I’ll test it later today, maybe you need a route on your windows client to your VPN remote network…
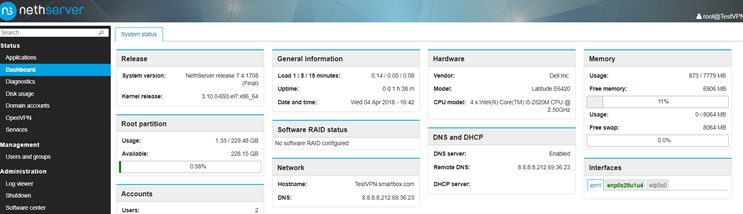
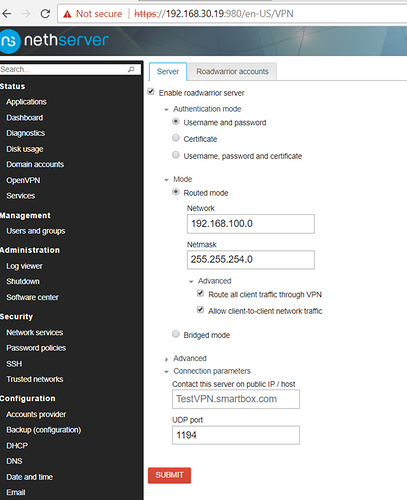
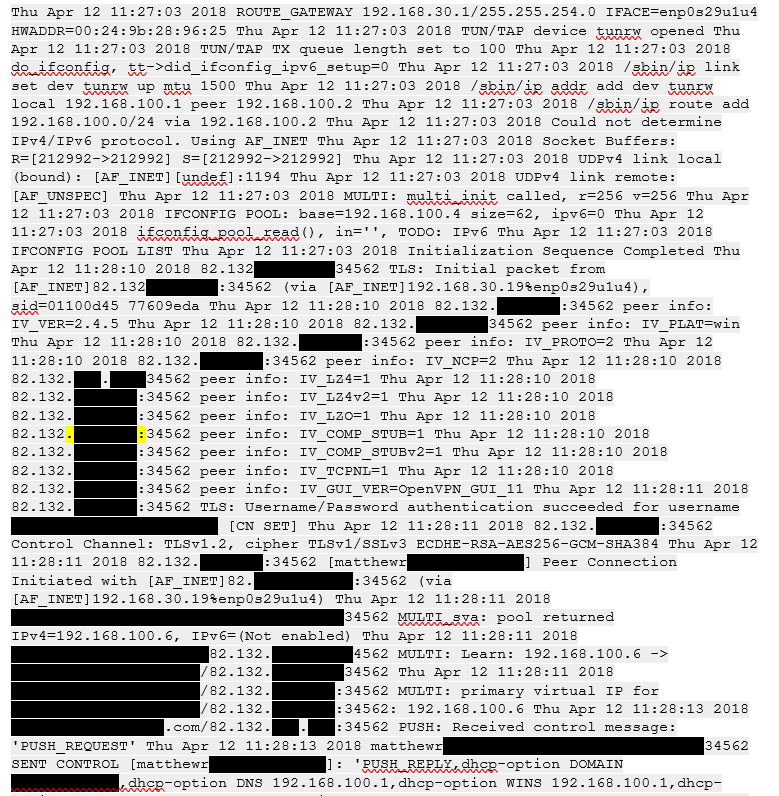
I re installed fresh Nethserver 7 downloaded new config file connected in again client icon goes green i successfully receive ip of 192.168.100.6 but couldn’t connect to any website or anything on the network, see screen shots
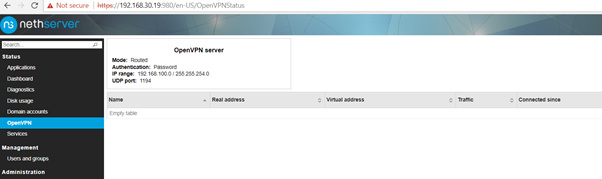
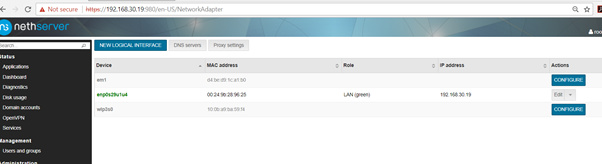
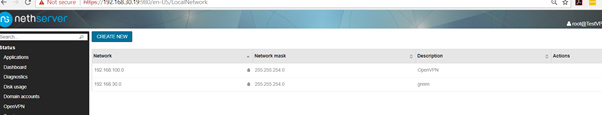
I tested it on Windows 10, installed openvpn client straightforward with default settings. Then I just imported the downloaded settings. I connected to the network without problems and could reach other network devices or webservers. I tested via mobile phone hotspot.
The differences between our setups are:
- Your VPN subnet mask. I have 255.255.255.0 and you have 255.255.254.0. I recognized that the adapter under Windows used 255.255.255.252 in my test.
- I don’t have the “Route all client traffic through VPN” option enabled.
Thanks Markus I’m out the office but will try another test later tonight
with these settings tweaked slightly and update.
ok so i tested this again just now and still stumped i replicated the set up the same as yours again i download config, connect into server of obtain an ip of 192.168.100.6
but can’t access anything on 192.168.30.x subnet i can even see my session on the server, i’m missing something obvious here surely?
Does firewall allow traffic between 192.168.30.X and 192.168.100.X?
I’m using a Dell sonicwall tz300 as main router would I be looking there or
you mean firewall in nethserver?
ok i’m thinking the issue is deffo routing between 192.168.100.0 to my lan 192.168.30.x
i can ping my NS Vpn server 192.168.30.19 from client and get reply but nothing else on the lan
is there a route i need to add in shorewall to route between 192.168.100.0 to 192.168.30.0
iptable is as follows:
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.30.1 0.0.0.0 UG 0 0 0 enp0s29u1u4
169.254.0.0 0.0.0.0 255.255.0.0 U 1002 0 0 enp0s29u1u4
192.168.30.0 0.0.0.0 255.255.254.0 U 0 0 0 enp0s29u1u4
192.168.100.0 192.168.100.2 255.255.254.0 UG 0 0 0 tunrw
192.168.100.2 0.0.0.0 255.255.255.255 UH 0 0 0 tunrw
firewall.log
Apr 11 15:59:00 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:28:96:23:08:00 SRC=192.168.30.195 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=10081 DF PROTO=TCP SPT=50654 DPT=62078 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 11 15:59:01 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:28:96:23:08:00 SRC=192.168.30.195 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=10082 DF PROTO=TCP SPT=50654 DPT=62078 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 11 16:16:48 TestVPN kernel: Shorewall:sfilter:DROP:IN=tunrw OUT=tunrw MAC= SRC=192.168.100.6 DST=192.168.100.2 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=5507 PROTO=ICMP TYPE=8 CODE=0 ID=1 SEQ=10
Apr 11 16:16:52 TestVPN kernel: Shorewall:sfilter:DROP:IN=tunrw OUT=tunrw MAC= SRC=192.168.100.6 DST=192.168.100.2 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=5508 PROTO=ICMP TYPE=8 CODE=0 ID=1 SEQ=11
Apr 11 16:16:57 TestVPN kernel: Shorewall:sfilter:DROP:IN=tunrw OUT=tunrw MAC= SRC=192.168.100.6 DST=192.168.100.2 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=5513 PROTO=ICMP TYPE=8 CODE=0 ID=1 SEQ=12
Apr 11 16:17:02 TestVPN kernel: Shorewall:sfilter:DROP:IN=tunrw OUT=tunrw MAC= SRC=192.168.100.6 DST=192.168.100.2 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=5515 PROTO=ICMP TYPE=8 CODE=0 ID=1 SEQ=13
Apr 11 16:36:17 TestVPN kernel: Shorewall:sfilter:DROP:IN=tunrw OUT=tunrw MAC= SRC=192.168.100.6 DST=192.168.100.2 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=5849 PROTO=ICMP TYPE=8 CODE=0 ID=1 SEQ=52
Seems like you didn’t change the subnetmask of the VPN network. You may try 255.255.255.0 instead of 255.255.254.0.
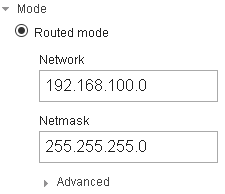
EDIT: I tried different subnet masks and it just works
sorry yep changed to 255.255.255.0 still no joy, can ping vpn server but nothing else on lan
Routing table seems to be ok.
Are there any errors in /var/log/openvpn/openvpn.log?
ok no errors in openvpn.log will post just need to redact
I don’t have that entries in firewall.log. Did you customize the firewall?
i didn’t touch firewall after fresh install
ok and firewall log now showing this do i need to add a arule?
TTL=128 ID=1298 DF PROTO=TCP SPT=10557 DPT=22 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:03 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=1299 DF PROTO=TCP SPT=10555 DPT=5060 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:03 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=1341 DF PROTO=TCP SPT=10547 DPT=5800 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:03 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=1342 DF PROTO=TCP SPT=10548 DPT=16992 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:03 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=1343 DF PROTO=TCP SPT=10551 DPT=9100 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:03 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=1344 DF PROTO=TCP SPT=10550 DPT=17988 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:03 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=1345 DF PROTO=TCP SPT=10554 DPT=3389 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:03 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=1347 DF PROTO=TCP SPT=10557 DPT=22 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:03 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=52 TOS=0x00 PREC=0x00 TTL=128 ID=1348 DF PROTO=TCP SPT=10555 DPT=5060 WINDOW=64240 RES=0x00 SYN URGP=0
Apr 12 12:02:06 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=69 TOS=0x00 PREC=0x00 TTL=128 ID=1550 PROTO=UDP SPT=62700 DPT=161 LEN=49
Apr 12 12:02:11 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=69 TOS=0x00 PREC=0x00 TTL=128 ID=1588 PROTO=UDP SPT=62700 DPT=161 LEN=49
Apr 12 12:02:16 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=69 TOS=0x00 PREC=0x00 TTL=128 ID=1638 PROTO=UDP SPT=62700 DPT=161 LEN=49
Apr 12 12:02:21 TestVPN kernel: Shorewall:loc2fw:REJECT:IN=enp0s29u1u4 OUT= MAC=00:24:9b:28:96:25:00:24:9b:27:d9:16:08:00 SRC=192.168.30.68 DST=192.168.30.19 LEN=69 TOS=0x00 PREC=0x00 TTL=128 ID=1677 PROTO=UDP SPT=62700 DPT=161 LEN=49
/etc/shorewall/policy
#SOURCE DEST POLICY LOG LIMIT: CONNLIMIT:
# LEVEL BURST MASK
#
# 20policy
#
loc net ACCEPT
# firewall can always connect outside
$FW net ACCEPT
# Traffic from firewall to local network is always allowed
$FW loc ACCEPT
#
# 20policy_openvpn
#
loc ovpn ACCEPT
ovpn loc ACCEPT
ovpn $FW ACCEPT
$FW ovpn ACCEPT
ovpn net ACCEPT
#
# 30policy_extra_zones
#
#
# 40policy_static
#
loc $FW REJECT info
# Drop traffic from external interface to firewall and local network
net $FW DROP info
net loc DROP info
# Drop all other traffic from external interface
net all DROP info
#
# 90reject all
#
# THE FOLLOWING POLICY MUST BE LAST
all all REJECT info
I use openvpn on nethserver in gateway mode so maybe try to replace the router with nethserver for a test. Another thing you may try is bridged mode VPN.
Hi Markus
Bridged mode that’s where this post started trying to get away from bridged Tap mode and using Tun routed.
any other suggestions?
it seems to be a routing issue from me coming in on 192.168.100.x i can ping the vpn server on the lan 192.168.30.x but i can’t see anything else any rule i need to get the two talking?
firewall.log
Apr 12 13:26:17 TestVPN kernel: Shorewall:sfilter:DROP:IN=tunrw OUT=tunrw MAC= SRC=192.168.100.6 DST=192.168.100.2 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=8679 PROTO=ICMP TYPE=8 CODE=0 ID=1 SEQ=146
Apr 12 13:26:22 TestVPN kernel: Shorewall:sfilter:DROP:IN=tunrw OUT=tunrw MAC= SRC=192.168.100.6 DST=192.168.100.2 LEN=60 TOS=0x00 PREC=0x00 TTL=127 ID=8680 PROTO=ICMP TYPE=8 CODE=0 ID=1 SEQ=147