I was wondering on the possibility of blocking mass ip addresses without iptables. I can manually tell ip tables to block ips but an option to add a list of ips to the firewall would be awesome. It would look like an option under hosts to add a block of ips that are labeled something. So under hosts, be able to paste 1-1000 or more ip addresses that can be selected in the firewall for “DROP” or something.
There are several objects that you can use on Firewall objects.
Subnets, ip Blocks, hosts, hosts group.
Would you like to analyze this feature regarding the user interface?
Shorewall already supports blacklists, but we need a clear and simple user interface.
Have you read this thread?
The issue here is I would have to add each host manually, before adding them as a “host group”.
I saw that, I was just wondering on the possibility of an option in “firewall objects”. Expand “Hosts” to allow for host lists
You could always use ipset which is quite effective and if you have a couple of thousand IP addresses in the list, I would recommend ipset for performance reasons.
Do you have the list of IP addresses in a text file? Or do you dynamically pick them out of the firewall logs based on certain criteria?
What do you think about adding a new tab in the firewall objects page to add ipsets?
We could add a cron job to automatically download lists and add to the relevant ipset.
I think that is a great idea. The fail2ban list would be the first block list for me, but I know of other lists that would be cool to add. Ipsets would be awesome.
@filippo_carletti That would be an interesting feature - a tab for ipsets.
I would love to have a reliable place to run the script I have on startup which creates and populates the IPsets I have.
I find that Shorewall fails to start if the IPsets have not been created.
@Jclendineng I’ll ping you the set up that I have for this later
GeoIP Location could be useful too, into firewall objects.
True. See this code to create ipsets:
@Jclendineng Apologies for taking so long to ping you the following details, been rather busy lately with school holidays and work.
I have a file call /etc/shorewall/ipsets which contains the following:
create blockipsnets hash:net family inet hashsize 16384 maxelem 65536
create blockips hash:net family inet hashsize 262144 maxelem 524288
create whitelistips hash:ip family inet hashsize 1024 maxelem 65536
Once you have created that file with those entries, run the following command to create the IPSets:
ipset restore -! < /etc/shorewall/ipsets
In Shorewall, I enabled blacklists so the line effectively now reads:
$OUT.=“net\t”.$i->key.“\tdhcp,nosmurfs,optional,blacklist”;
In the /etc/shorewall/blrules file, I added the following rules:
WHITELIST net:+whitelistips fw
DROP net:+blockipsnets fw
DROP net:+blockips fw
WHITELIST net:+whitelistips loc
DROP net:+blockipsnets loc
DROP net:+blockips loc
Note that the names in the blrules need to match up with the names of the IPSets you created earlier.
If you want to drop traffic from an entire country, you can add a line like the following:
DROP net:[1] loc
I have the following details in the rc.local script so ensure that the IPSets are created and loaded with the relevant information before Shorewall starts. Shorewall will fail to start if the IPSets are not created:
if [ “
lsmod | grep ip_set” = “” ]; then
modprobe ip_set
fiCounter=
cat /etc/shorewall/ipsets | wc -l
if [ $Counter -eq 0 ]
then
if [-f /etc/shorewall/ipsets.bak ]
then
Counter=cat /etc/shorewall/ipsets.bak | wc -l
if [ $Counter -gt 0 ]
then
cp /etc/shorewall/ipsets.bak /etc/shorewall/ipsets
fi
fi
fiipset restore -! < /etc/shorewall/ipsets
I have 2 additional text files, 1 for a list of public IP addresses which I whitelist as they are trusted IP addresses which I use, the other is a specific list of IP Addresses which I wish to blacklist which may not appear in any of the logs.
I have a cron script which runs through the logs, grabs the relevant information and then updates the IPSets. the script looks pretty much like the following:
strHome=“/root/blacklist”
strTmpBL=“$strHome/blacklist”
strTmp1=“$strHome/blacklisttmp1”
rm-rf $strTmpBL
touch $strTmpBL
- Grab a copy of all of the IPs which you wish to blacklist from the logs or any other location which you desire and write them to the
strTmpBLfile.
- check amount of lines before sorting and cleanup and basic ip syntax checking
cat $strTmpBL | grep -E -o “([0-9]{1,3}[.]){3}[0-9]{1,3}” | sort | uniq > $strTmp1
rm -rf $strTmpBL
mv $strTmp1 $strTmpBL
if [ -f $strHome/safe_ips.txt ]
then
cat $strHome/safe_ips.txt | sort | uniq > $strSafeTmp
rm -rf $strHome/safe_ips.txt
mv $strSafeTmp /root/blacklist/safe_ips.txt
grep -v -f $strHome/safe_ips.txt $strTmpBL > $strTmp1
rm -rf $strTmpBL
mv $strTmp1 $strTmpBL
fi
while read line; do
ipset -A -exist blockips $line &
done < $strTmpBL
- This is where I save the IPsets to a file. I also make a backup copy of it as I found that sometimes when Shorewall is stopped or restarted or when the server is restarted, the entries in the
/etc/shorewall/ipsetsfile are thrown away and I am left with an empty file which causes Shorewall not to start.
ipset -S > /etc/shorewall/ipsets
Counter=
cat /etc/shorewall/ipsets | wc -l
if [ $Counter -gt 0 ]
then
cp /etc/shorewall/ipsets /root/blacklist/ipsets.bak
fi
Sorry about the lack of indentation, the indentation was lost when posting the snippets in here and I don’t know how to fix that.
Hope this is of some use.
CN ↩︎
Admins any chance of an integration in the future?
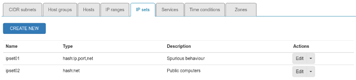
Regarding server-manager UI I think it makes sense to start with ipsets, then blacklists/whitelist and geoIP.
I don’t know if this feature will make it but knowing what we are after would help. I want to get some feedback on how this could be implemented, which options you consider better to expose on UI, and how to make them “easy to use”. Share your thoughts and correct me where I’m wrong.
Shorewall requires xtables to support geoIP. Kernel updates could suppose a problem for xtables? An alternative are geoIP ipsets.
-
ipsets should:
- use IPv4 only (IPv6 is not enabled/supported on NethServer for Shorewall)
- allow adding other firewall objects (hosts, IP ranges, cidr, services) as set members?
- have an inverse match (nomatch) checkbox for set members?
- have a text field to add ip addresses in bulk, or a file upload option?
- have an option to “subscribe” to external ipsets lists (URL, update interval for cron…)?
- which set types to use? a hard-coded one, or do you need multiple choices? (see poll below for choices)
- For IP Sets, which set types should be supported from UI?
- bitmap:ip
- bitmap:ip,mac
- bitmap:port
- hash:ip
- hash:net
- hash:ip,port
- hash:net,port
- hash:ip,port,ip
- hash:ip,port,net
- hash:net,iface
- list:set
0 voters
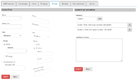
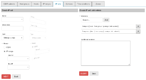
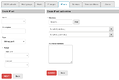
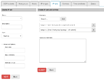
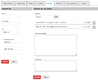
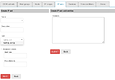
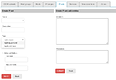
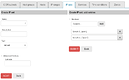
A possible mock-up of multiple ipset types creation in a two steps process:
Image mock-up of hash:net,iface is not included, but probably should be guided (eg. net:=ip | ip-range | ip/cidr; iface:= dropdown with available interfaces; nomatch checkbox; add/save button to build a list of entries).
Most publicly shared blacklists/blocklists are made of IPs and CIDR nets, therefore fitting on hash:ip / hash:net ipset types. They could go on a different tab or in a tab on the firewall rules section, to be used against blrules file. 
Just throwing ideas… Please, correct me were I’m wrong.