Install Moodle on NS7
Prerequisites:
– NS7
– webserver
– mysql (MariaDB)
Update the server
It’s a good habit to work with an up-to-date installation of your server. NS7 can be updated through software center. Make sure all updates are done.
Install NS7 modules
Install the webserver module
Install the mysql(mariadb) module
Install other prerequisites
Install php through the commandline:
yum install php php-mysql
yum install php-iconv php-mbstring php-curl php-openssl php-tokenizer php-xmlpc php-soap php-ctype php-zip php-gd php-simplexml php-spl php-pcre php-dom php-xml php-intl php-json php-ldap php-pecl-apc php-xmlrpc
Create a mysql database and user for Moodle
The password for mariadb root account is stored in /var/lib/nethserver/secrets/mysql.
cat /var/lib/nethserver/secrets/mysql
Copy the password.
Now open a mysql prompt:
mysql -u root -p
Fill in the copied password and you will be in the Mariadb prompt:
MariaDB [(none)]>
Remember, every command you give in the Mariadb prompt must end with a ;
MariaDB [(none)]> create database moodle;
MariaDB [(none)]> create user 'moodle'@'localhost' identified by 'chooseyourmoodlepassword';
MariaDB [(none)]> grant all privileges on moodle.* to 'moodle'@'localhost';
MariaDB [(none)]> flush privileges;
MariaDB [(none)]> exit
Bye
CD into the wwwroot of your server:
cd /var/www/html
download the latest version of moodle
wget https://download.moodle.org/download.php/direct/stable31/moodle-latest-31.tgz
Extract the tarball
tar -xvf moodle-latest-31.tgz
give rights to the moodle directory to www-data (apache)
chown -R apache:apache /var/www/html/moodle
chmod -R 755 /var/www/html/moodle
Create a data directory for moodle under /var/www/ named as ‘moodledata’ which will be used by moodle.
Change permissions and ownership for that directory to www-data(apache) user. Moodledata can not be in the html directory since it is not considered secure if that directory is externally accessable.
cd /var/www/
mkdir moodledata
chmod -R 755 /var/www/moodledata
chown -R apache:apache /var/www/moodledata
Restart httpd services
systemctl restart httpd
Configure Moodle for first time use
Installation process is over at this stage, lets configure moodle server, open a browser type ip_address/moodle
Follow the instructions in the webinterface:
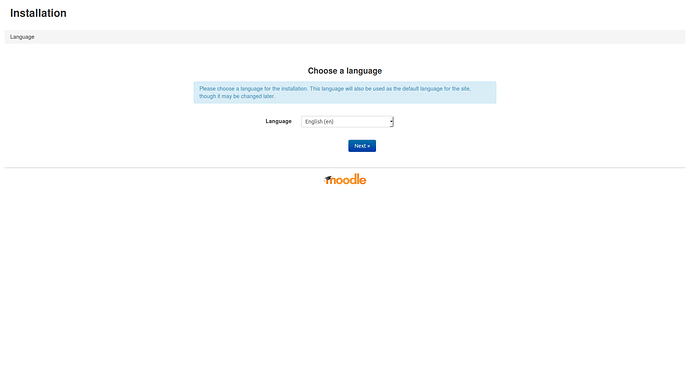
Choose the language for your install prcedure
click Next
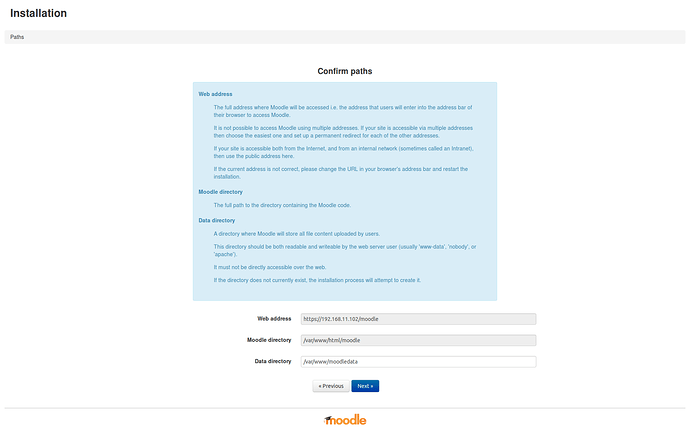
Check the paths. Change if necessary. These are the paths you created during first install.
Click Next
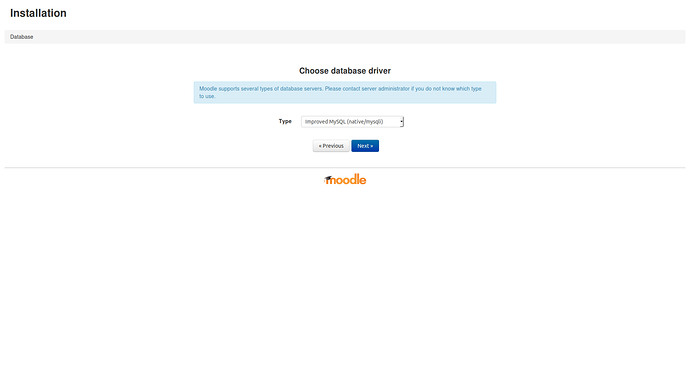
Choose the database driver. Go for the default (mysqli) driver.
Click Next
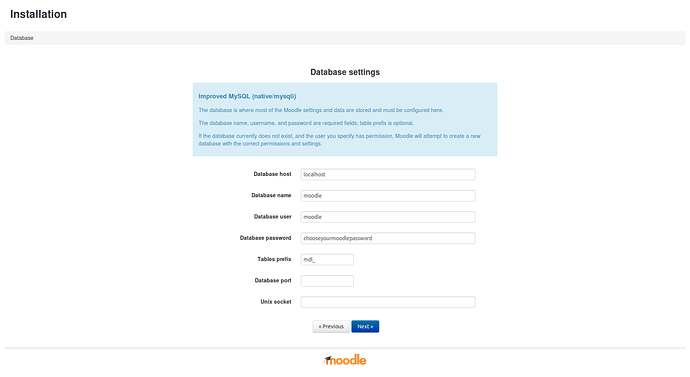
Fill in the database settings. These are the settings you used when creating the database and the database user. If you defined a custom Database port and/or Unix socket, fill those in. For a default NS7 server you can leave those empty.
Click Next
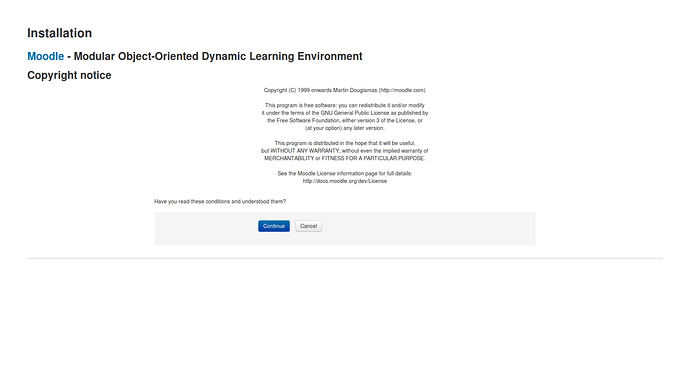
Accept the conditions to use Moodle. You agree Moodle is opensource software and you will act according the GNU GPL3 license or newer.
Click Continue
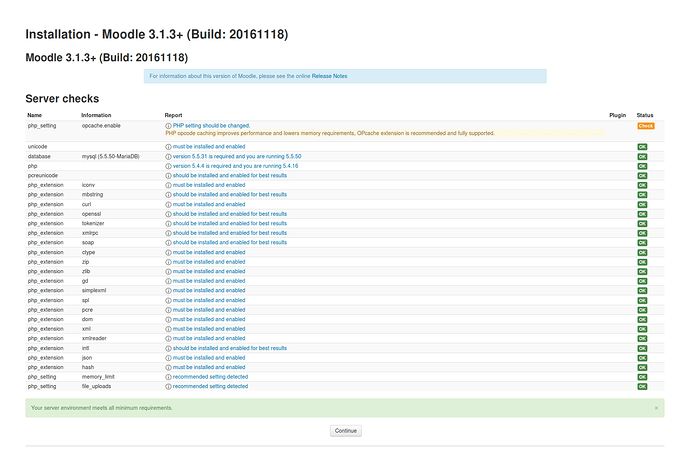
Check if your moodle install meets all prerequisites
Click Continue
If all went well you see a long list of items in green with success
Scroll all the way down and click Next
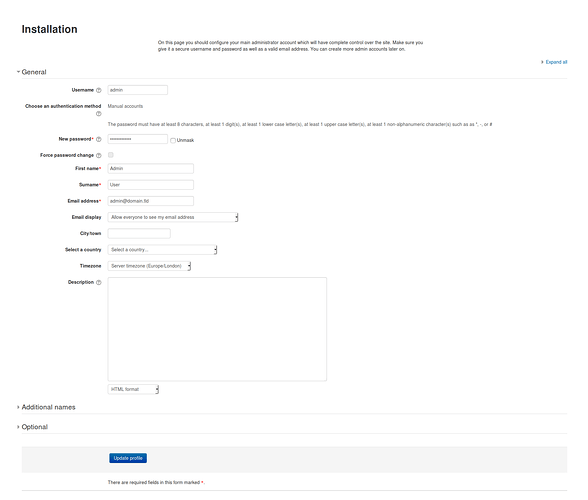
You end up at the admin user profile page. Fill in the required fields:
– New Password
– First Name
– Surname
– Email address
Click update profile
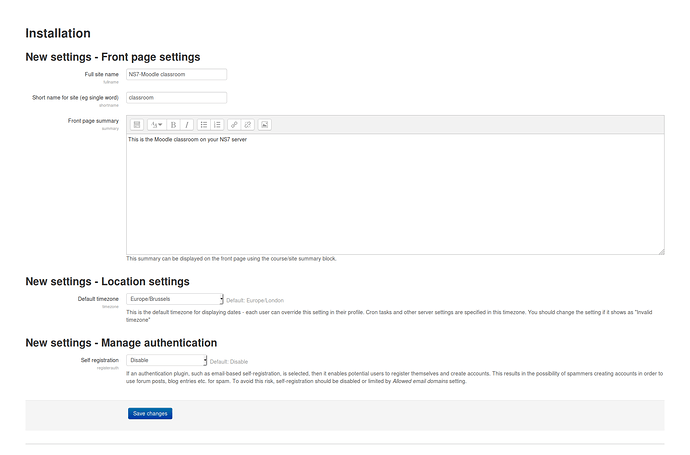
Fill in what you want to show on the Moodle frontpage. Set the Location for your Moodle server.
Authentication will be covered later, since we want to use the account provider of our NS7 server.
Click Save Changes
Your Moodle install is finished. You are now at the Moodle Start Page and logged in as Admin.
At this point there is no account provider configured. I will add both OpenLDAP and Samba4 configurations later.
For more information on Moodle see the Moodle website
Finally, when both OpenLDAP and Samba4 accountproviders are integrated, I could use some help with making this an NS7 RPM package so it can be added to NethForge repository.
Configuring Samba4 AD authentication
To be able to authenticate users with their network credentials, we need a accountprovider to be installed, configured and provisioned.
Install the Samba4 AD account provider from Software center. The Samba4 AD package runs in a separate container. After you installed the module, you have to configure it:
- Give the container an IP address on the same subnet as your green interface.
- This IP address can not be used by another device (including your NS7 server!). Also it is advised to choose an IP address outside the DHCP scope of your DHCP server.
- the green network must be bound to a bridged interface, so that the Linux Container can attach its virtual interface to it.
Change the administrator password.
Create a user to test the settings.
Now head back to the Moodle login page and log in as admin. When logged in, click the site administration link (on a default moodle install on the left of the screen)
Find and click “plugins”
Click Authentication
Click Manage Authentication
On the right you will see a lot of different autentication methods. By default only 2 are active: Manual accounts and No login.
Find LDAP Server and click the crossed eye icon to activate LDAP authentication
LDAP Server will become active. Now click Settings
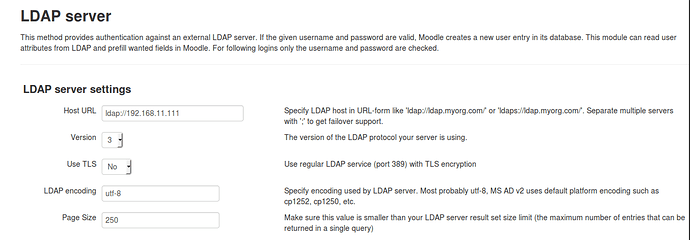
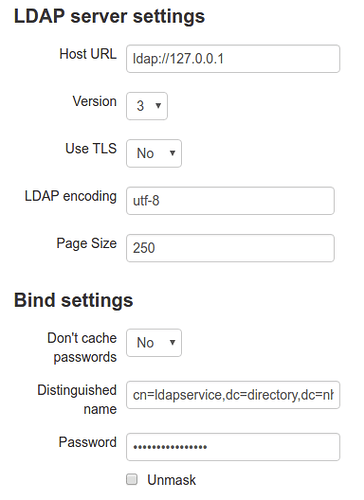
LDAP Server settings:
Host URL: ldap://IPAddress of your Samba4 container
Version: 3
Use TLS: No
LDAP encoding: ulf-8
Page Size: 250
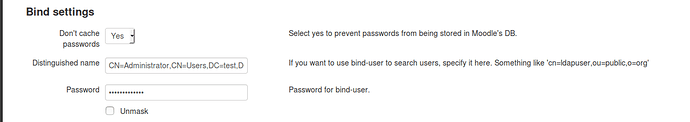
Bind Settings
Don’t cache passwords: yes (you don’t want your administrator password end up in the Moodle database)
Distinguished name: DN of your Administrator account in the Samba4 Tree. In a default NS7 install this is CN=Administrator,CN=Users,DC=yourdomain,DC=TLD
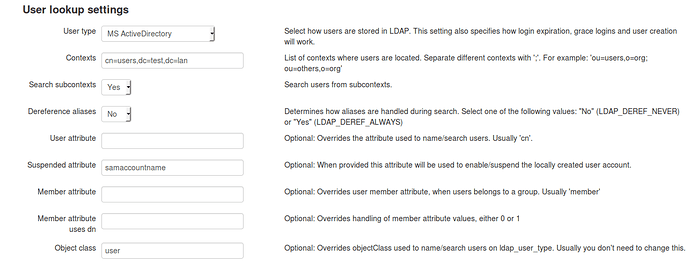
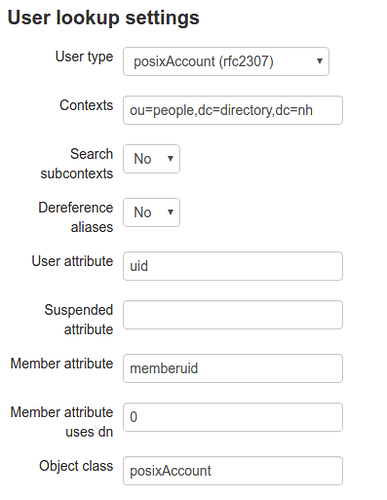
User lookup settings
User type: Active Directory
Contexts: DN of your users ou. cn=users,dc=yourdomain,dc=tld
Search subcontexts: yes
Dereference aliases: No
Suspended attribute: samaccountname
Object class: user
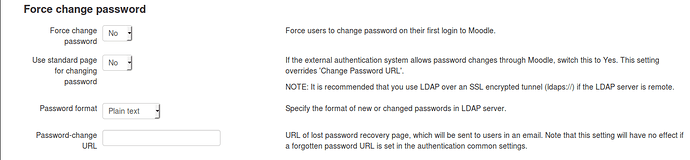
Force change password
Force change password: No (These are Samba4 accounts. Don’t change them in Moodle, rather change them through the NS7 options)
Use standard page for changing password: No (Moodle doesn’t take care of user accounts)
Password format: plain text
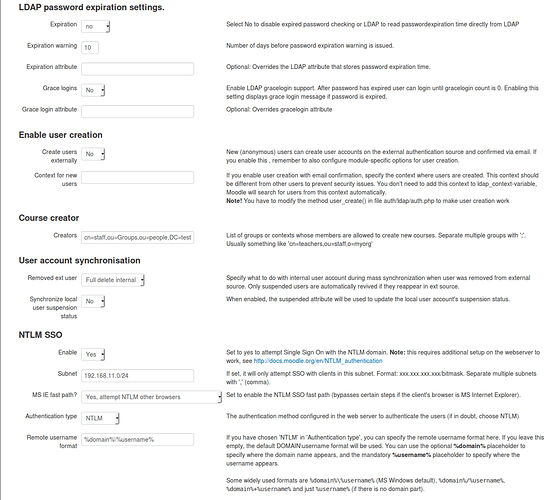
LDAP password expiration settings
Expiration: No
Expiration warning: stick to default, it is not enabled.
Grace Login: No
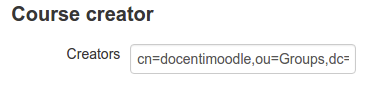
Course Creator:
Here you can define what users and/or groups are automatically enabled as course creators. This is depending how you give permissions to your users in Samba4 AD. For example if you want the staff group as Course creator, and you have staff as an ou in the Users ou:
Example of possible entries: cn=staff,ou=Users,DC=test,DC=lan
User account synchronisation
Removed ext user: Full delete internal
Synchronize local user suspension status: No
NTLM SSO
Enable: Yes
Subnet: 192.168.11.0/24 (subnet of your local LAN)
MS IE fastpath: Yes attempt NTLM other browsers
Authentication type: Kerberos
Remote username format: %domain%%username%
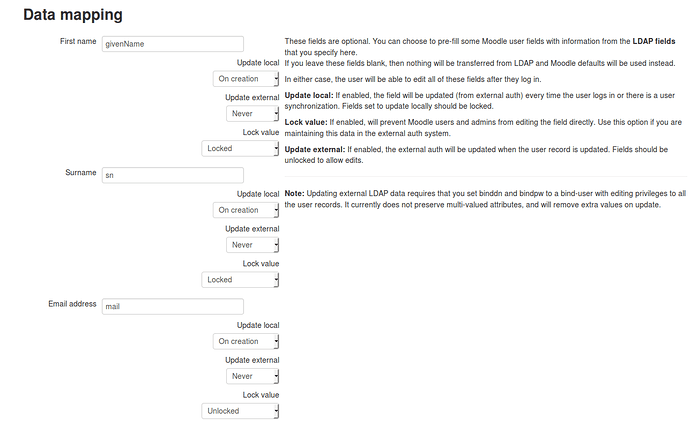
Data mapping
First Name: givenName
Surname: sn
Email address: userPrincipalName
the rest can be left blank.
Scroll down and click save changes.
Log out off Admin user and log in with a Samba4 AD user
If you are logged in with a Samba4 AD account on your pc or laptop, you will be logged in authomagically. Otherwise, log in with your Samba4 AD credentials and you will end up in your Moodle home page.
Enjoy!
To do:
- OpenLDAP authentication
- Create RPM so it can be added to NethForge repository.
Note: Monday 28th of November Moodle 3.2 will be released. For now I think it is best to stick with 3.1 version. As soon Moodle 3.2 is proven stable enough we can consider upgrading the software.

 Maybe in the future I would provide one for Chamilo…
Maybe in the future I would provide one for Chamilo…