Thanks Andy for your answer,
my first problem is I how to get the letsencrypt certificate.
We use a lancom router as router and firewall, this router is the only hardware connected directly to the internet. So I think I have to get the certificate with this router. Then I have to copy it to the first and the second server, no one of this is the AD. The AD is a Windows Server.
A self created certificate for me would much be easier, if I know how to import.
Hi
As said, you CAN use the SSL certs from Server 1:
and copy them over to Server 2…
Make a backup first of the files in question (On server 2) - and for saftey reasons also a backup of the whole server, if possible!
LE on a LANcom should be possible, also copying them over to the two NethServers, but as I only use OPNsense firewalls now, I can’t help with LANcom. Also, LANcom is a commercial product, that may limit your options.
Another thing is the aliases (For both NethServers) need to be on the LE certs - this does work when NethServer or OPNsense get’s the SSL certs.
It also depends if your DNS Provider / Hoster supports the LE API (DNS API) - that makes life easier. Mine does not support DNS API… ![]()
To get an “easy” LE SSL cert, it would be sufficient to pass Port 80 from your LANcom to the NethServer 1 and let NethServer request the LE cert. There is no risk and no “Web” changes needed on NethServer. The only html page viewable is static and as such, almost “unhackable”…
However, if your client does not want / allow this, then you need to do it the manual way with the self created certs / CA…
My 2 cents
Andy
I copied localhost.crt, but this doesn’t work too. The NSRV I tested before, it doesn’t work also, and it couldn’t be a solution, it includes the server name.
Only for information, at /etc/ssl/certs is only a link to /etc/pki/tls/certs/.
I think the problem here is that NethServer doesn’t include a “full” CA…
See eg this thread about “Issues”… (Not specific CA related)
or (better) this one about implementing a CA in Neth:
my 2 cents
Andy
Thanks again Andy,
I’ve read the two threads.
I don’t think this is a problem, of course it could be a solution, but copying the tls/ssl certificate for mail from first to second server should also be a solution.
A thunderbird for example imports the certificate of the first server and works without any issues, why doesn’t it work to import it to the second server for smart host.
There is a BIG difference in certificates, depending on server or client application…
Thunderbird is a pure client application.
Servers need to have the server name in the certificate, wheras clients do not.
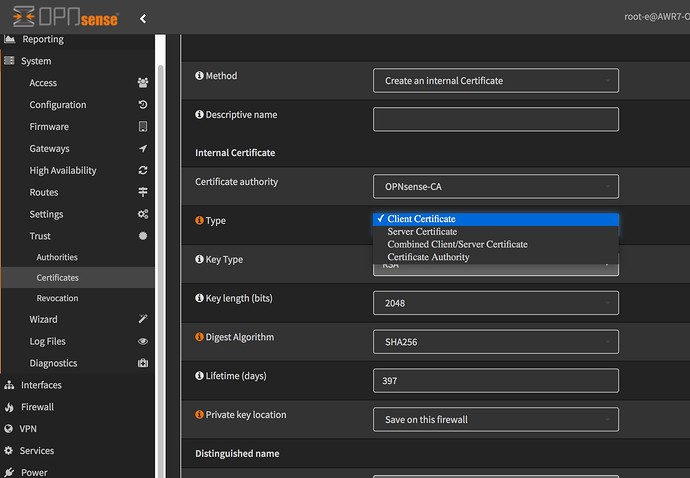
See this setting for creating a new certificate from the built in CA on OPNsense:
It’s already defined at the CA level, if it is a client or a server certificate, so that can’t be changed later on…
Server / Client attribute limits what the certificate can be used for.
But that isn’t the issue here, as the built in SSL Cert works for NethServer as a server.
I think it’s the server name, which is conflicting here.
My 2 cents
Andy
Thanks Andy for clarification, but one more question:
Isn’t server 2 acting as a client in this situation? I thought it is a mail client, which tries to send mail over the first server, which acts as mail server at my situation?
Hi Michael
In this sense you’re right, for Smarthost usage only “Client” usage is needed.
However, AFAIK, NethServer uses the same SSL Cert for almost everything (Problems with Cockpit & NethGUI…), besides which, there’s no option to add in a Cert just for one service (like Smarthost) in any of the GUIs… ![]()
One Option for your environment:
You CAN create a Cert in MS AD, as the AD AFAIK comes with a built in CA (Like OPNsense has).
It’s NOT OpenSource, but can create a usable Cert eg for Mac or Linux, so why not try that out?
The CA is accessible, both NethServers would use that CA / SSL-Cert, so it should work…
I can’t really help you there, as it’s been a few years since I last needed to create Certs on MS-AD… But Google should be able to give pointers… ![]()
My 2 cents
Andy
I didn’t read the whole thread, but I can suggest a simple configuration.
If you have 2 servers inside the same LAN, and server A (client) should relay through machine B (mail server) you can:
- go to server B and inside the “Relay” page add the IP of server A
- got to server A and configure B as the relay server
Thanks @giacomo,
I tried this too, but get the same certificate error, I fear, I have to create the certificate at the windows AD as @Andy_Wismer said.
DNS validation is your friend here.
I’m pretty sure you can do it without TLS, at least using a template-custom.
Maybe @stephdl already tried something similar.
Sorry to have no time to read this full thread but maybe you are searching a s/bad/difficult/ solution
I do have some servers myself and all send emails to admin@domain.com, you just have to set the root email in the setting cockpit page with the email of admin@domain.com and use a smarthost to send email for your server.
I do not understand what is the issue :-?
Hi @stephdl,
thanks for your answer
The issue is a curl certificate error if I try to use the smarthost.
I tried this, then smarthost can’t connect because a missing authentication. I think mailserver expects a secure connection. Perhaps somebody can tell me how to disable this.
You issue is really simple, your smarthost is not compatible with nethserver, if you cannot pass the validation please use another smtp smarthost
You can use only smarttls, ssl over 465 is not supported
The smarthost is another nethserver, I hope it will be compatible ![]()
Then we need to launch the api action in the terminal to understand what it occurs but trust me it works
What do you mean, how should I do this?
Not at home sorry
When you try to validate your settings you send a rest api to the server so open the developer webtool console by pressing F12 in your laptop and copy and paste the command you send by pressing the test setting button to your server terminal
Thanks for your input, here is the output 
[root@project ~]# echo '{"action":"test-smarthost","SmartHostName":"groupware.jonas.local","SmartHostPort":"587","SmartHostUsername":"mtraeumner@jonas.local","SmartHostPassword":"MyPassword","SmartHostTlsStatus":true}' | /usr/bin/sudo /usr/libexec/nethserver/api/system-settings/execute | jq
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0* About to connect() to groupware.jonas.local port 587 (#0)
* Trying 192.168.46.5...
* Connected to groupware.jonas.local (192.168.46.5) port 587 (#0)
< 220 groupware.jonas.local ESMTP Postfix
> EHLO project
< 250-groupware.jonas.local
< 250-PIPELINING
< 250-SIZE 20000000
< 250-VRFY
< 250-ETRN
< 250-STARTTLS
< 250-ENHANCEDSTATUSCODES
< 250-8BITMIME
< 250 DSN
> STARTTLS
< 220 2.0.0 Ready to start TLS
* Initializing NSS with certpath: sql:/etc/pki/nssdb
* CAfile: /etc/pki/tls/certs/ca-bundle.crt
CApath: none
* Server certificate:
* subject: L=MyCity,C=DE,OU=Main,OID.2.5.29.17=jonas.local,E=it@My-MailProvider.de,ST=SomeState,O=My Business,CN=groupware.jonas.local
* start date: Jul 13 06:40:27 2020 GMT
* expire date: Jul 11 06:40:27 2030 GMT
* common name: groupware.jonas.local
* issuer: L=MyCity,C=DE,OU=Main,OID.2.5.29.17=jonas.local,E=it@MyMailProvider.de,ST=SomeState,O=Jonas GmbH,CN=groupware.jonas.local
* NSS error -8172 (SEC_ERROR_UNTRUSTED_ISSUER)
* Peer's certificate issuer has been marked as not trusted by the user.
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
* Closing connection 0
curl: (60) Peer's certificate issuer has been marked as not trusted by the user.
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.