Hi,
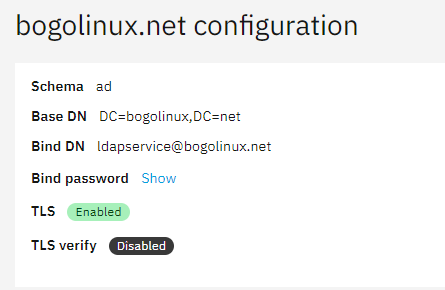
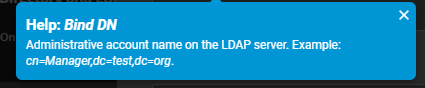
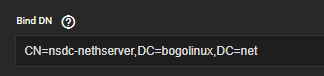
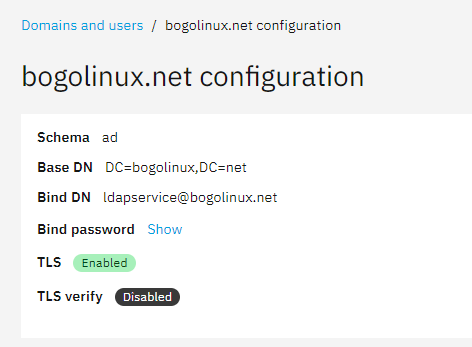
I’m trying to get TrueNAS-Scale to use the NS8 AD. My initial attempt at connection, once I worked out what the correct Bind DN parameter was (Hint, it’s not what you show on the Configuration page)
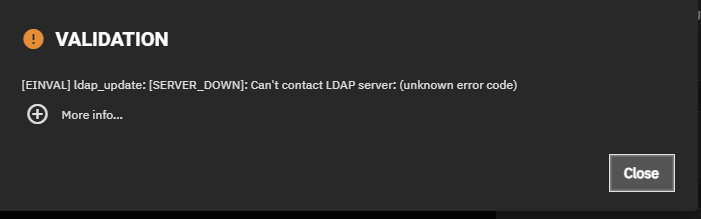
This failed with:
middlewared.service_exception.ValidationErrors: [EINVAL] ldap_update: [STRONG_AUTH_REQUIRED]: Strong(er) authentication required: BindSimple: Transport encryption required.
So looking at the addition parameters available, it looked like I had to turn on TLS for the connection, so I tried to generate a certificate for the CN used by the AD. This failed with:
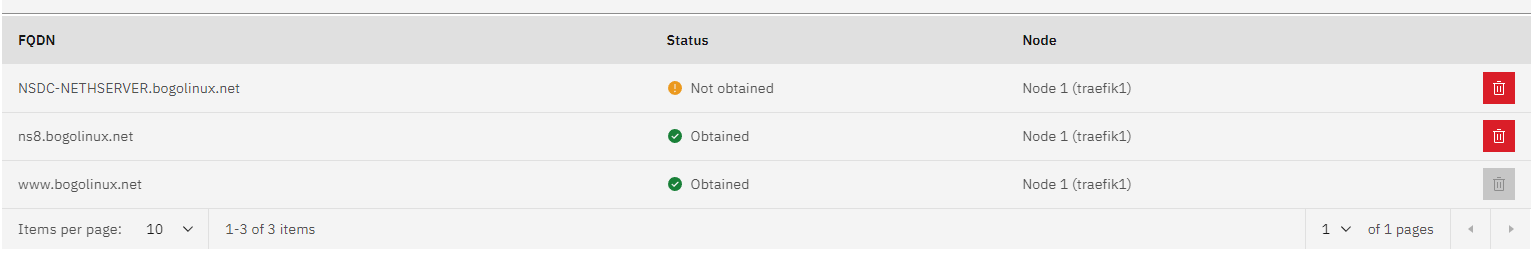
{“context”:{“action”:“set-certificate”,“data”:{“fqdn”:“NSDC-NETHSERVER.bogolinux.net”,“sync”:true},“extra”:{“description”:“Processing”,“eventId”:“24172678-dc7a-4a4d-a2b9-af59f9907fe0”,“logs”:{“instance”:“traefik1”,“path”:“?searchQuery=&context=module&selectedAppId=traefik1&followLogs=false&startDate=2024-08-19&startTime=10%3A37&autoStartSearch=true”},“title”:“Request certificate for NSDC-NETHSERVER.bogolinux.net”},“id”:“73d2ae8f-6bc1-429b-89ac-e372fe79fa94”,“parent”:“”,“queue”:“module/traefik1/tasks”,“timestamp”:“2024-08-19T17:37:34.267038547Z”,“user”:“admin”},“status”:“aborted”,“progress”:99,“subTasks”:,“validated”:true,“result”:{“error”:“”,“exit_code”:2,“file”:“task/module/traefik1/73d2ae8f-6bc1-429b-89ac-e372fe79fa94”,“output”:{“obtained”:false}}}
Looking through the traefik1 logs I couldn’t see anything obvious that was wrong and it was only at the 99% stage of the process that it appeared to fail.
I’ve got the DNS entries set up both internally and externally set up correctly to find the server, so not sure why one request would work, but not another.
Cheers.