I used this HowTo to join a Fedora Client to Nethserver 7 AD:
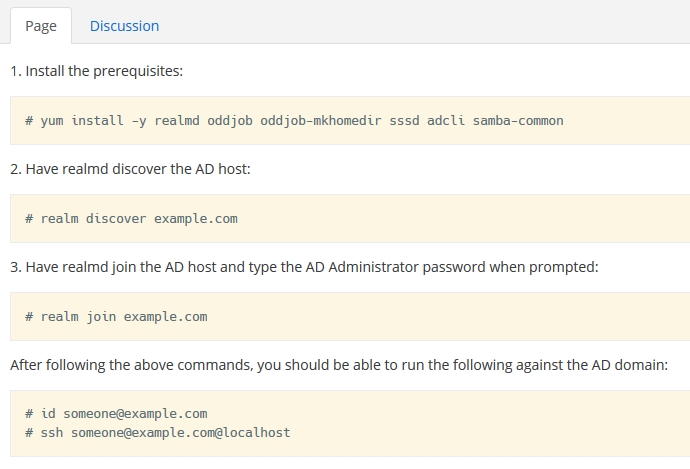
The Problem is only the AD-user Administrator is able to login… Any suggestions to solve this ?
I used this HowTo to join a Fedora Client to Nethserver 7 AD:

The Problem is only the AD-user Administrator is able to login… Any suggestions to solve this ?
The -U flag is required:
realm join -U admin ...
Provided you set a password for the admin’s account
Hi, I used this to join the domain on a fresh installed Fedora 27 Client:
[support@fed001 ~]$ realm discover example.com
example.com
type: kerberos
realm-name: EXAMPLE.com
domain-name: example.com
configured: no
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
[support@fed001 ~]$ sudo realm join -U admin example.com
[sudo] password for support:
Password for admin:
- Installing necessary packages: oddjob oddjob-mkhomedir
Only the user Administrator@example.com is able to logon, I guess the problem is the creation of the homedirectory… The user admin@example.com fails …
support is a local Fedora 27 user…
Hi @fausp,
I tried it and the join works but I can’t see an AD user with ‘id’ or a login screen like yours…will give it another try!
Hi Markus, I use Fedora-Workstation-Live-x86_64-27-1.6.iso on the client side…
Please check the AD join with:
realm list
The join works, “realm list” gives me the joined realm but “id” not working. I’ll try to resetup…
[support@fed001 ~]$ realm list
example.com
type: kerberos
realm-name: EXAMPLE.COM
domain-name: example.com
configured: kerberos-member
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
login-formats: %U@example.com
login-policy: allow-realm-logins
[support@fed001 ~]$ id Administrator@example.com
uid=443200500(administrator@example.com) gid=443200513(domain users@example.com) groups=443200513(domain users@example.com),443200520(group policy creator owners@example.com),443200519(enterprise admins@example.com),443200512(domain admins@example.com),443200518(schema admins@example.com),443200572(denied rodc password replication group@example.com)

[markus@fedora ~]$ realm list
ad.cmb.local
type: kerberos
realm-name: AD.CMB.LOCAL
domain-name: ad.cmb.local
configured: kerberos-member
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common-tools
login-formats: %U@ad.cmb.local
login-policy: allow-realm-logins
[markus@fedora ~]$ id Administrator@ad.cmb.local
id: „Administrator@ad.cmb.local“: Einen solchen Benutzer gibt es nicht
[markus@fedora ~]$The error is “user does not exist”.
Maybe each realm account must be enabled separately. See the realm manpage.
I tried to permit the accounts but it doesn’t work. @fausp has it working, at least as admin.
I try reinstalling Fedora now, maybe there were problems with existing users with same name or I already changed some config files…I should remember to snapshot ![]()
I couldn’t even join with “realm join AD.DOMAIN.LOCAL”, I had to use the samba containers IP (realm join IP).
The join works with Administrator@example.com and admin@example.com but only user Administrator@example.com is able to logon Fedora 27 Client…
Sounds like a DNS Problem, do you use dhcp ?
[root@fed001 sssd]# getent passwd Administrator@EXAMPLE.COM
administrator@example.com:*:443200500:443200513:Administrator:/home/administrator@example.com:/bin/bash
[root@fed001 sssd]# getent passwd admin@EXAMPLE.COM
admin@example.com:*:443201104:443200513:admin:/var/lib/nethserver/home/admin:/usr/libexec/openssh/sftp-server
[root@fed001 sssd]# id Administrator@EXAMPLE.COM
uid=443200500(administrator@example.com) gid=443200513(domain users@example.com) groups=443200513(domain users@example.com),443200520(group policy creator owners@example.com),443200519(enterprise admins@example.com),443200512(domain admins@example.com),443200518(schema admins@example.com),443200572(denied rodc password replication group@example.com)
[root@fed001 sssd]# id admin@EXAMPLE.COM
uid=443201104(admin@example.com) gid=443200513(domain users@example.com) groups=443200513(domain users@example.com),443200572(denied rodc password replication group@example.com),443200512(domain admins@example.com),443201106(g_firma@example.com)
Yes, I did use DHCP but it was strange, “nslookup ad.domain.local” worked, ping the resolved domain IP didn’t work. Reinstalling now, I’ll try with static IP.
god bless virtualization 
I guess that @iglqut can help here, he made some tests with Suse
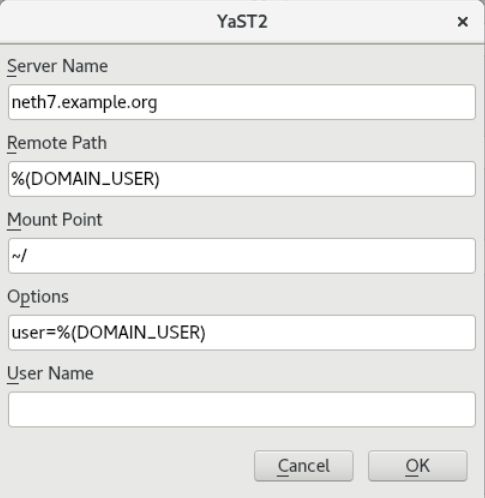
Working great and simple, we are now using even Server based User directories on the users share at NS (find that features at the Windows Domain Join (YAST) screen withe the extras) -
Servername: your Server IP (not the name!)
distant path; %(DOMAIN_USER) => als Variable
Einhängepunkt: ~/ => Linux User Home
Optionen: user=%(DOMAIN_USER)
UserName: leave empty
have fun 
OK Thomas, I would like to try the suse Client, do you have a download link for me ?
I use the big one not the Net one. Enjoy!
Hi Thomas, thank you for the hint. I am a bit busy atm, I will try it in a few days…
regards
Franz
AGN, thank you for your help, Thomas. I just like to give you all a feedback what I have tested…
I tried both, openSUSE Leap and openSUSE Tumbleweed Client and joined them to the NethServer AD.
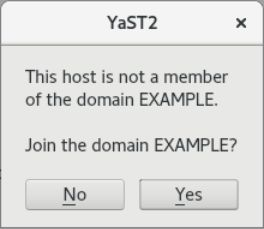
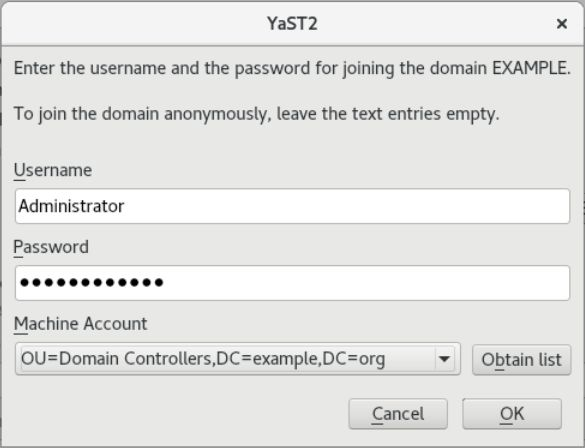
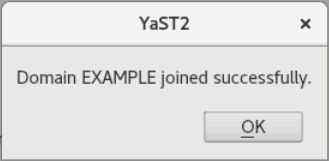
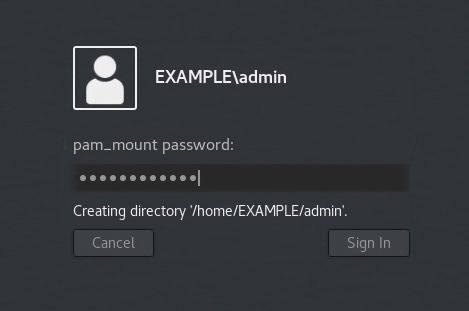
Cool done- thank´s for posting! Any problems yet?