Hi All
I did - a while ago - say I would attempt a fair, neutral look at NethSecurity 8. I do admit liking OPNsense as Open Source firewall and still mostly use OPNsense.
Due to the almost unbeatable price for Unifis newer UCG-Ultra / UCG-Max firewalls I have started using these boxes. Even on “cheap” China-Boards / Boxes, and using OPNsense or any other Open Source firewall, I can not beat the thruput / price / features / size of these hardware.
As I am also a longtime advocate of independant firewall as a box, my first test of NethSecurity will be on a suitable box, here a PCengines APU box. These have a AMD G-T40E Processor running at 1 GHz, 4 GB RAM and 3 Realtec NICs and this model is equipped with a 120 GB SSD. I do have a set of the newer APU4d4 boxes, with a Quadcore AMD, and 4 Intel GBE NICs, but otherwise not much difference. The Quad core is a mite more performant, yes.
So, after downloading and flashing the live/installer image with BalenaEtcher and booting from USB:
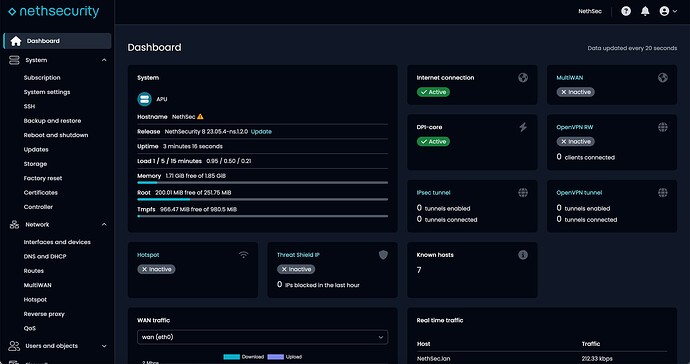
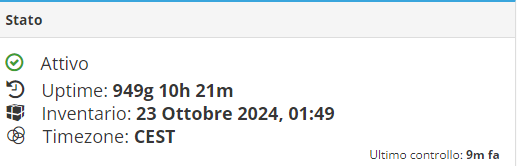
First impression: nice
Hardware recognized as APU (upper left).
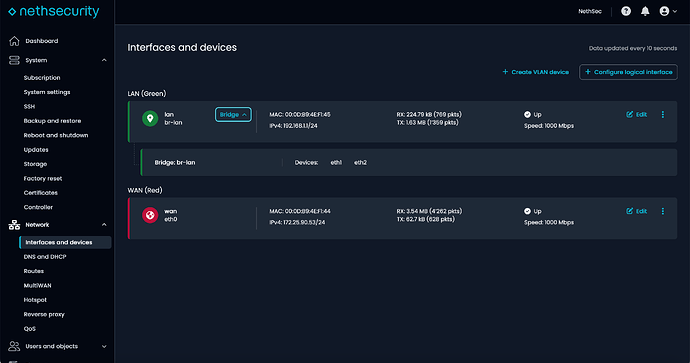
First BIG question: What is this?
Without any information, NICs 1 & 2 are bridged (even though 2 is not used or even connected…).
Really BAD !
It gets worse: 20 years after Microsoft and the rest of the world tried to stop people from using the stupid Pre 2000 Microsoft suggestion of using .local or .lan as a domain name, some still pushes this very bad security suggestion in using .lan as domain name.
Already plenty of poats in the forum of people with Mail, AD, LE and other issues due to installing their system on .lan…
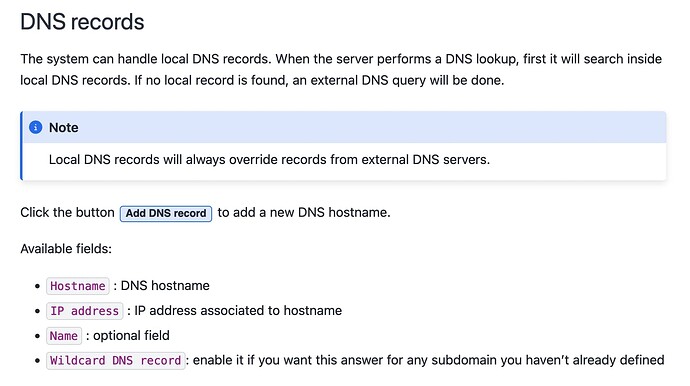
Only A records, no CNAMES, PTR, TXT, SVR, MX or other records in DNS?
Sure I can use CLI to edit the config for DNSmasq - but I’ll be honest. I am a user of OpenWRT, which uses DNSmasq AND provides a halfway usable Web-GUI. NethSecurity, based on OpenWRT, still shows a extremly primitive, basically unusable interface.
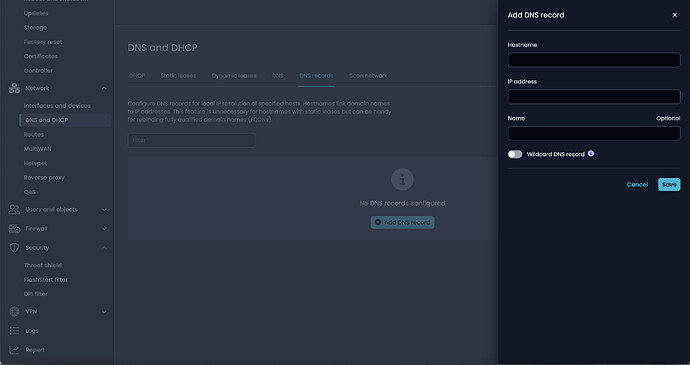
The field “Name”:
Very clear information… Is the “name” field a remark or comment / notes field, or is the “name” something important - DNS is about Names after all…
Not good at all!
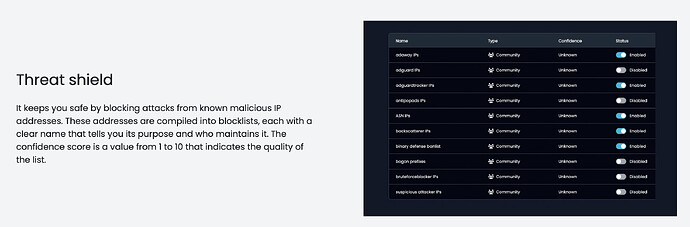
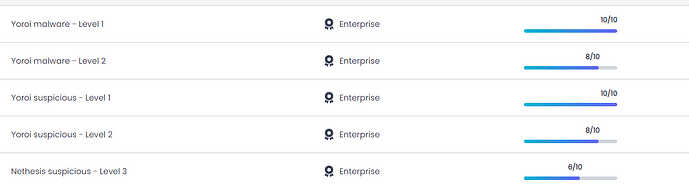
Next one: Threat shield
As the website already states:
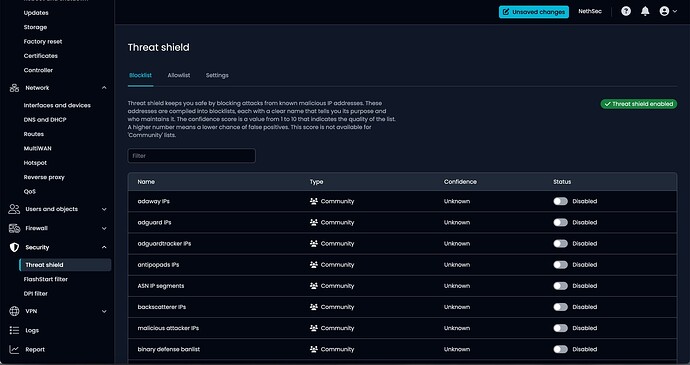
Yet even here, nothing is clearly stated. All Maintainers are called “Community”. And all Confidance is unknown.
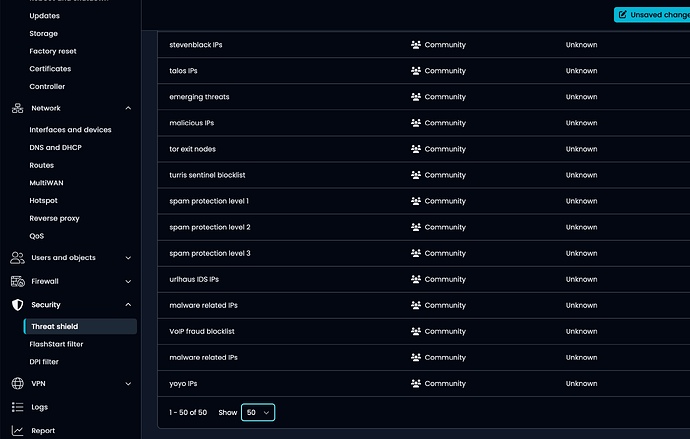
Of 50, none have anything other than “community” and Unknown Confidance…
Other projects at least display one suggestion…
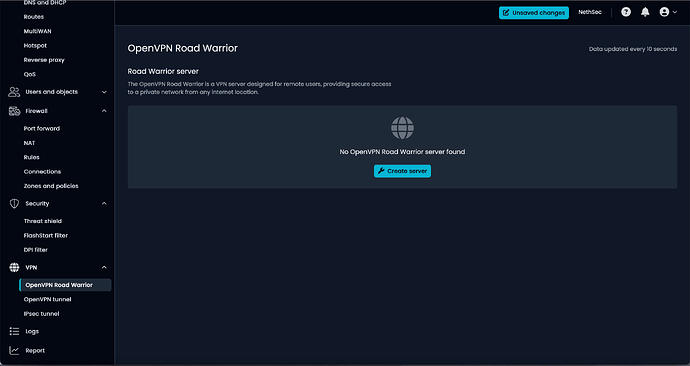
During installation/ booting, I did recall seeing Wireguard installed. Where are any Wireguard VPN options?
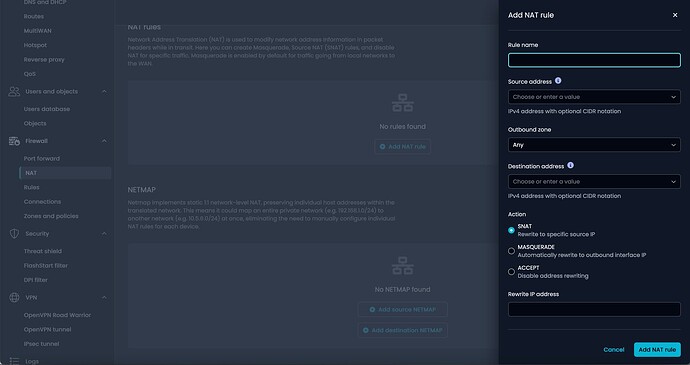
Firewalling seems to emphasize the use of Masquerading in the NAT settings:
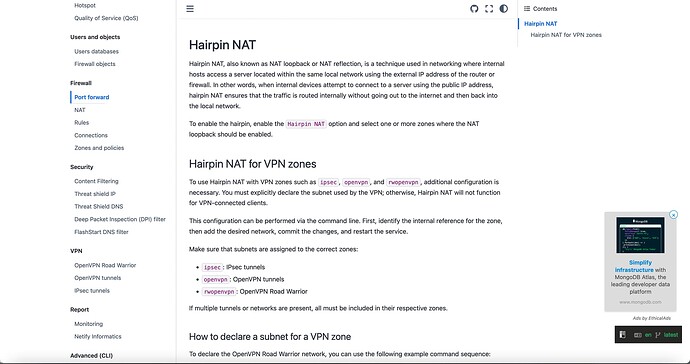
Masquerading isn’t used in the Docs, which talk about “Hairpin NAT”
And fact is: Hairpin NAT or Masquerading are only “stupid” workarounds for peple who do not really understand DNS or Split-DNS, the only correct way to handle this problem introduced by NAT.
The only mention of Split-DNS I could find in the docs:
People who do not understand the basic workings of the Internet (And DNS is one of the most Important of all underlying services) are just a risk for any other Internet operator or server admin. The risk for Spam and more just increase…
Bliss through Ignorance is a bit like the much cited Security by Obscurity…
Security by Obscurity
A typical one is changing the SSH port.
→ While this does result in less log file entries, it does NOT increase security in any way.
Today, it’s no more the 1990ies, any half-baked script-kiddie has access to Port-Scanners and can Google how to use them in a simple attack vector… Sheesh!
There are only about 65000 ports, any scanner with a current CPU will take a few milliseconds more to probe all ports for a ssh demon listening in the background. Code-wise? A one liner will cover it!
Updating System:
Since the recent release of NethSecurity project milestone 8.3, the update is a bit smoother.
No more fatal error on the screen but the nethSecurity box still reboots silently in the background.
This hardware does include a beeper, OPNsense has a GUI option to sound this for booting and shutdowns, a good option to have and use when available.
A silent reboot without ANY info is really uncool. It’s 2024, provide feedback on what the box is doing!
Conclusion
Sorry guys! While I’m still fully behind NS8, NethSecurity seems not quite at the level…
Not only is NethSecurity very lacking in Key functions, “sensible” suggestions are also very lacking, like which Threatshield lists are better or not (At least suggest one!). Others (competitors) do!
But the fact that NethSecurity still endorses very old strategies and mindsets is generally not a good thing for the Internet.
While I happen to have a good comprehension of how DNS works back and forth, I am aware that for most others DNS is a sealed book. But DNS strategies should be at least mentionned and important ones like split-dns emphasized.
The fact that I will find wrong hostnames or fqdns in logfiles when trying to solve issues is often due to the fact that CNAME can’t be used from the GUI, neither can incorrect PTR records be purged or corrected. Most of these stem from the fact that several A records are used instaed of a single A record and several CNAME records, resulting in a single, correct PTR record.
Having to additionally manually sieve out these false records when comparing logfiles is additionally error-prone, a less than ideal situation for any firewall operator!
Summary:
Good:
- Clean GUI
- Fairly responsive GUI
- Correct hardware identification
Bad / Stupid presumptions:
- Unasked for, unlogical “bridging” of two NICs
- Unfinished look and feel for Threat Shield, lacking preset suggestions
- Use of .lan as default domain name
- Non working LetsEncrypt options if set up using a .lan domain…
- Missing WireGuard options
- No usable DNS (which doesn’t give back wrong information.)
- GUI and Docu are in several places “out of sync” or do not contain any usefull information, like “Name” field in DNS.
- Fast, silent reboot without ANY information when updating.
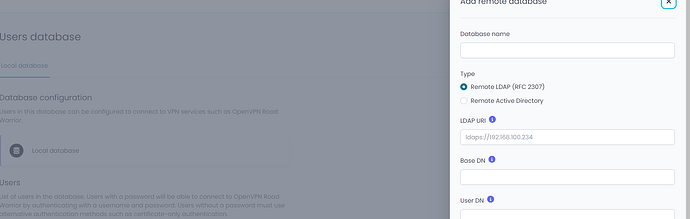
- Locking down LDAP or AD as a data source (for example a typical use is for VPN Road Warrior use) in a Open-Source firewall is just not cool, nor really acceptable nowadays. NS7 did have “Account provider” access built in, a major “downgrade”.
- The fact that an optional Phone-Home for Nethesis to get user data and stats and win additional clients by using this info to provide a free per device stats interface for users seems like a missed opportunity to me
- Too many key services of NethSecurity 8 as firewall are dependant on external services. It’s OK for me if we are talking about updated blacklists or Antiivirus signatures. If not current, a day old, OK. But DPI to use Netify? Other firewalls can do self contained DPI…
- Same eg goes for the Hotspot. To use a Hotspot, even if I explicitely do not want or allow Social Media logins, I still have to setup an Ikaro service in the cloud somewhere, or use Nethesis own Ikaro server. OPNsense handles a Hotspot with Ticket system all internally, self contained. Such reliance on external services would already be a showstopper for several client use cases I have, as the server is isolated and serves an isolated network (Eg a school).
At the moment, I do not deem this product really usefull for any of my clients or myself, neither for Office, Home or Lab use. I will keep an eye open in the near future, and probably keep a VM running to play around, but I will not be dedicating hardware at the moment.
A small note to using hard-coded colors in firewalling: The Red / Green basics:
It is a true and well known fact that most people in IT and Networking are male.
It’s also true, but much less well known that color-blindness is a mostly birth deficiency (Not intended as any form of insult or disregard) in males…
And color-blindness mainly affect green and red…
Depending on race / region, the values for infliction can reach 20% of males…
In traffic lights, they (color-blind people) can help themselves as the position of Red and Green are always top or left for Red, and bottom or right for green. (Only one known exception to this rule, and that’s the light in new York, Green on Top!).
On a firewall table, not seeing green and red priorities is a major disadvantage. And not being able to choose more appropriate, visible colors for themselves makes it doubly worse!
I am myself not inflicted with color-blindness, but in my professional life I have often met up with people having this issue…
My 2 cents
Andy
Note to all: I have actually done this installation to SSD, but some screenshots were missed. So redone everything again, but only as “live” system for documentation purposes.