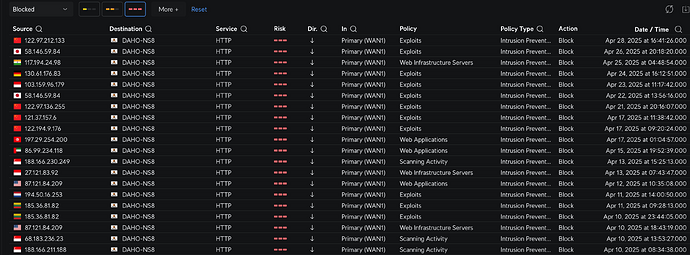
I run my NS8 server at home behind a UniFi gateway. This has documented a series of intrusion attempts.
PS Alert 1: Attempted Administrator Privilege Gain. Signature ET SCAN Mirai Variant User-Agent (Inbound). From: 122.97.212.133:5158, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: Web Application Attack. Signature ET SCAN JAWS Webserver Unauthenticated Shell Command Execution. From: 58.146.59.84:47946, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: Attempted Administrator Privilege Gain. Signature ET EXPLOIT D-Link Devices Home Network Administration Protocol Command Execution. From: 117.194.24.98:53519, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: Potentially Bad Traffic. Signature ET WEB_SERVER WebShell Generic - wget http - POST. From: 130.61.176.83:39018, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: A Network Trojan was detected. Signature ET SCAN Internal Dummy Connection User-Agent Inbound. From: 188.166.230.249:54081, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: Attempted Administrator Privilege Gain. Signature ET EXPLOIT D-Link Devices Home Network Administration Protocol Command Execution. From: 27.121.83.92:33282, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: A Network Trojan was detected. Signature ET WEB_SERVER PHP.//Input in HTTP POST. From: 87.121.84.209:56738, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: Web Application Attack. Signature ET WEB_SPECIFIC_APPS MVPower CCTV DVR /shell JAWS Webserver Unauthenticated Remote Command Execution (CVE-2016-20016). From: 185.36.81.82:46674, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: Web Application Attack. Signature ET WEB_SPECIFIC_APPS MVPower CCTV DVR /shell JAWS Webserver Unauthenticated Remote Command Execution (CVE-2016-20016). From: 185.36.81.82:43728, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: Web Application Attack. Signature ET WEB_SERVER /bin/bash In URI, Possible Shell Command Execution Attempt Within Web Exploit. From: 87.121.84.209:51260, to: 192.168.3.21:80, protocol: TCP
IPS Alert 1: A Network Trojan was detected. Signature ET SCAN Internal Dummy Connection User-Agent Inbound. From: 68.183.236.23:50797, to: 192.168.3.21:80, protocol: TCP
Now I have a number of other NS8 servers directly connected to the internet, i.e. without intrusion prevention.
Is a pure NS8-Server actually protected against such attempts?