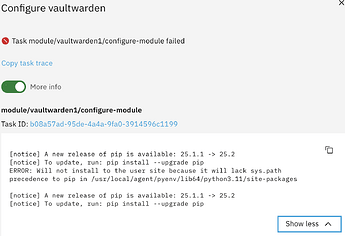
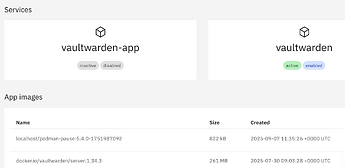
On other app instances I find a way to remove them. Am I missing or not seeing the one for vaultwarden in the status window for Vailtwarden page?
remove module --no-preserve moduleid1 should remove the app you need from CLI
and no he did not mean removing it altogether, he meant just setting new settings on the App settings page, and saving the details to re-apply them.
The One shown on the app settings page is not the actual, since the actual is encoded by Vaultwarden, we cant know for sure and only vaultwarden Knows the value, unless we save it seprately for your convenience, i think its rather better if its not stored by Us, but you the user stores it somewhere safe.
Don’t you think?
@Shadowfire were able to sort it out
I have realized that on the first time installation that the admin token that will be set you can’t update change it
and it seems not be a Nethserver Issue Alone. @kemboielvis22 Could you retest this case using a new Coolify Deployment of Vaultwarden.
Yes, I saved the settings (applied them again). Did not fix it.
As soon as I get back to the office later today I will check it out further.
Thanks for the feedback on this.
Okay i will check and investigate further
Going by these here: GitHub - geniusdynamics/ns8-vaultwarden
A potential Way of Pre-implementing Ldap in VAultwarden
Ldap Configuration for Vaultwarden
Implement a new Service in VAultwaden with
GitHub - ViViDboarder/vaultwarden_ldap: Automate LDAP invites to Vaultwarden which will send an invitation to any member of the group vaultwarden.
Replace dc=example,dc=com with your LLDAP configured domain.
docker-compose.yml to run vaultwarden_ldap
version: '3'
services:
ldap_sync:
image: vividboarder/vaultwarden_ldap:0.6-alpine
volumes:
- ./config.toml:/config.toml:ro
environment:
CONFIG_PATH: /config.toml
RUST_BACKTRACE: 1
restart: always
Configuration to use LDAP in config.toml
vaultwarden_url = "http://your_bitwarden_url:port"
vaultwarden_admin_token = "insert_admin_token_vaultwarden"
ldap_host = "insert_ldap_host"
ldap_port = 3890
ldap_bind_dn = "uid=admin,ou=people,dc=example,dc=com"
ldap_bind_password = "insert_admin_pw_ldap"
ldap_search_base_dn = "dc=example,dc=com"
ldap_search_filter = "(&(objectClass=person)(memberOf=uid=vaultwarden,ou=groups,dc=example,dc=com))"
ldap_sync_interval_seconds = 300
Will check every 300 seconds your ldap group vaultwarden and send an invitation by email to any new member of this group.
We could implement a ExecCondition=/bin/sh -c ‘[ -n “$ldap_host” ]’
based on below to start the service only if Ldap was selected… systemd.service
This could Also potentially be another APP, that Does this, which connects to an existing Vaultwarden Instance.
the longest running PR, that impelments OIDC for Vaultwarden has now been merged: SSO using OpenID Connect by Timshel · Pull Request #3899 · dani-garcia/vaultwarden
On the description it states as a document server, but I believe it’s a password manager?
Thanks,
I guess that is a leftover of copy and paste. Small error.
Please also see the wiki.
Hi, there is a new Version of vaultwarden yet to be merged, We need help testing the new VErsion:
geniusdynamics/ns8-vaultwarden at dev
Fresh Install
add-module ghcr.io/geniusdynamics/vaultwarden:dev 1
Test Cases
- Test Backup
- Test Restore
- Verify Admin Keys on UI
** Update to New Version**
Install Previous Version first
add-module ghcr.io/geniusdynamics/vaultwarden:1.0.0 1
Then Update to New Version
api-cli run update-module --data '{"module_url":"ghcr.io/geniusdynamics/vaultwarden:dev","instances":["vaultwarden"],"force":true}'
Test Cases
- Update Works, and retains Data
- Login to Admin page works
On Separate Note: Vaultwarden Support SSH Authentication KEys
Now Linkwarden is working. What is with Vaultwarden. Is it usable?
yes
vaultwarden is a password manager
selfhosted alternative of bitwarden
the current version 1 on SS as well as on the dev branch geniusdynamics/ns8-vaultwarden at dev
add-module ghcr.io/geniusdynamics/vaultwarden:dev 1
works, dev is latestt, we have not yet tested upgrading from old to this, if you can help test upgrade, we can release
File “/usr/local/sbin/add-module”, line 34, in
result = agent.tasks.run(
^^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/run.py”, line 39, in run
results = runp([taskrq], **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/run.py”, line 50, in runp
return asyncio.run(_runp(tasks, **kwargs))
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/lib64/python3.11/asyncio/runners.py”, line 190, in run
return runner.run(main)
^^^^^^^^^^^^^^^^
File “/usr/lib64/python3.11/asyncio/runners.py”, line 118, in run
return self._loop.run_until_complete(task)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/lib64/python3.11/asyncio/base_events.py”, line 654, in run_until_complete
return future.result()
^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/run.py”, line 120, in _runp
return await asyncio.gather(*runners, return_exceptions=(len(tasks) > 1))
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/run.py”, line 127, in _run_with_protocol
return await run_redisclient(taskrq, **pconn)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/redisclient.py”, line 77, in run_redisclient
await _task_submission_check_client_idle(rdb, taskrq, kwargs[‘check_idle_time’])
File “/usr/local/agent/pypkg/agent/tasks/redisclient.py”, line 36, in _task_submission_check_client_idle
for client_item in await rdb.client_list(‘normal’):
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/client.py”, line 601, in execute_command
conn = self.connection or await pool.get_connection(command_name, **options)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 1040, in get_connection
await self.ensure_connection(connection)
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 1062, in ensure_connection
await connection.connect()
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 258, in connect
await self.on_connect()
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 326, in on_connect
auth_response = await self.read_response()
^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 510, in read_response
response = await self._parser.read_response(
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/_parsers/hiredis.py”, line 210, in read_response
raise response
redis.exceptions.AuthenticationError: invalid username-password pair or user is disabled.
[root@ ~]# add-module Package vaultwarden · GitHub 1
File “/usr/local/sbin/add-module”, line 34, in
result = agent.tasks.run(
^^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/run.py”, line 39, in run
results = runp([taskrq], **kwargs)
^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/run.py”, line 50, in runp
return asyncio.run(_runp(tasks, **kwargs))
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/lib64/python3.11/asyncio/runners.py”, line 190, in run
return runner.run(main)
^^^^^^^^^^^^^^^^
File “/usr/lib64/python3.11/asyncio/runners.py”, line 118, in run
return self._loop.run_until_complete(task)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/lib64/python3.11/asyncio/base_events.py”, line 654, in run_until_complete
return future.result()
^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/run.py”, line 120, in _runp
return await asyncio.gather(*runners, return_exceptions=(len(tasks) > 1))
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/run.py”, line 127, in _run_with_protocol
return await run_redisclient(taskrq, **pconn)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pypkg/agent/tasks/redisclient.py”, line 77, in run_redisclient
await _task_submission_check_client_idle(rdb, taskrq, kwargs[‘check_idle_time’])
File “/usr/local/agent/pypkg/agent/tasks/redisclient.py”, line 36, in _task_submission_check_client_idle
for client_item in await rdb.client_list(‘normal’):
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/client.py”, line 601, in execute_command
conn = self.connection or await pool.get_connection(command_name, **options)
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 1040, in get_connection
await self.ensure_connection(connection)
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 1062, in ensure_connection
await connection.connect()
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 258, in connect
await self.on_connect()
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 326, in on_connect
auth_response = await self.read_response()
^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/asyncio/connection.py”, line 510, in read_response
response = await self._parser.read_response(
^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^^
File “/usr/local/agent/pyenv/lib64/python3.11/site-packages/redis/_parsers/hiredis.py”, line 210, in read_response
raise response
redis.exceptions.AuthenticationError: invalid username-password pair or user is disabled.
what test is this
This one from above…
add-module Package vaultwarden · GitHub 1
vaultwarden ondev branch is not woeking?!! fresh install?