NethServer Version: 7.8
Module: IPsec VPN
tl;dr
My Neth server can’t route traffic over an IPsec VPN connection I’ve established through the GUI to my pfSense box.
Background/status
In trying to troubleshoot my backup performance issues, @Andy_Wismer suggested testing over an IPsec VPN connection, rather than the OpenVPN connection I’ve been using. Once I got the connection set up (and TFM is no help at all in this), I see it’s sometimes (though not consistently) showing better performance on iperf3, but it isn’t able to reach hosts on my LAN over that connection. Hosts on my LAN can ping it, run iperf3 against it, and even access the web GUI via the IPsec VPN connection, but the Neth box isn’t able to initiate any connection to hosts on my LAN over this connection.
Configuration
My Neth server is hosted in a Contabo VPS. Its “real” interface (with the public IP address assigned by Contabo) is Red, and I’ve created a dummy interface of dummy0 with an IP of 192.168.4.1/24, designating it green.
I have a pfSense router at home, and my home LAN is on 192.168.1.0/24. The router creates a separate subnet for OpenVPN on 192.168.3.0/24. I’ve used the router’s interface to create a connection profile for Neth at 192.168.3.100/24, dropped that .ovpn file into /etc/openvpn/client/pfsense.conf, and enabled the connection with systemctl enable --now openvpn-client@pfsense. (Doing this through the GUI would have been much trickier; last I checked the GUI didn’t support uploading the standard .ovpn config file, but instead required some .json thing that only another Neth server would generate.) That connection has been working well for as long as I’ve been running the Neth server there.
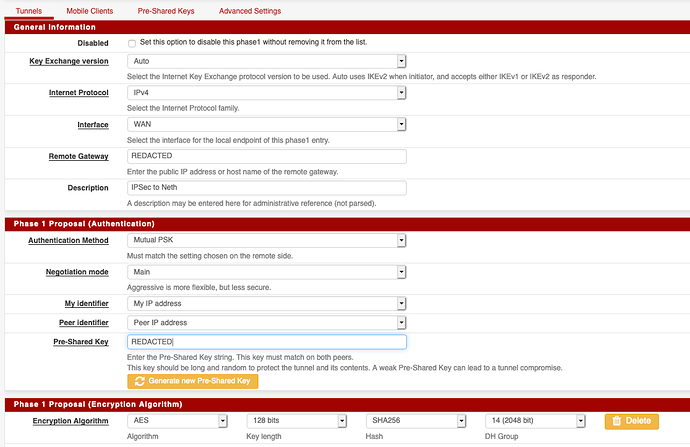
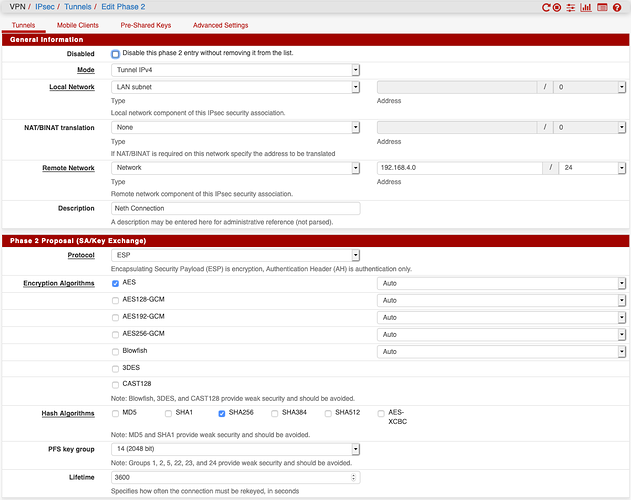
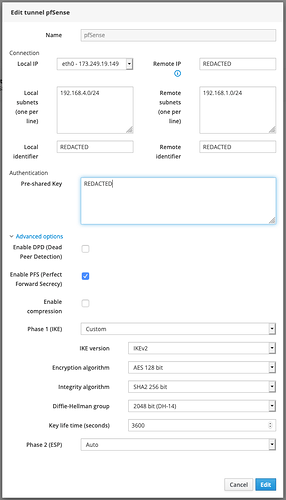
Then came IPsec. Compared to OpenVPN, IPsec is a pain to configure. There are about a dozen settings, they all need to match between local and remote (including, critically, the local and remote identifiers, which Neth defaults to completely inappropriate values), there’s no documentation on the Neth end about what settings are expected or supported, and the (much more thorough) pfSense docs recommend settings that Neth doesn’t support at all. But that rant aside, with a bit of experimentation, I got a connection set up.
That connection is configured as a net-to-net tunnel, between 192.168.1.0/24 on my LAN side and 192.168.4.0/24 on the Neth side. And from my LAN side, it seems to be working OK. I can reach the Neth server’s web GUI, I can ping it, I can hit it with iperf3, it’s all good. But not so from the Neth end.
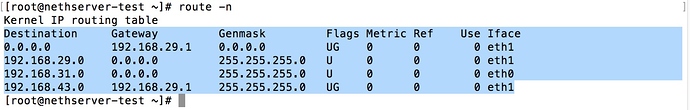
From the Neth end, I can’t reach anything on my LAN–I can’t so much as ping 192.168.1.1, the IP of my pfSense router. Nor can I ping anything else on my LAN, nor can I connect to them in any other way (like using iperf).
Screen shots
pfSense configuration
Neth configuration
Conclusions
From the fact that my LAN can connect to the Neth box, but my Neth box can’t connect to hosts on my LAN, I surmise that there’s a routing problem–my router (and therefore my LAN) knows to route traffic to 192.168.4.0/24 through the IPsec link, but the Neth box doesn’t know to route traffic to 192.168.1.0/24 through that same link. But having determined that, I’m not at all sure how to fix it. Help?