NethServer Version: 7
Module: let’s encrypt, virtual hosts
Hi all,
this is not a “problem support request”. It is more to get some idea of “best practice” and “possibilities” for let’s encrypt (I will call “LE” in the following). Therefor I think It is a good idea to summarize my experiences and derived questions.
Initially, I had just one LE certificate for two or three domain names:
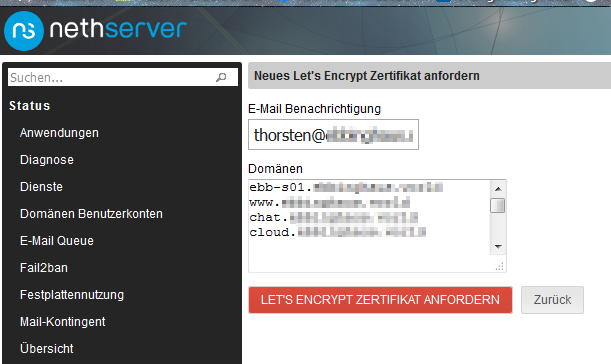
This grew up to say 10 or 12 domain names for one certificate. I accept this as this as there was no doubt for me to create just one certificate for all. I shared arround the certificate by simple copy scipts as described here:
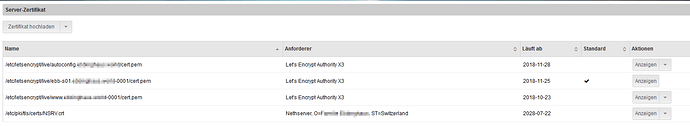
For some reson - honestly, I can not remember how I made it - i do have now three certifcates:
I am quite shure I managed this during set up of email autoconfig:
Q: Is this in generall possible within nethserver to create more than one LE Certificate?
Q: If so, how do I do that, e.g. by providing different e-mails?
Q: Will all of these certificates be updated after three month?
Currently, I do no only on module, virtualhosts, for which I can select the certificate to be used. This works very nice, e.g. I used the www certificate for the www vhost (2nd from bottom).
Q: Are there any other modules for which I can select a specific certificate (reverse proxy is vhost, isn’t it?)
Q: is it possible to use several / single certificates within nethserver
Additionally, I copied the certficate to the radius \etc\raddb\certificates\ directory and linked it to the experimentals nethserver-radius module, see here:
The client (Windows 7) gets the certicate, but considers it as invalid.
Q: How can I share nethserver (and other) CAs to (windows, iphone) clients, is there any option to do this by AD policies?
TIA
Thorrsten