Thank you for taking the time to test this out,
I would like to know, if there is a way to put it as a proxy like instead of https://nethserver.com:8080 to have it as key.nethserver.com.
I have looked into the mattermost vhost config
VhostConfig
<VirtualHost *:80>
IncludeOptional conf.d/default-virtualhost.inc
<VirtualHost :80>
ServerName key.nethserver.com
RedirectMatch 301 ^(?!/.well-known/acme-challenge/). https://key.nethserver.com
<VirtualHost *:443>
ServerName key.nethserver.com
SSLEngine on
ProxyPreserveHost On
setup the proxy
<Proxy *>
Order allow,deny
Allow from all
Set web sockets
RewriteEngine On
RewriteCond %{REQUEST_URI} /api/v[0-9]+/(users/)?websocket [NC,OR]
RewriteCond %{HTTP:UPGRADE} ^WebSocket$ [NC,OR]
RewriteCond %{HTTP:CONNECTION} ^Upgrade$ [NC]
RewriteRule .* ws://127.0.0.1:8080%{REQUEST_URI} [P,QSA,L]
RewriteCond %{DOCUMENT_ROOT}/%{REQUEST_FILENAME} !-f
Force SSL redirect
RewriteCond %{HTTPS} !=on
RewriteRule (.*) https://%{SERVER_NAME}%{REQUEST_URI} [END,QSA,R=permanent]
<LocationMatch “^/api/v(?[0-9]+)/(?users/)?websocket”>
Require all granted
ProxyPass ws://127.0.0.1:8080/api/v%{env:MATCH_APIVERSION}/%{env:MATCH_APIUSERS}websocket
ProxyPassReverse ws://127.0.0.1:8080/api/v%{env:MATCH_APIVERSION}/%{env:MATCH_APIUSERS}websocket
ProxyPassReverseCookieDomain 127.0.0.1 key.nethserver.com
Require all granted
ProxyPass http://127.0.0.1:8080/
ProxyPassReverse http://127.0.0.1:8080/
ProxyPassReverseCookieDomain 127.0.0.1 key.nethserver.com
I saved it in the /etc/httpd/conf, restarted the http server.
and I also used these:
$ sudo -u keycloak ./bin/jboss-cli.sh ‘embed-server,/subsystem=undertow/server=default-server/http-listener=default:write-attribute(name=proxy-address-forwarding,value=true)’
$ sudo -u keycloak ./bin/jboss-cli.sh ‘embed-server,/socket-binding-group=standard-sockets/socket-binding=proxy-https:add(port=443)’
$ sudo -u keycloak ./bin/jboss-cli.sh ‘embed-server,/subsystem=undertow/server=default-server/http-listener=default:write-attribute(name=redirect-socket,value=proxy-https)’
But it seems not to work,
I also opened the ports 8080 on my router and in NS config.
No luck.
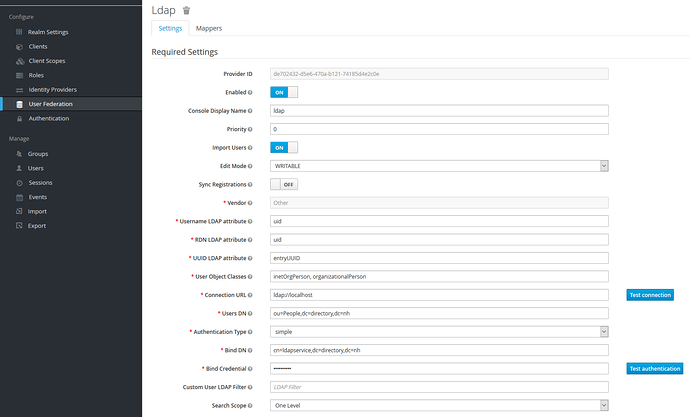
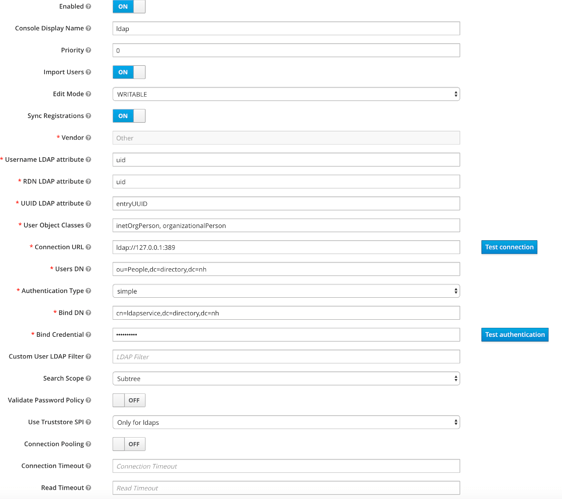
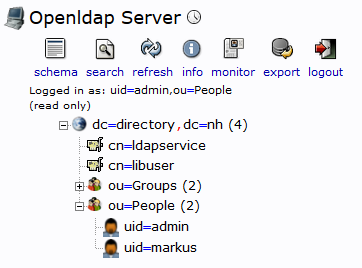
I noticed that keycloak config for the ldap doesn’t work when it not on the same network,
Lastly, could you let me know how did you manage to get the google authenticator working?
With my best regards