Hi,
I’m using NS8 on Debian together With Nethsecurity.
Is there maybe a setting not correct in my setup ?
--------- 2 ---------
How to i get the token for Crowdsec. On the website of Crowdsec i cannot find this, or is it only for paid users ?
--------- 3 ---------
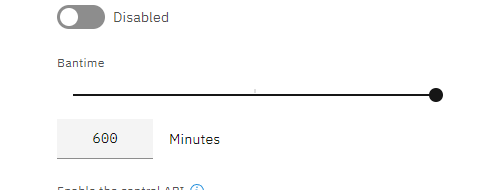
Is it possible to extend the ban time.
dnutan
October 7, 2024, 7:46pm
2
Recently I’ve seen a report of a bug regarding crowdsec and nextcloud (an older one with other modules: Crowdsec not banning ) but unaware if something similar happens with postfix.ns8-crowdsec readme .
Maybe a run of crowdsec’s cscli explain can bring some light on what happens when it processes the postfix log.
runagent -m crowdsec1 cscli explain --file "dontknowthepathtopostfixlogfile" --type <typecorrespondingtopostfix-maybe-syslog-or-maybe-not> # or --log instead of file to specify a line
…or similar.
extended ban time: should be possible form command line but better if devs tweak the UI, if your request is considered valid.
You can sign-up for free (see pricing for feature comparison) and get your enrollment key (creating an account on https://app.crowdsec.net )
stephdl
October 7, 2024, 8:09pm
3
Interesting topic
Fai2lban is became stronger bugs after bugs because people has tested it and reviewed it
I know it because I started it on my own
Maybe your IP was known and thus tested by hackers but with a new IP you have less popularity … who knows
You have to parse and watch your logs or attempt to do yourself brute force login against your services
stephdl
October 7, 2024, 8:13pm
4
Honestly I do not see much interest, a machine is never bored to do thing again and again. So when the IP will be released a new ban will occur
What is the issue ?
Furthermore crowdsec uses a dynamic bantime so first ban is x minutes, second bans is 2X x minutes etc
LayLow
October 7, 2024, 9:14pm
5
Agree, interested in motivation.
Every attack is a change, so why don’t try to avoid it with a longer periode
Also how much effort is it to change the value in the UI to a large number
stephdl
October 8, 2024, 7:29pm
8
-Search in your log first you will see brute force attempts
-do bad login to smtp and imap/pop3 with thunderbird or use curl to simulate it
stephdl
October 8, 2024, 7:32pm
9
stephdl
October 9, 2024, 12:39pm
11
see last lineR2-pve.rocky9-pve2.org crowdsec1-firewall-bouncer[22478]: time=“2024-10-08T20:06:57Z” level=info msg=“1 decision added”
Oct 08 22:06:56 R2-pve.rocky9-pve2.org postfix/smtpd[23708]: warning: leo-stephdl-dynu-net.stephdl.dynu.net[192.168.13.25]: SASL PLAIN authentication failed: (reason unavailable), sasl_username=stephane
Oct 08 22:06:56 R2-pve.rocky9-pve2.org postfix/smtpd[23708]: lost connection after AUTH from leo-stephdl-dynu-net.stephdl.dynu.net[192.168.13.25]
Oct 08 22:06:56 R2-pve.rocky9-pve2.org postfix/smtpd[23708]: disconnect from leo-stephdl-dynu-net.stephdl.dynu.net[192.168.13.25] ehlo=2 starttls=1 auth=0/1 commands=3/4
Oct 08 22:06:56 R2-pve.rocky9-pve2.org rspamd[1934]: (rspamd_proxy) <676bee>; milter; rspamd_milter_process_command: got connection from 192.168.13.25:35806
Oct 08 22:06:56 R2-pve.rocky9-pve2.org rspamd[1934]: (rspamd_proxy) <676bee>; proxy; proxy_milter_finish_handler: finished milter connection
Oct 08 22:06:56 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:06:56Z" level=info msg="Ip 192.168.13.25 performed 'crowdsecurity/postfix-spam' (7 events over 19.250864434s) at 2024-10-08 20:06:56.638141212 +0000 UTC"
Oct 08 22:06:56 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:06:56Z" level=info msg="(localhost/crowdsec) crowdsecurity/postfix-spam by ip 192.168.13.25 : 8m ban on Ip 192.168.13.25"
Oct 08 22:06:56 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:06:56Z" level=info msg="127.0.0.1 - [Tue, 08 Oct 2024 20:06:56 UTC] \"POST /v1/alerts HTTP/1.1 201 2.635751ms \"crowdsec/v1.6.3-4851945a-docker\" \""
Oct 08 22:06:57 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:06:57Z" level=info msg="127.0.0.1 - [Tue, 08 Oct 2024 20:06:57 UTC] \"GET /v1/decisions/stream HTTP/1.1 200 5.757288ms \"crowdsec-firewall-bouncer/v0.0.28-debian-pragmatic-af6e7e25822c2b1a02168b99ebbf8458bc6728e5\" \""
Oct 08 22:06:57 R2-pve.rocky9-pve2.org crowdsec1-firewall-bouncer[22478]: time="2024-10-08T20:06:57Z" level=info msg="1 decision added"
curl -k -n --ssl-reqd --url "smtp://rocky9-pve2.org:587" --mail-from stephane@de-labrusse.fr --mail-rcpt stephane@rocky9-pve2.org --upload-file /dev/null -u 'stephane@rocky9-pve2.org':'password' -v
1 Like
stephdl
October 9, 2024, 1:06pm
12
see the last line
wall-bouncer/v0.0.28-debian-pragmatic-af6e7e25822c2b1a02168b99ebbf8458bc6728e5" ""R2-pve.rocky9-pve2.org crowdsec1-firewall-bouncer[22478]: time=“2024-10-08T20:36:57Z” level=info msg=“1 decision added”
Oct 08 22:36:47 R2-pve.rocky9-pve2.org samba-dc[1894]: Auth: [LDAP,simple bind/TLS] user [ROCKY9-PVE2]\[ldapservice@ad.rocky9-pve2.org] at [Tue, 08 Oct 2024 20:36:47.451935 UTC] with [Plaintext] status [NT_STATUS_OK] workstation [DC1] remote host [ipv4:192.168.12.111:47818] became [ROCKY9-PVE2]\[ldapservice] [S-1-5-21-4246221167-834095538-3919285230-1103]. local host [ipv4:192.168.12.111:636]
Oct 08 22:36:47 R2-pve.rocky9-pve2.org samba-dc[1894]: TLS ../../source4/lib/tls/tls_tstream.c:1378 - Decryption has failed.
Oct 08 22:36:47 R2-pve.rocky9-pve2.org samba-dc[1894]: TLS ../../source4/lib/tls/tls_tstream.c:1378 - Decryption has failed.
Oct 08 22:36:47 R2-pve.rocky9-pve2.org samba-dc[1894]: TLS ../../source4/lib/tls/tls_tstream.c:1378 - Decryption has failed.
Oct 08 22:36:47 R2-pve.rocky9-pve2.org samba-dc[1894]: Auth: [LDAP,simple bind/TLS] user [ROCKY9-PVE2]\[CN=stephane,CN=Users,DC=ad,DC=rocky9-pve2,DC=org] at [Tue, 08 Oct 2024 20:36:47.496345 UTC] with [Plaintext] status [NT_STATUS_WRONG_PASSWORD] workstation [DC1] remote host [ipv4:192.168.12.111:47818] mapped to [ROCKY9-PVE2]\[stephane]. local host [ipv4:192.168.12.111:636]
Oct 08 22:36:47 R2-pve.rocky9-pve2.org dovecot[23491]: auth-worker(88): conn unix:auth-worker (pid=86,uid=90): auth-worker<2>: ldap(stephane,192.168.13.25,<xjxoGP0jmIfAqA0Z>): Password mismatch (for LDAP bind)
Oct 08 22:36:49 R2-pve.rocky9-pve2.org dovecot[23491]: imap-login: Disconnected: Connection closed (auth failed, 1 attempts in 6 secs): user=<stephane>, method=PLAIN, rip=192.168.13.25, lip=192.168.12.111, TLS, session=<xjxoGP0jmIfAqA0Z>
Oct 08 22:36:49 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:36:49Z" level=info msg="Ip 192.168.13.25 performed 'crowdsecurity/dovecot-spam' (4 events over 8.498841924s) at 2024-10-08 20:36:49.387145739 +0000 UTC"
Oct 08 22:36:49 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:36:49Z" level=info msg="(localhost/crowdsec) crowdsecurity/dovecot-spam by ip 192.168.13.25 : 12m ban on Ip 192.168.13.25"
Oct 08 22:36:49 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:36:49Z" level=info msg="127.0.0.1 - [Tue, 08 Oct 2024 20:36:49 UTC] \"POST /v1/alerts HTTP/1.1 201 2.491463ms \"crowdsec/v1.6.3-4851945a-docker\" \""
Oct 08 22:36:50 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:36:50Z" level=info msg="127.0.0.1 - [Tue, 08 Oct 2024 20:36:50 UTC] \"GET /v1/heartbeat HTTP/1.1 200 211.855µs \"crowdsec/v1.6.3-4851945a-docker\" \""
Oct 08 22:36:54 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:36:54Z" level=info msg="Signal push: 1 signals to push"
Oct 08 22:36:57 R2-pve.rocky9-pve2.org crowdsec1[22917]: time="2024-10-08T20:36:57Z" level=info msg="127.0.0.1 - [Tue, 08 Oct 2024 20:36:57 UTC] \"GET /v1/decisions/stream HTTP/1.1 200 6.620503ms \"crowdsec-firewall-bouncer/v0.0.28-debian-pragmatic-af6e7e25822c2b1a02168b99ebbf8458bc6728e5\" \""
Oct 08 22:36:57 R2-pve.rocky9-pve2.org crowdsec1-firewall-bouncer[22478]: time="2024-10-08T20:36:57Z" level=info msg="1 decision added"
curl -kv imaps://stephane:password@rocky9-pve2.org
MadPatrick
October 10, 2024, 5:06pm
13
Thanks guys. Still not succeeded in a good test, but will try it again
I see the following error in the log
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.287282692Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="could not acquire work: context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.287305384Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="could not acquire work: context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.287328153Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="could not acquire work: context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.287344035Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="could not acquire work: context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.288135147Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.28821734Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.288277671Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.291205054Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="could not acquire work: context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.291293837Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="could not acquire work: context canceled"
2024-10-10T19:04:03+02:00 [1:loki1:loki-server] level=error ts=2024-10-10T17:04:03.291327914Z caller=retry.go:73 org_id=fake traceID=5a7721e0b742f734 msg="error processing request" try=0 query="{node_id=\"1\"} | json syslog_id=\"SYSLOG_IDENTIFIER\",message=\"MESSAGE\" | line_format \"[{{.node_id}}:{{.module_id}}:{{.syslog_id}}] {{.message}}\" |= \"crowd\"" err="could not acquire work: context canceled"
What is ithis ?
LayLow
October 15, 2024, 6:21pm
14
I think this has been overlooked in the mix of questions.
Form the CLI it can be done as described here .
2 Likes
MadPatrick
October 15, 2024, 7:12pm
15
Thanks. That helps.
MadPatrick
October 16, 2024, 5:43pm
16
An other question which is a bit on topic
During installation I remove the Crowdsec instance to start a new clean instance
Is it possible to rename the instance to Crowdsec1
The question is as old as Nethserver 8 itself.
Here yo can find the answer.