Here are the logs :
Incoming Spam :
Jun 16 07:14:13 mattlabs postfix/smtpd[31795]: connect from 213.211.170.105.static.edpnet.net[213.211.170.105] │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; proxy; proxy_accept_socket: accepted milter connection from /var/run/rspamd/worker-proxy port 0 │
Jun 16 07:14:13 mattlabs postfix/smtpd[31795]: 30DD9C003E76: client=213.211.170.105.static.edpnet.net[213.211.170.105] │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; milter; rspamd_milter_process_command: got connection from 213.211.170.105:59798 │
Jun 16 07:14:13 mattlabs postfix/cleanup[31799]: 30DD9C003E76: message-id=<5B24DBF1.4060103@pro.wera.de> │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; proxy; rspamd_mime_text_to_utf8: converted from IBM850 to UTF-8 inlen: 799, outlen: 799 │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; proxy; rspamd_mime_text_to_utf8: converted from IBM850 to UTF-8 inlen: 1039, outlen: 1039 │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; proxy; rspamd_mime_part_detect_language: detected part language: de │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; proxy; rspamd_message_parse: loaded message; id: <5B24DBF1.4060103@pro.wera.de>; queue-id: <30DD9C003E76>; size: 3150; checksum: <af47dca4e9c800e86c11a9ab1b170│
fa4> │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; proxy; rspamd_symbols_cache_check_symbol: slow rule: XM_UA_NO_VERSION: 102986751 ticks │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; lua; neural.lua:454: trained ANN rule RFANN, save spam vector, 151 bytes │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; proxy; rspamd_task_write_log: id: <5B24DBF1.4060103@pro.wera.de>, qid: <30DD9C003E76>, ip: 213.211.170.105, from: <betakeq3@pro.wera.de>, (default: T (reject):│
[15.67/15.00] [MSBL_EBL(7.50){saintaina01@gmail.com;c0738c3509c77564a18005985f6dc3c296b9363e;},DATE_IN_FUTURE(4.00){},RECEIVED_SPAMHAUS_XBL(3.00){4.113.98.37.zen.spamhaus.org : 127.0.0.4;},AUTH_NA(1.00){},IP_│
SCORE(0.21){ip: (0.43), ipnet: 213.211.160.0/20(0.35), asn: 9031(0.22), country: BE(0.04);},MIME_GOOD(-0.10){multipart/alternative;text/plain;},BAYES_SPAM(0.06){57.87%;},ASN(0.00){asn:9031, ipnet:213.211.160.0│
/20, country:BE;},DMARC_NA(0.00){wera.de;},FROM_EQ_ENVFROM(0.00){},FROM_NO_DN(0.00){},MID_RHS_MATCH_FROM(0.00){},PREVIOUSLY_DELIVERED(0.00){myuser@gaillet.be;},RCPT_COUNT_ONE(0.00){1;},RCVD_COUNT_THREE(0.00){│
4;},RCVD_NO_TLS_LAST(0.00){},RECEIVED_SPAMHAUS(0.00){4.113.98.37.zen.spamhaus.org;},R_DKIM_NA(0.00){},R_SPF_NA(0.00){},TO_DN_NONE(0.00){},TO_MATCH_ENVRCPT_ALL(0.00){}]), len: 3150, time: 440.008ms real, 10.226│
ms virtual, dns req: 23, digest: <af47dca4e9c800e86c11a9ab1b170fa4>, rcpts: <myuser@gaillet.be>, mime_rcpts: <myuser@gaillet.be> │
Jun 16 07:14:13 mattlabs rspamd[26808]: <f8ea22>; proxy; rspamd_protocol_http_reply: regexp statistics: 0 pcre regexps scanned, 7 regexps matched, 172 regexps total, 93 regexps cached, 0B bytes scanned using p│
cre, 6.26k bytes scanned total │
Jun 16 07:14:13 mattlabs postfix/cleanup[31799]: 30DD9C003E76: milter-reject: END-OF-MESSAGE from 213.211.170.105.static.edpnet.net[213.211.170.105]: 5.7.1 Spam message rejected; from=<betakeq3@pro.wera.de> to│
=<myuser@gaillet.be> proto=ESMTP helo=<cloud.lebrass.be> │
Jun 16 07:14:13 mattlabs postfix/smtpd[31795]: disconnect from 213.211.170.105.static.edpnet.net[213.211.170.105] │
Jun 16 07:14:13 mattlabs rspamd[26808]: <d55b00>; proxy; proxy_milter_finish_handler: finished milter connection │
Jun 16 07:14:40 mattlabs rspamd[26809]: <wsrwiw>; lua; neural.lua:813: check ANN tRFANNF87B4FFCD4397E85260 │
Jun 16 07:14:40 mattlabs rspamd[26809]: <wsrwiw>; lua; neural.lua:825: no need to learn ANN tRFANNF87B4FFCD4397E85260 120 learn vectors (1000 required)
And here is the non-delivery answer :
Jun 16 22:08:37 mattlabs postfix/smtpd[8021]: connect from 213.211.170.105.static.edpnet.net[213.211.170.105] │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; proxy_accept_socket: accepted milter connection from /var/run/rspamd/worker-proxy port 0 │
Jun 16 22:08:37 mattlabs postfix/smtpd[8021]: 722BDC003E76: client=213.211.170.105.static.edpnet.net[213.211.170.105] │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; milter; rspamd_milter_process_command: got connection from 213.211.170.105:36038 │
Jun 16 22:08:37 mattlabs postfix/cleanup[8026]: 722BDC003E76: message-id=<receipt-22830566@mxsc.fl-it.net> │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_mime_part_get_cte: detected missing CTE for part as: 7bit │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_mime_part_get_cte: detected missing CTE for part as: 7bit │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_mime_part_get_cte: detected missing CTE for part as: 7bit │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_mime_part_detect_language: detected part language: en │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_mime_part_detect_language: detected part language: en │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_mime_part_detect_language: detected part language: en │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_message_parse: loaded message; id: <receipt-22830566@mxsc.fl-it.net>; queue-id: <722BDC003E76>; size: 2585; checksum: <b659223f449a0b0416a0ea5197│
1f0c6a> │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; fuzzy_generate_commands: <receipt-22830566@mxsc.fl-it.net>, part is shorter than 1000 bytes: 390 (195 * 2.00 bytes), skip fuzzy check │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; fuzzy_generate_commands: <receipt-22830566@mxsc.fl-it.net>, part is shorter than 1000 bytes: 680 (340 * 2.00 bytes), skip fuzzy check │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; fuzzy_generate_commands: <receipt-22830566@mxsc.fl-it.net>, part is shorter than 1000 bytes: 390 (195 * 2.00 bytes), use direct hash │
Jun 16 22:08:37 mattlabs rspamd[26808]: <efe725>; proxy; fuzzy_generate_commands: <receipt-22830566@mxsc.fl-it.net>, part is shorter than 1000 bytes: 680 (340 * 2.00 bytes), use direct hash │
Jun 16 22:08:38 mattlabs rspamd[26808]: <efe725>; lua; greylist.lua:255: Score too low - skip greylisting │
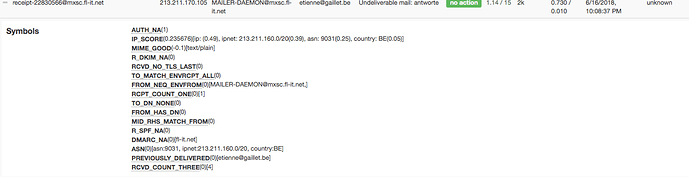
Jun 16 22:08:38 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_task_write_log: id: <receipt-22830566@mxsc.fl-it.net>, qid: <722BDC003E76>, ip: 213.211.170.105, (default: F (no action): [1.14/15.00] [AUTH_NA(1│
.00){},IP_SCORE(0.24){ip: (0.49), ipnet: 213.211.160.0/20(0.39), asn: 9031(0.25), country: BE(0.05);},MIME_GOOD(-0.10){text/plain;},ASN(0.00){asn:9031, ipnet:213.211.160.0/20, country:BE;},DMARC_NA(0.00){fl-it│
.net;},FROM_HAS_DN(0.00){},FROM_NEQ_ENVFROM(0.00){MAILER-DAEMON@mxsc.fl-it.net;;},MID_RHS_MATCH_FROM(0.00){},PREVIOUSLY_DELIVERED(0.00){myuser@gaillet.be;},RCPT_COUNT_ONE(0.00){1;},RCVD_COUNT_THREE(0.00){4;},│
RCVD_NO_TLS_LAST(0.00){},R_DKIM_NA(0.00){},R_SPF_NA(0.00){},TO_DN_NONE(0.00){},TO_MATCH_ENVRCPT_ALL(0.00){}]), len: 2585, time: 730.354ms real, 9.598ms virtual, dns req: 38, digest: <b659223f449a0b0416a0ea5197│
1f0c6a>, rcpts: <myuser@gaillet.be>, mime_rcpts: <myuser@gaillet.be> │
Jun 16 22:08:38 mattlabs rspamd[26808]: <efe725>; proxy; rspamd_protocol_http_reply: regexp statistics: 0 pcre regexps scanned, 2 regexps matched, 172 regexps total, 89 regexps cached, 0B bytes scanned using p│
cre, 5.56k bytes scanned total │
Jun 16 22:08:38 mattlabs postfix/qmgr[29031]: 722BDC003E76: from=<>, size=2842, nrcpt=1 (queue active) │
Jun 16 22:08:38 mattlabs postfix/smtpd[8021]: disconnect from 213.211.170.105.static.edpnet.net[213.211.170.105] │
Jun 16 22:08:38 mattlabs rspamd[26808]: <a8c8c9>; proxy; proxy_milter_finish_handler: finished milter connection │
Jun 16 22:08:38 mattlabs dovecot: lmtp(8029): Connect from local │
Jun 16 22:08:38 mattlabs dovecot: lmtp(8029, myuser@gaillet.be): qqyzEkZuJVtdHwAAj0go4A: sieve: msgid=<receipt-22830566@mxsc.fl-it.net>: stored mail into mailbox 'INBOX' │
Jun 16 22:08:38 mattlabs postfix/lmtp[8028]: 722BDC003E76: to=<myuser@gaillet.be>, relay=mattlabs.gaillet.be[/var/run/dovecot/lmtp], delay=1, delays=0.84/0.02/0/0.18, dsn=2.0.0, status=sent (250 2.0.0 <etienn│
e@gaillet.be> qqyzEkZuJVtdHwAAj0go4A Saved) │
Jun 16 22:08:38 mattlabs dovecot: lmtp(8029): Disconnect from local: Successful quit │
Jun 16 22:08:38 mattlabs postfix/qmgr[29031]: 722BDC003E76: removed
Here are the spam tags in a more readable form :
For the record :
Backscatter (also known as outscatter, misdirected bounces, blowback or collateral spam) is incorrectly automated bounce messages sent by mail servers, typically as a side effect of incoming spam.
Recipients of such messages see them as a form of unsolicited bulk email or spam, because they were not solicited by the recipients, are substantially similar to each other, and are delivered in bulk quantities. Systems that generate email backscatter may be listed on various email blacklists and may be in violation of internet service providers’ Terms of Service.
source : Backscatter (email) - Wikipedia