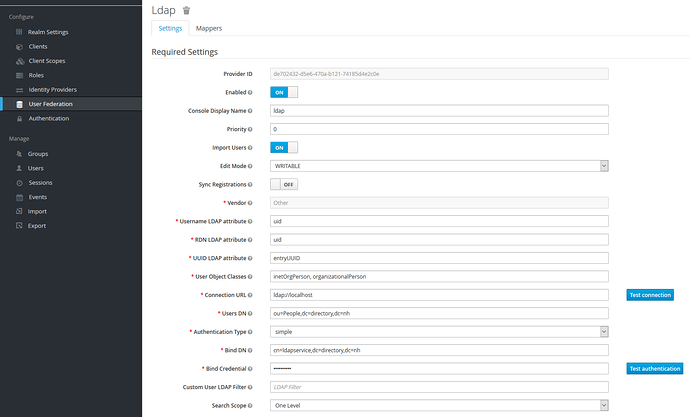
It seems to be just a connection to LDAP/AD:
https://www.keycloak.org/about.html
I installed it on a Nethserver with local LDAP and it worked, I synced an LDAP user and could login with Google authenticator.
Install steps:
yum install java-1.8.0-openjdk curl
groupadd -r keycloak
useradd -m -d /var/lib/keycloak -s /sbin/nologin -r -g keycloak keycloak
curl https://downloads.jboss.org/keycloak/4.6.0.Final/keycloak-4.6.0.Final.tar.gz -o keycloak.tar.gz
mkdir -p /opt/keycloak/4.6.0
ln -s /opt/keycloak/4.6.0 /opt/keycloak/current
tar -xzf keycloak.tar.gz -C /opt/keycloak/current --strip-components=1
chown keycloak: -R /opt/keycloak
cd /opt/keycloak/current
sudo -u keycloak chmod 700 standalone
cat > /etc/systemd/system/keycloak.service <<EOF
[Unit]
Description=Keycloak
After=network.target
[Service]
Type=idle
User=keycloak
Group=keycloak
ExecStart=/opt/keycloak/current/bin/standalone.sh -b 0.0.0.0
TimeoutStartSec=600
TimeoutStopSec=600
[Install]
WantedBy=multi-user.target
EOF
systemctl daemon-reload
systemctl enable keycloak --now
bin/add-user-keycloak.sh -r master -u admin -p secret123
systemctl restart keycloak
config set fw_keycloak service status enabled TCPPort 8080 access green
signal-event firewall-adjust
Now you can connect to http://nethserver:8080 and login with admin and password secret123.
Here are my ldap settings, just use account-provider-test dump to get your credentials. The default mappings worked.