:09,056:INFO:certbot._internal.auth_handler:http-01 challenge for alias.servername.sk
2020-09-10 19:14:09,057:DEBUG:certbot._internal.reporter:Reporting to user: The following errors were reported by the server:
Domain: alias.servername.sk
Type: unauthorized
Detail: Invalid response from https://alias.servername.sk/.well-known/acme-challenge/PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo [publicIP]: "\n\n<!DOCTYPE html>\n<html lang=\"en\">\n<head>\n<title>PROMT seafile</title>\n<meta http-equiv=\"Content-type\" content=\"text/html; chars"
To fix these errors, please make sure that your domain name was entered correctly and the DNS A/AAAA record(s) for that domain contain(s) the right IP address.
2020-09-10 19:14:09,057:DEBUG:certbot._internal.error_handler:Encountered exception:
Traceback (most recent call last):
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 91, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 180, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
AuthorizationError: Some challenges have failed.
2020-09-10 19:14:09,057:DEBUG:certbot._internal.error_handler:Calling registered functions
2020-09-10 19:14:09,057:INFO:certbot._internal.auth_handler:Cleaning up challenges
2020-09-10 19:14:09,057:DEBUG:certbot._internal.plugins.webroot:Removing /var/www/html/.well-known/acme-challenge/PHfBXTPrsq3I2rZO5qxP5-tU3zwSPylNw_0G_INpNoo
2020-09-10 19:14:09,058:DEBUG:certbot._internal.plugins.webroot:All challenges cleaned up
2020-09-10 19:14:09,058:DEBUG:certbot._internal.log:Exiting abnormally:
Traceback (most recent call last):
File "/usr/bin/certbot", line 9, in <module>
load_entry_point('certbot==1.7.0', 'console_scripts', 'certbot')()
File "/usr/lib/python2.7/site-packages/certbot/main.py", line 15, in main
return internal_main.main(cli_args)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 1357, in main
return config.func(config, plugins)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 1237, in certonly
lineage = _get_and_save_cert(le_client, config, domains, certname, lineage)
File "/usr/lib/python2.7/site-packages/certbot/_internal/main.py", line 121, in _get_and_save_cert
lineage = le_client.obtain_and_enroll_certificate(domains, certname)
File "/usr/lib/python2.7/site-packages/certbot/_internal/client.py", line 418, in obtain_and_enroll_certificate
cert, chain, key, _ = self.obtain_certificate(domains)
File "/usr/lib/python2.7/site-packages/certbot/_internal/client.py", line 351, in obtain_certificate
orderr = self._get_order_and_authorizations(csr.data, self.config.allow_subset_of_names)
File "/usr/lib/python2.7/site-packages/certbot/_internal/client.py", line 398, in _get_order_and_authorizations
authzr = self.auth_handler.handle_authorizations(orderr, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 91, in handle_authorizations
self._poll_authorizations(authzrs, max_retries, best_effort)
File "/usr/lib/python2.7/site-packages/certbot/_internal/auth_handler.py", line 180, in _poll_authorizations
raise errors.AuthorizationError('Some challenges have failed.')
AuthorizationError: Some challenges have failed.
2020-09-10 19:14:09,059:ERROR:certbot._internal.log:Some challenges have failed.
I thing there is some problem with virtualhost configuration. I have it based on my how-to.
OK, this is your problem. When trying to get the validation file, Let’s Encrypt got a 403 error from your server. You’re probably right that it’s something in your virtual host configuration.
I found DocumentRoot /var/www in /etc/e-smith/templates-custom/etc/httpd/conf.d/virtualhosts.conf/15_seafile and I think there you get a permission denied error.
Thank you for response.
Can you explain me solution? This is my forst work with virtualhosts 
Should I change DorcumentRoot path or change permision for /var/www ? And if change DocumentRoot what is the right path?
Thank you.
Not yet, I’m going to test your howto the next days. I saw seafile provides a centos repo too.
I think you don’t need DocumentRoot at all.
Hi Markus.
Any news? I tried disable virtual host and try again request cerificate, but with same result. 
Did you remove the custom template /etc/e-smith/templates-custom/etc/httpd/conf.d/virtualhosts.conf/15_seafile and applied the config:
signal-event nethserver-httpd-update
The seafile vhost alias.servername.sk should not be in httpd config anymore:
httpd -S
Markus you are great!!! I owe you a big BEER 
Now eerything is OK. But certificate is valid due to december. So I think my problem will be here again in december. So I need some tune-up for 15_seafile template.
Great, I’m sure we’ll find a solution until december.
Hi,
I’m back with my problem again. I need to solve it for full automatic certificate renew. When I delete virtualhost in cockpit, delete 15?sefile template, delete /etc/httpd/conf.d/virtualhosts.conf, and run signal-event nethserver-httpd-update, there is still seafile in virtualhost.
Run db vhosts show>
[root@server1 vhost]# db vhosts show
default=vhost
Description=Default virtual host
FtpPassword=
FtpStatus=disabled
f7fd8046d4ec51c=vhost-deleted
Access=public
Description=seafile
ForceSslStatus=enabled
FtpPassword=
FtpStatus=disabled
Indexes=disabled
MaxExecutionTime=0
MemoryLimit=252
PasswordStatus=disabled
PasswordValue=
PhpCustomSettings=enabled
PhpRhVersion=default
PostMaxSize=196
ServerNames=seafile.myserver.sk
SslCertificate=/etc/letsencrypt/live/seafile.myserver.sk/cert.pem
UploadMaxFilesize=128
status=enabledAnd this I think should be problem. It is deleted, but enabled. But how to repair it.
Thanks
And today I’m not able to request new certificate. Using previous method not working. All virtualhost records are deleted in Cockpit, but when I try create new virtualhost, it wrote that name alreadz exist.
I think you need to delete the vhost from vhosts db
db vhosts delete f7fd8046d4ec51c
and apply the config with
signal-event nethserver-httpd-update
Thanks for reply.
Now I am unable to create reverse proxy - virtualhost already exist. Also with problem for request certificate.
[Mon Mar 15 12:44:51.041442 2021] [proxy:error] [pid 4844] (111)Connection refused: AH00957: HTTP: attempt to connect to 127.0.0.1:8000 (127.0.0.1) failed
[Mon Mar 15 12:44:51.041470 2021] [proxy:error] [pid 4844] AH00959: ap_proxy_connect_backend disabling worker for (127.0.0.1) for 60s
[Mon Mar 15 12:44:51.041477 2021] [proxy_http:error] [pid 4844] [client 18.224.20.83:11276] AH01114: HTTP: failed to make connection to backend: 127.0.0.1, referer: http://seafile.myserver.sk/.well-known/acme-challenge/W1zhjzSUbUYVNLZKwOHOKQ8h1mZ0s7pIsIy3bDyTPSk
[Mon Mar 15 12:44:51.350439 2021] [proxy:error] [pid 4845] (111)Connection refused: AH00957: HTTP: attempt to connect to 127.0.0.1:8000 (127.0.0.1) failed
[Mon Mar 15 12:44:51.350458 2021] [proxy:error] [pid 4845] AH00959: ap_proxy_connect_backend disabling worker for (127.0.0.1) for 60s
[Mon Mar 15 12:44:51.350463 2021] [proxy_http:error] [pid 4845] [client 66.133.109.36:40672] AH01114: HTTP: failed to make connection to backend: 127.0.0.1, referer: http://seafile.myserver.sk/.well-known/acme-challenge/W1zhjzSUbUYVNLZKwOHOKQ8h1mZ0s7pIsIy3bDyTPSkAnd my httd service is also unable start - dns.service_action_error:
echo '{"action":"start","name":"httpd"}' | /usr/bin/setsid /usr/bin/sudo /usr/libexec/nethserver/api/system-services/update | jqOkay. httpd service is running now. I had to delete file /etc/httpd/conf.d/bad_virtualhosts.conf.
And now, I am able to request certificate. And everything is now working.