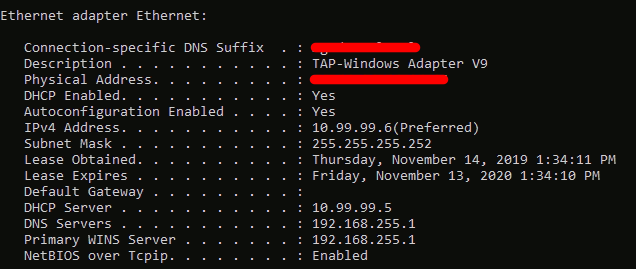
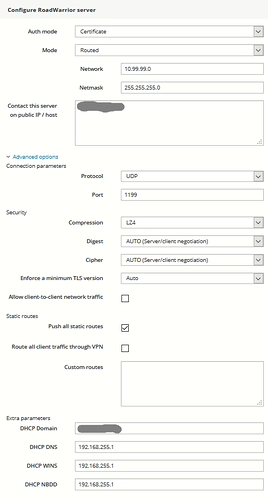
It’s a bit messy for my comprehension. I hope that will be readable for you, @tl5k5.
Site LAB
Subnet: 192.168.255.0/24
Gateway: 192.168.255.1
DNS: 192.168.255.2
Site Island
Subnet: 10.210.13.0/24
NethServer
Red Interface: 192.168.255.13/24, GW 192.168.255.1
Green Interface: 10.210.13.13
OpenVPN/Purple: 10.99.99.0/24
Don’t forget that due to this setup, all Island subnet will have full access to Lab LAN, no matter what.
For create some rules to filter traffic and access from Island to LAB, an interface must be add into Gateway 192.168.255.1 for connecting Island subnet, and the gateway must have firewall capabilities for create any kind of regulation.
If the device is currently uncapable of any of this two requiremens, LAB’s Gateway must be replaced or add another device (maybe another NethServer?) between LAB LAN and the current gateway
If Island access to LAN is not an issue, IMVHO there are two ways to achieve something similar on what you’re looking for.
Option 1: whole subnet accessible both ways and static route.
NethServer should be configured as
Green Interface: 192.168.255.13/24, GW 192.168.255.1
Blue Interface: 10.210.13.13/24
On LAB Subnet a static route must be applied to all device that must reach or being reachable from Island, using 192.168.255.13 as a gateway to reach 10.210.13.0/24.
Firewall rules must be added to grant access From island to LAB, because as stated into docs
https://docs.nethserver.org/en/v7/firewall.html
https://docs.nethserver.org/en/v7/firewall2.html#firewall-new-section
(please read both links carefully)
Option2: OpenVPN client configured on all devices who must access Island subnet.
Don’t forget that due to this setup, all Island subnet will have full access to Lab LAN, no matter what.
RoadWarrior server should
- push all static routes
- not allow client-to-client traffic
- Route all client traffic through VPN must be disabled
Create a RoadWarrior user for every installation should access, reserve IP address for every user. An administrative user (Linux or windows do not matter) should be able to start the client and open the tunnel automatically.
Therefore, firewall rules for allow access to Island’s green network segment should be created, if necessary.
Both solutions are a bandaid, not a “real” (IMHO) solution. Which is using a gateway into LAB capable of having another “Green” interface for Island subnet.
This will ease deployment of
OpenVPN (not always possible for “not computers” like printers and NAS or something similar)
or static route (sometimes can lock you out from the device if not well written, some devices do not support static routes).
Maybe a LAB gateway with enough interfaces (why not, realized on NethServer) can be the “real” solution, with a “normal” router on Island site capable of being DHCP server and traffic regulator.
Mine are just options. Bandaids one and “real” one. There are plenty way to create solutions for desires.