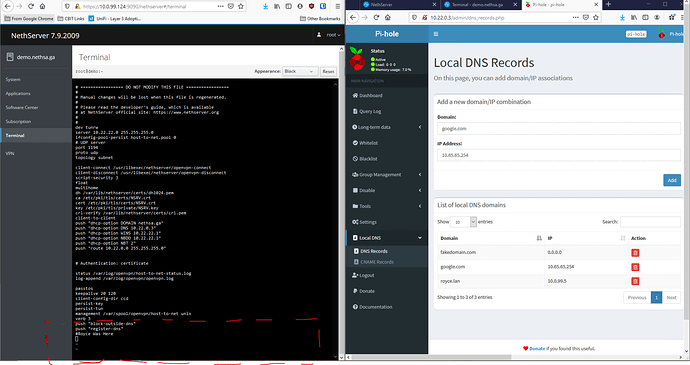
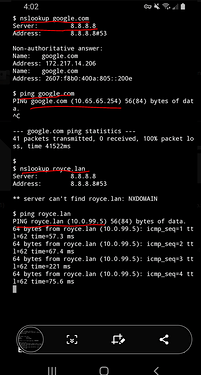
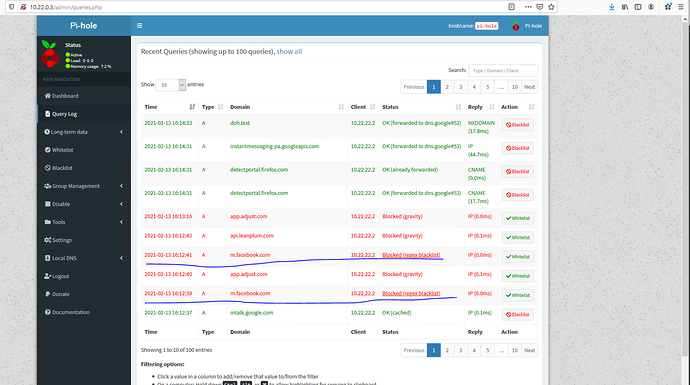
Today I want to continue tinkering with my LAN/VPN configuration:
Objectives:
- all clients dialed in via VPN should use Pihole as DNS resolver
- should not only the VPN client but the entire end device be assigned an IP from the address range of the VPN incl. DNS server via DHCP?
Current state:
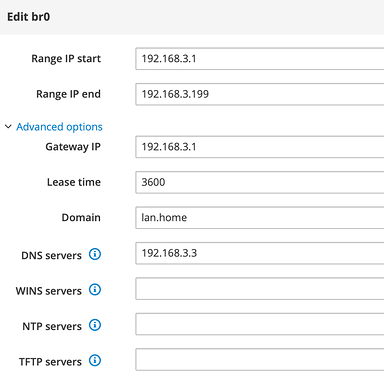
- LAN: 192.168.3.0/24
- Gateway: 191.683.1
- DNS-Server (piHole) 192.168.3.3
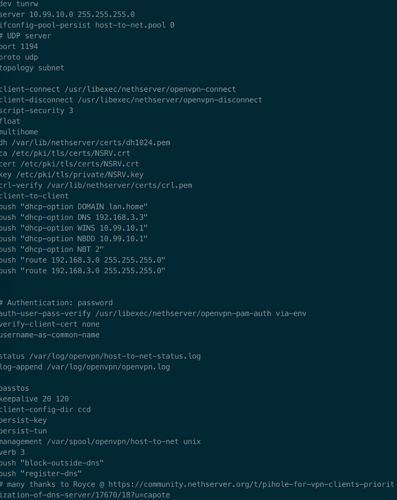
Roadwarrior-VPN:
- Auth-Mode: User/PW
- Network: 10.99.10.0
- Netmask: 255.255.255.0
- Contact this server on public IP / host: vpn.mydomain.de (the IP is regularly updated with my dynamic IP of my router)
- Protocol: UDP
- Port: 1194
- Compression: no
- Digest: Auto
- Cipher: Auto
- Enforce a minimum TLS version: Auto
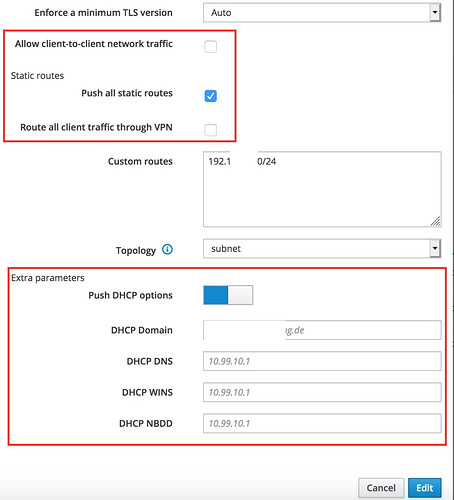
- Allow client-to-client network traffic: yes
Static routes:
- Push all static routes: yes
- Route all client traffic through VPN: n0
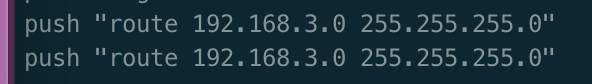
- Custom routes: 192.168.3.0/24
- Topology: subnet
Extra parameters
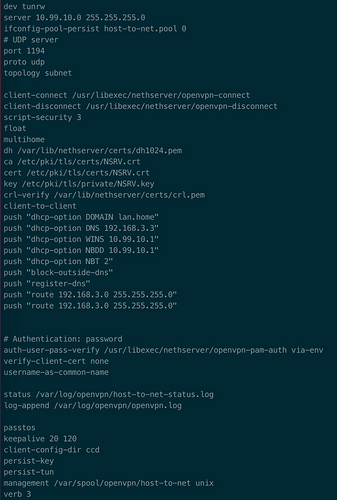
- Push DHCP options: yes
- DHCP Domain: lan.home
- DHCP DNS: 192.168.3.3
- DHCP WINS:
- DHCP NBDD:
Account configuration:
DHCP configuration
- Reserved IP: 10.99.10.31
Remote network:
- VPN Remote network:
- VPN Remote netmask:
Local Client Configuration:
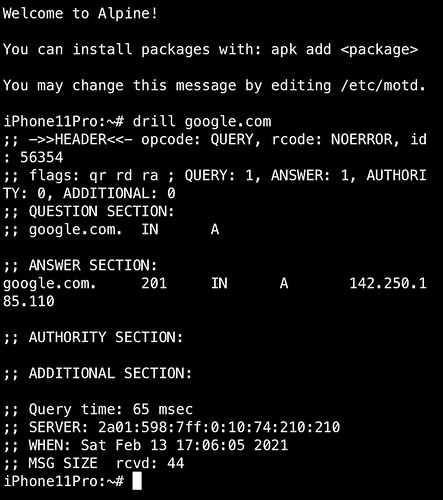
Network connection established via personal hotspot of my iPhone
- WAN-IP 80.###.##.##
- LAN-IP : 172.20.10.6
- DNS: 172.20.10.1
Szenario 1
VPN-Client (macOS): Viscosity
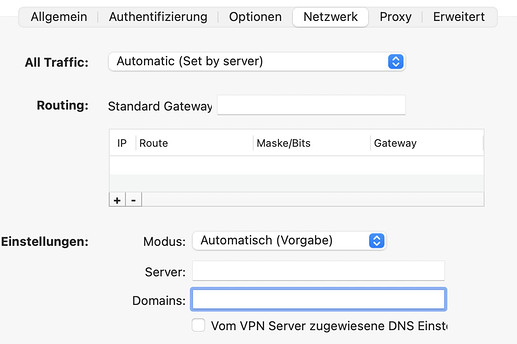
Connection settings: Auto
Serer:
Domains:
DNS settings assigned to the VPN server: yes
Connection-Log:
2021-02-11 14:21:39: Viscosity Mac 1.9.1 (1563)
2021-02-11 14:21:39: Viscosity OpenVPN Engine Started
2021-02-11 14:21:39: Running on macOS 11.2.1
2021-02-11 14:21:39: ---------
2021-02-11 14:21:39: State changed to Connecting
2021-02-11 14:21:39: Checking reachability status of connection...
2021-02-11 14:21:39: Connection is reachable. Starting connection attempt.
2021-02-11 14:21:39: OpenVPN 2.4.10 x86_64-apple-darwin [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [MH/RECVDA] [AEAD] built on Jan 18 2021
2021-02-11 14:21:39: library versions: OpenSSL 1.1.1i 8 Dec 2020, LZO 2.10
2021-02-11 14:21:39: Resolving address: vpn.mydomainde
2021-02-11 14:21:39: Valid endpoint found: 93.###.##.##:1194:udp
2021-02-11 14:21:39: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
2021-02-11 14:21:39: TCP/UDP: Preserving recently used remote address: [AF_INET]93.###.##.##:1194
2021-02-11 14:21:39: UDP link local: (not bound)
2021-02-11 14:21:39: UDP link remote: [AF_INET]93.###.##.##:1194
2021-02-11 14:21:39: State changed to Authenticating
2021-02-11 14:21:40: [NethServer] Peer Connection Initiated with [AF_INET]93.###.##.##:1194
2021-02-11 14:21:41: Opened utun device utun10
2021-02-11 14:21:41: /sbin/ifconfig utun10 delete
2021-02-11 14:21:41: NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure
2021-02-11 14:21:41: /sbin/ifconfig utun10 10.99.10.31 10.99.10.31 netmask 255.255.255.0 mtu 1500 up
2021-02-11 14:21:41: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2021-02-11 14:21:41: Initialization Sequence Completed
**2021-02-11 14:21:41: DNS mode set to Split**
2021-02-11 14:21:41: WARNING: Split DNS is being used however no DNS domains are present. The DNS server/s for this connection may not be used. For more information please see: https://www.sparklabs.com/support/kb/article/warning-split-dns-is-being-used-however-no-dns-domains-are-present/
2021-02-11 14:21:41: State changed to Connected
Outcome: negative
- macOS-IP: IP of my mobile IPS
- DNS-Server: 72.20.10.1
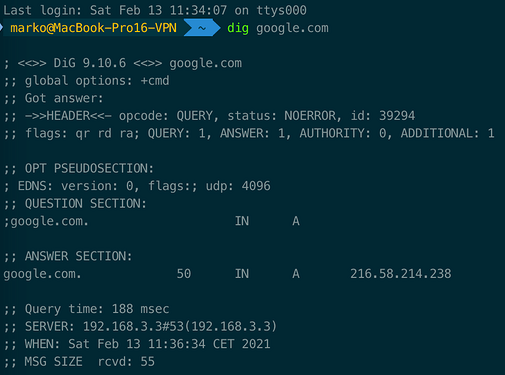
- DIG anything: ;; SERVER: 172.20.10.1#53(172.20.10.1)
- Ping 192.168.3.3: ok
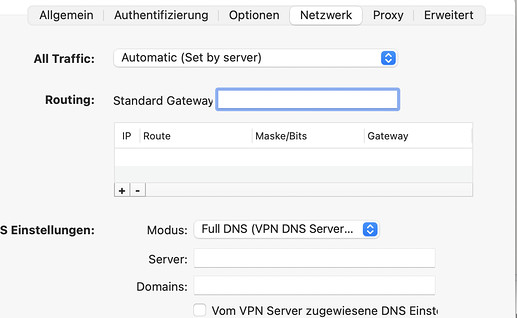
Szenario 2
VPN-Client (macOS): Viscosity
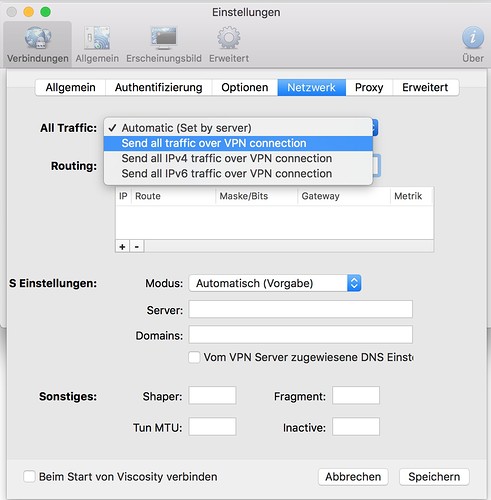
Connection settings: Full-DNS (use VPN-DNS-Server)
Server:
Domains:
DNS settings assigned to the VPN server: yes
2021-02-11 14:27:18: Viscosity Mac 1.9.1 (1563)
2021-02-11 14:27:18: Viscosity OpenVPN Engine Started
2021-02-11 14:27:18: Running on macOS 11.2.1
2021-02-11 14:27:18: ---------
2021-02-11 14:27:18: State changed to Connecting
2021-02-11 14:27:18: Checking reachability status of connection...
2021-02-11 14:27:18: Connection is reachable. Starting connection attempt.
2021-02-11 14:27:18: OpenVPN 2.4.10 x86_64-apple-darwin [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [MH/RECVDA] [AEAD] built on Jan 18 2021
2021-02-11 14:27:18: library versions: OpenSSL 1.1.1i 8 Dec 2020, LZO 2.10
2021-02-11 14:27:18: Resolving address: vpn.mydomainde
2021-02-11 14:27:18: Valid endpoint found: 93.###.##.##:1194:udp
2021-02-11 14:27:18: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
2021-02-11 14:27:18: TCP/UDP: Preserving recently used remote address: [AF_INET]93.###.##.##:1194
2021-02-11 14:27:18: UDP link local: (not bound)
2021-02-11 14:27:18: UDP link remote: [AF_INET]93.###.##.##:1194
2021-02-11 14:27:18: State changed to Authenticating
2021-02-11 14:27:19: [NethServer] Peer Connection Initiated with [AF_INET]93.###.##.##:1194
2021-02-11 14:27:19: Opened utun device utun10
2021-02-11 14:27:19: /sbin/ifconfig utun10 delete
2021-02-11 14:27:19: NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure
2021-02-11 14:27:19: /sbin/ifconfig utun10 10.99.10.31 10.99.10.31 netmask 255.255.255.0 mtu 1500 up
2021-02-11 14:27:19: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2021-02-11 14:27:19: Initialization Sequence Completed
**2021-02-11 14:27:19: DNS mode set to Full**
2021-02-11 14:27:20: State changed to Connected
Outcome: negative
- macOS-IP: IP of my mobile IPS
- DNS-Server: 72.20.10.1
- DIG anything: ;; connection timed out; no servers could be reached
- Ping 192.168.3.3: ok
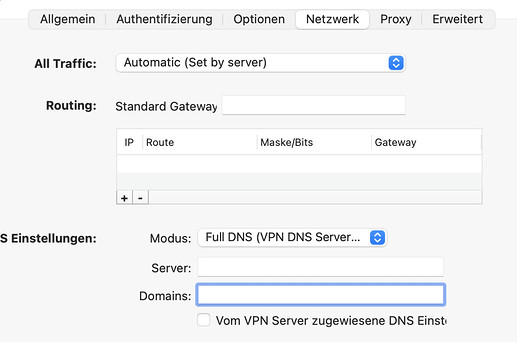
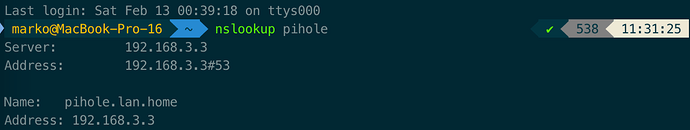
Szenario 3
VPN-Client (macOS): Viscosity
Connection settings: Full-DNS (use VPN-DNS-Server)
Server: 192.168.3.3
Domains: lan.home
DNS settings assigned to the VPN server: yes
2021-02-11 14:32:39: Viscosity Mac 1.9.1 (1563)
2021-02-11 14:32:39: Viscosity OpenVPN Engine Started
2021-02-11 14:32:39: Running on macOS 11.2.1
2021-02-11 14:32:39: ---------
2021-02-11 14:32:39: State changed to Connecting
2021-02-11 14:32:39: Checking reachability status of connection...
2021-02-11 14:32:39: Connection is reachable. Starting connection attempt.
2021-02-11 14:32:39: OpenVPN 2.4.10 x86_64-apple-darwin [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [MH/RECVDA] [AEAD] built on Jan 18 2021
2021-02-11 14:32:39: library versions: OpenSSL 1.1.1i 8 Dec 2020, LZO 2.10
2021-02-11 14:32:39: Resolving address: vpn.mydomainde
2021-02-11 14:32:39: Valid endpoint found: 93.###.##.##:1194:udp
2021-02-11 14:32:39: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
2021-02-11 14:32:39: TCP/UDP: Preserving recently used remote address: [AF_INET]93.###.##.##:1194
2021-02-11 14:32:39: UDP link local: (not bound)
2021-02-11 14:32:39: UDP link remote: [AF_INET]93.###.##.##:1194
2021-02-11 14:32:39: State changed to Authenticating
2021-02-11 14:32:40: [NethServer] Peer Connection Initiated with [AF_INET]93.###.##.##:1194
2021-02-11 14:32:40: Opened utun device utun10
2021-02-11 14:32:40: /sbin/ifconfig utun10 delete
2021-02-11 14:32:40: NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure
2021-02-11 14:32:40: /sbin/ifconfig utun10 10.99.10.31 10.99.10.31 netmask 255.255.255.0 mtu 1500 up
2021-02-11 14:32:40: WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this
2021-02-11 14:32:40: Initialization Sequence Completed
**2021-02-11 14:32:40: DNS mode set to Full**
2021-02-11 14:32:40: State changed to Connected
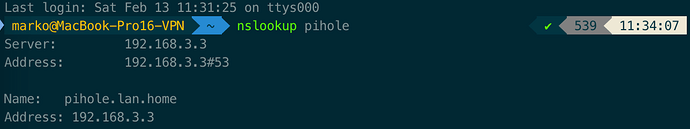
Outcome: positve
- macOS-IP: IP of my mobile IPS
- DNS-Server: DNS-Server of my IPS 72.20.10.1
- DIG anything: ;; SERVER: 192.168.3.3#53(192.168.3.3)
What can I do, so that my server provides all clients with a configuration that mandates the use of the VPN DNS server (Pihole).
Sincereley, Marko