Hello everyone,
Continuing from @ghost experiments from this thread, I would like to share an HowTo that will provide a working local webrtc setup with Nextcloud, perhaps someone that is into rpm-making could integrate this in the Nextcloud server-manager installation 
Some parts of the HowTo still need to be confirmed, so please if you have any hint on install paths, best practices, etc, please leave a comment !
I don’t really like the latest trend of using docker for everthing just to ease the setup, as that does not give detailed insight on how things work, so this will be based on building the necessary from sources, no docker:
Tested on Nethserver 7.3
I installed the following modules from software center: OpenLDAP, Backup, Basic Firewall, MariaDB, Nextcloud, and Webserver
Login from the Web GUI with admin/Nethesis,1234 (Nextcloud admin account) and give the LDAP admin account administrator rights
Logout and login again with LDAP admin account and delete the nextcloud built-in admin account
ssh into the server and:
- Install nextcloud-spreedme addon
cd /var/www/html/nextcloud/apps
wget https://github.com/strukturag/nextcloud-spreedme/archive/master.zip
unzip master.zip
mv nextcloud-spreedme-master spreedme
rm master.zip
- Install go 1.7, required for spreed-webrtc server build process, this is built from source as installing go with yum gives version 1.6, which does not suffice, it throws an error related to a function not existing.
cd /tmp/
curl -LO https://storage.googleapis.com/golang/go1.7.linux-amd64.tar.gz
tar -xvf go1.7.linux-amd64.tar.gz
mv go /usr/local
mkdir /opt/goprojects/
export GOROOT=/opt/go/
export GOPATH=/opt/goprojects/
export PATH=$GOPATH/bin:$GOROOT/bin:$PATH
go version (should give output like the following)
go version go1.7 linux/amd64
go env (should give output like the following)
GOARCH=“amd64”
GOBIN=""
GOEXE=""
GOHOSTARCH=“amd64”
GOHOSTOS=“linux”
GOOS=“linux”
GOPATH="/opt/goprojects/"
GORACE=""
GOROOT="/usr/local/go"
GOTOOLDIR="/usr/local/go/pkg/tool/linux_amd64"
CC=“gcc”
GOGCCFLAGS="-fPIC -m64 -pthread -fmessage-length=0"
CXX=“g++”
CGO_ENABLED=“1”
- Install spreed-webrtc server:
cd /opt/ (Is /opt/ the best path for this?)
wget https://github.com/strukturag/spreed-webrtc/archive/master.zip
unzip master.zip
rm master.zip
cd /opt/spreed-webrtc-master/
./autogen.sh
./configure
make
make get
make assets
make binary
From Nextcloud web interface, with admin account, go to the top left menu Admin -> Applications -> Not Enabled -> Spreed.ME, and enable it.
Then from top right admin -> Admin -> Additional Settings -> scroll down to Spreed.ME and click on Generate Spreed WebRTC Config
Copy the generated template to the clipboard and click on Save Settings
Make sure that the SPREED_WEBRTC_BASEPATH parameter is set to /webrtc/ (should be by default)
Go back to ssh and paste the copied template to /opt/spreed-webrtc-master/server.conf (which should not exist by default)
Then create a reverse proxy file for httpd (also doable with reverse proxy module?)
vi /etc/httpd/conf.d/spreed.conf
Paste the following in it (i suppose it could be improved)
<Location /webrtc>
ProxyPass http://127.0.0.1:8080/webrtc
ProxyPassReverse /webrtc
</Location>
<Location /webrtc/ws>
ProxyPass ws://127.0.0.1:8080/webrtc/ws
</Location>
ProxyVia On
ProxyPreserveHost On
RequestHeader set X-Forwarded-Proto 'https' env=HTTPS
Reboot apache:
systemctl restart httpd.service
Start spreed webrtc server
/opt/spreed-webrtc-master/spreed-webrtc-server
(or if you are in the /opt/spreed-webrtc-master/ folder, run ./spreed-webrtc-server)
Now you should be able to access your Nextcloud installation with any LDAP user, and those users will all be able to join Spreed.ME the WebRTC feature
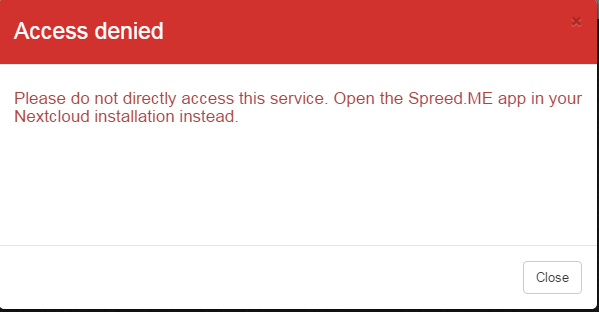
Not accessing this app from Nextcloud, i.e. accessing it directly on http://FQDN/webrtc/, throws an error (which is good):
- Notes:
On Nextcloud settings page (where you generated the config file) you will have a few alerts indicating some files don’t exist. That’s normal, if you want not to be that way you have to create these files manually:
/var/www/html/nextcloud/apps/spreedme/config/config.php
/var/www/html/nextcloud/apps/spreedme/extra/static/config/OwnCloudConfig.js
You can start from an existing template that can be found in:
/var/www/html/nextcloud/apps/spreedme/config/config.php.in
/var/www/html/nextcloud/apps/spreedme/extra/static/config/OwnCloudConfig.js.in
- LIMIT USAGE TO SOME USERS OF NEXTCLOUD (From Nextcloud site, needs testing)
By default, all users who can log in to your Nextcloud installation can also use this app (and Spreed WebRTC).
If you want to limit access to this app (and Spreed WebRTC) only to a selected user-group, open Nextcloud’s user configuration site in your browser: /index.php/settings/users
Create a new group there (e.g. SpreedME). Or you can also use an existing group (like admin).
Now go to Nextcloud’s app configuration page /index.php/settings/apps, find this app and check Enable only for specific groups. Then add all groups which should be able to use this app.
All users not in a group specified in the step above, will neither be able to use this app nor Spreed WebRTC.
TEST NON-NEXTCLOUD USERS (From Nextcloud site, needs testing)
If you want to use Spreed WebRTC with users who do not have a Nextcloud account, you can enable the “Temporary Password” feature on the Nextcloud admin settings page.
This allows them to use Spreed WebRTC with a “Temporary Password”, which admins can generate by clicking on the key icon in the room bar of Spreed WebRTC or at https://FQDN/nextcloud/index.php/apps/spreedme/admin/tp
Admins are either Nextcloud admins or Spreed.ME group admins. Create a group named Spreed.ME and add users as a group admin for that group to allow them to generate “Temporary Passwords”.
TODO:
- Create a systemd unit file to automatically start Spreed WebRTC server on startup, for now it’s manually starting in the foreground
- 4G/External access with a remote STUN/TURN server support (coturn)
Cheers