I’m curious, does it play with the NS mail-server or (as zarafa) does it deploy it own imap server?
Below are the steps to install Citadel on Nethserver7b2
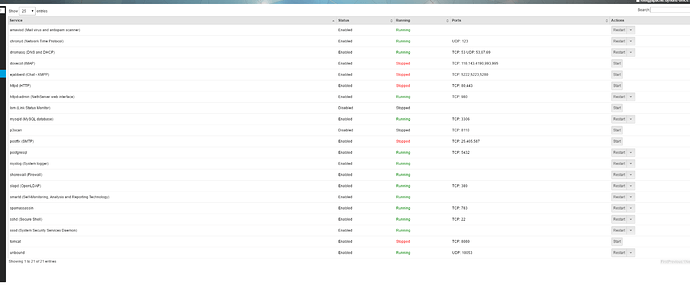
First this is the list of services that should be disabled prior to the installation:
SSH to the server and execute the following:
netstat -nlp
There should be no services running on the following ports:
SMTP, Secure SMTP, POP secure POP , port 2000, port 5280 , 443
should there be then check the PID number of that service and kill it
kill pidnumber
The best way to install Citadel is by executing the easyinstall.
yum -y groupinstall "Development Tools"
yum -y install gettext shared-mime-info openssl-devel
wget -q -O - http://easyinstall.citadel.org/install | sh
Accept all default parameters (define admin as user name and give it a password)
When asked under which username to run Citadel, keep the user root
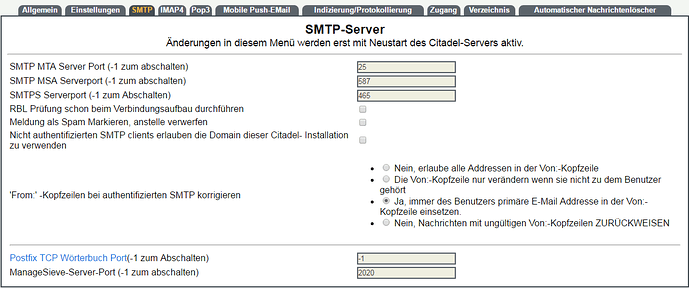
Leave the remaining as default, please do not change the default port 2000 and 443 under which Citadel wishes to run else you will never be able to access it.
Problems and issues:
- Was not able to configure it as LDAP (did not put much efforts anyway)
- Cannot change default ports although the WEBCIT config file is located under /etc/rc.d/init.d
no matter what ports we define the webcit will refuse to honor connections until defaults are put back
ports 2000 and 443 . Also it will only accept connections to the secure 443 port. - By keeping the port 443 for citadel, we deprive nextcloud from being accessed and that is a major drawback
Can someone join efforts with me ?
@ghost, every kind of app that need disabling of standard daemons on NS is to avoid…
Stefano, sure no issues. I thought there was interest in knowing the steps, drawbacks and side effects of installing Citadel on NS.
Surely there is a solution to make all applications/services coexist. I am here not to eliminate any applications.
If my help is appreciated then I continue else I will work in silence without sharing my experiments.
When changing tge port for webcit, did you retart the webcit service?
Also check this from citadel support
Yes sure restarted and even rebooted the linux machine.
The Citadel support talks about Apache which is not installed on my NS7
I will try the redirect referred to on that article it might help.
don’t get me wrong… you’re free to do all you want…
just be aware that if citadel (or any other app you like) can’t work with NS’ daemons (http, smtp, pop, ldap, imap and so on) it likely won’t be adopted… same for Zarafa, Zimbra etc…
even if NS is linux, it’s not a plain centos install (you can safely install citadel on centos with no issues), and it relies on a strict integration among many services…
it’s the same if you think about SME server, Zentyal, Clearos… all of them are more than just linux.
I repeat: if you manage to make citadel work with standard services, you’re more than welcome…
Hi @ghost I’m also playing with citadel. So maybe you 're interested in my experiences.
Me too. Neither with Open-LDAP nor with NSDC.
Tried it several times, but installation programm stucks at 95 to 97 %.
I didn’t find any log-entries related to the installation. In the txt-file in tmp-directory
I didn’t find any relevant info. Did you find something?
My installation accepts port 2443 for https and 2000 for http.
@mark_nl
I can send mails from one citadeluser to another, without installing any ns-package.
Citadel comes with it’s own servers.
But I won’t go deeper into citadel. I couldn’t figure out how it works with ldap and so it is not of interest for me on NS7. The concept with this rooms to share to other user is also a bit peculiar.
I’m using SOGo and will keep it until webtop 5 will be available.
I like the interface of wbtop and when the devs of webtop keep their promisses with caldav/groupdav I think I will change to it.
Thanks to @ghost for the hint about citadel. It’s always good to know some alternatives. I think citadel is a good and powerfull groupware, but I can’t get familiar with it’s concept and it’s GUI.
So long guys.
@flatspin thank you for sharing this.
I was experiencing exactly the same behavior while installing it with LDAP.
As for the ports, that was not my very first priority to be honest as I know that we can figure a solution out.
I share my concern with you, if no LDAP support then it has no place on my network.
An alternative approach could be running citadel internal LDAP and configure NethServer to use it. If it has RFC2307 schema and anonymous binds, NethServer can consume its accounts.
During installation it’s possible to choose
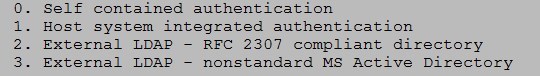
From citadel site about self contained authentication:
This is also known in some other circles as “black box” authentication. Note that you can use mod_auth_citadel to integrate other applications with citadel; You don't need ldap for that.
Self-contained authentication is the mode most sites will want to use. It is by far the easiest because it requires zero maintenance and zero external configuration.
If I understand that right, citadel doesn’t use ldap in this case.
What about “host system integrated authentication”?
If citadel runs on NethServer, both PAM and nsswitch are already configured!
My main aim is the Nextcloud + extra features around it like:
A good CRM with integration with Asterisk
A fair HRM
Something like Zentyal, Zimbra or Citadel,
Chatting XMPP + Video to complete the package.
To cut the story short , most of the above support LDAP, or Active directory (AD is low priority for me as I do not wish to mix my AD of Microsoft with the nextcloud) my nextcloud will also be partially open to external users , LDAP is the best choice I could think of unless someone can enlighten me otherwise.
But users are created with nethgui with nsdc installed are not available on the host, only in the container, or am I wrong? These users are not listed in /etc/passwd.
That file is read by the pam_unix backend. However nethserver-sssd configures pam_sss module, too so the whole system can authenticate against AD or OpenLDAP, too.
A similar configuration applies to /etc/nsswitch.conf.
Hi everyone,
I can only say that there is a lot of confusion around Webtop here.
First, it is actively developed even today, but as already stated elsewhere, we stopped pushing sources in 2011 because we had to focus on our customers and had not time to work with a community.
I personally don’t see the point to compare Webtop with Citadel, because they are two completely different product, where Webtop is focused on being both a development platform of services and an Exchange/Zimbra/Notes/whatever-business-collaboration-product replacement.
Second, Webtop is a multidomain solution: we have our cloud based customers running around 1000 users inside a multitenant zone, with different domains, different customized instances where needed and login rebranding depending on domain.
Third, we’ve been actively working on Webtop5 in the last couple of years, and going to release a public beta together with Nethesis shortly (while still mantaining and adding features to wt4 where and when needed).
The fact that latest git sources repos for both wt4 and wt5 are not public yet, is just a matter of agreements to be finalized between Sonicle and Nethesis.
I hope you can wait a little bit longer, and resist the urge to push, it’s a very very very busy moment for all of us, focused on publishing the bast we can as a starting point with the community.
Thanks,
Gabriele
Tried it. Accountprovider OpenLDAP.
Citadel is starting, but I can’t authenticate.
System does not use native mode authentication.
from messages.log
All logs with sssd are empty.
from slapd.log
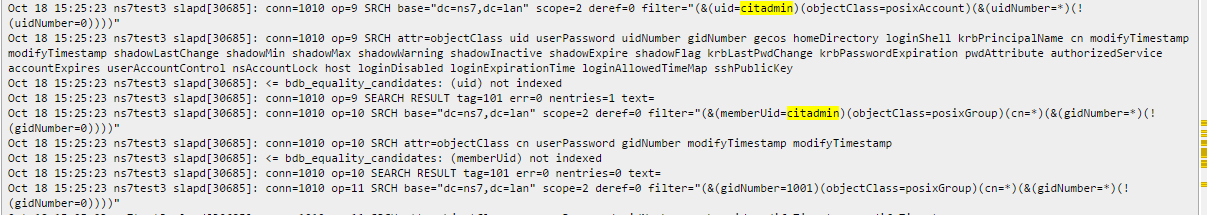
Anything relevant?
Is citadmin present in the LDAP tree? Can you set the search base in citadel config file?
Can you attach the output of
ldapsearch -Y EXTERNAL[root@ns7test3 /]# ldapsearch -Y EXTERNAL
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
# extended LDIF
#
# LDAPv3
# base <dc=directory,dc=nh> (default) with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# directory.nh
dn: dc=directory,dc=nh
objectClass: top
objectClass: dcObject
objectClass: organization
dc: directory
o: Example Org
# People, directory.nh
dn: ou=People,dc=directory,dc=nh
objectClass: top
objectClass: organizationalUnit
ou: People
# Groups, directory.nh
dn: ou=Groups,dc=directory,dc=nh
objectClass: top
objectClass: organizationalUnit
ou: Groups
# locals, Groups, directory.nh
dn: cn=locals,ou=Groups,dc=directory,dc=nh
objectClass: posixGroup
cn: locals
gidNumber: 1003
# libuser, directory.nh
dn: cn=libuser,dc=directory,dc=nh
objectClass: device
objectClass: simpleSecurityObject
cn: libuser
description: libuser management account
userPassword:: e0NSWVBUfSQ2JGZlWWNPMHVYR09EZFhwdG4kNGtGa0hFaVBqVS9ocEtXbW5UeEJ
Mby9SdkVpS0FZbTZtbnRrVEFsR2dIL2t2djJXTjBNNnZ2T1BCQkFRNTQyWm41bmVJRUw5alRxbG80
M1U2N1pNcS4=
# pam, directory.nh
dn: cn=pam,dc=directory,dc=nh
objectClass: device
objectClass: simpleSecurityObject
cn: pam
description: pam management account
userPassword:: e0NSWVBUfSQ2JHlrL3cxVVl1VWRRdEVhWXckNDJBbVA4NnFuNW43ajMzVzNqbjQ
4c0hOTE5LNjE2U0pIaGpBakJCc05OeGxtSy9IcFJJQlBEdU5hQmxrN3ZtTHhqTld5dmNRRVAuZ2lo
LlJjejZuYTA=
# admin, People, directory.nh
dn: uid=admin,ou=People,dc=directory,dc=nh
uidNumber: 1000
gidNumber: 1001
uid: admin
shadowMax: 99999
shadowWarning: 7
shadowMin: 0
loginShell: /usr/libexec/openssh/sftp-server
homeDirectory: /var/lib/nethserver/home/admin
shadowInactive: -1
shadowExpire: -1
gecos: Administrator
shadowLastChange: 17091
shadowFlag: -1
cn: Administrator
sn: admin
objectClass: posixAccount
objectClass: shadowAccount
objectClass: inetOrgPerson
mail: admin@ns7.lan
userPassword:: e0NSWVBUfSQ2JHRLekxVUWcuYkxlVnNBc1kkckQwdWx6ZlMzd1lxVDl0Skw4L0l
MZU1HOFdPSDQyd3dRR3kycDVNVHpjcmRYUEFZNm5PR1NhS2J3bU1jdURwVS5PUW9FT095RG1xNmtT
eXg2VmxOai4=
# citadmin, People, directory.nh
dn: uid=citadmin,ou=People,dc=directory,dc=nh
uidNumber: 1002
gidNumber: 1001
uid: citadmin
shadowMax: 99999
shadowWarning: 7
shadowMin: 0
loginShell: /usr/libexec/openssh/sftp-server
homeDirectory: /var/lib/nethserver/home/citadmin
shadowInactive: -1
shadowExpire: -1
gecos: Citadel
shadowLastChange: 17091
shadowFlag: -1
cn: Citadel
sn: citadmin
objectClass: posixAccount
objectClass: shadowAccount
objectClass: inetOrgPerson
mail: citadmin@ns7.lan
userPassword:: e0NSWVBUfSQ2JC40eUtURzJCamdMRjE2dzUkUk1oUzZlZ2gwWVloWks4eFN5a0V
zbTlwd1pYR0VaR0x1QTFTM2lWbno0eGdjZWxaenpNcXJKcnRLZVNvNlJoYzBXYktqazdUamlWbE8v
Zkk1LmpWMzE=
# testuser, People, directory.nh
dn: uid=testuser,ou=People,dc=directory,dc=nh
uidNumber: 1003
gidNumber: 1003
uid: testuser
shadowMax: 99999
shadowWarning: 7
shadowMin: 0
loginShell: /usr/libexec/openssh/sftp-server
homeDirectory: /var/lib/nethserver/home/testuser
shadowInactive: -1
shadowExpire: -1
gecos: Testuser
shadowLastChange: 17092
shadowFlag: -1
cn: Testuser
sn: testuser
objectClass: posixAccount
objectClass: shadowAccount
objectClass: inetOrgPerson
mail: testuser@ns7.lan
userPassword:: e0NSWVBUfSQ2JHhHNlFTRkVzLnkvaFBuQXEkc2FJT28uY2s2cmhFQm5qdHhDN0N
MbGk1THE2TldzVnZsbUVmTGZLbDd0emgzeGdscnhha3pZSEtaalJObWdScnFEWERyTi95YkZFU29v
SUI0UXQvajA=
# search result
search: 2
result: 0 Success
# numResponses: 10
# numEntries: 9
[root@ns7test3 /]#
citadmin is present.
It makes sense , I just noticed that while installing the Citadel in LDAP mode it asks for the ldap admin password.
I entered what I thought it was but I was wrong.
It would be good since we have an LDAP expert here to advise how can we retrieve the default NS7 LDAP Password.
I do have an LDAP issue with Nextcloud + XMPP that I also seek help on.