Hi,
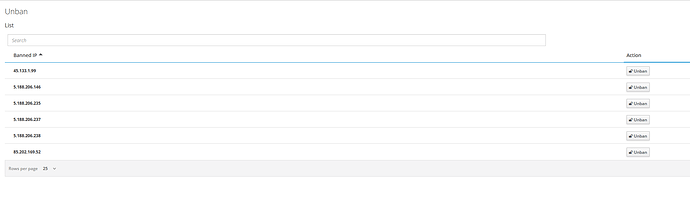
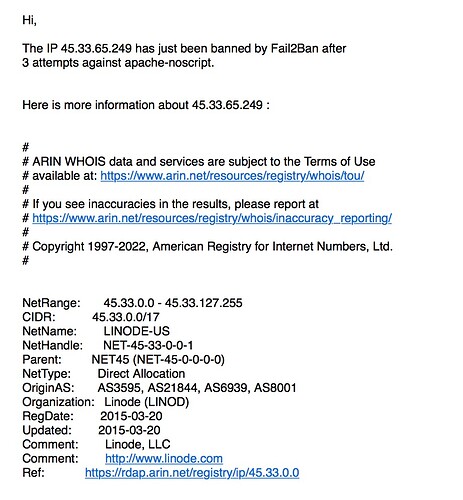
today I was looking up my NAT-list on my router (Hardware). I found a lot of entries on open sessions for the Nethserver. One IP, 45.133.1.99, occurs very often for Port 25:
By Change: Does this look similar with you, does anybody know that IP, do I need to fear some intrusion?
TIA
Thorsten
|Private IP|:Port|#Pseudo-Port|Peer-IP|:Port|Interface|
|172.17.0.12|25|25|45.133.1.99|59016|WAN1|
|172.17.0.12|25|25|45.133.1.99|59029|WAN1|
|172.17.0.12|25|25|45.133.1.99|59059|WAN1|
|172.17.0.12|25|25|45.133.1.99|59219|WAN1|
|172.17.0.12|25|25|45.133.1.99|59110|WAN1|
|172.17.0.12|25|25|45.133.1.99|59117|WAN1|
|172.17.0.12|25|25|45.133.1.99|59138|WAN1|
|172.17.0.12|25|25|45.133.1.99|59139|WAN1|
|172.17.0.12|25|25|85.202.169.52|62276|WAN1|
|172.17.0.12|25|25|45.133.1.99|59283|WAN1|
|172.17.0.12|25|25|85.202.169.52|62191|WAN1|
|172.17.0.12|25|25|45.133.1.99|59185|WAN1|
|172.17.0.12|25|25|85.202.169.52|62323|WAN1|
|172.17.0.12|25|25|45.133.1.99|59417|WAN1|
|172.17.0.12|25|25|45.133.1.99|59424|WAN1|
|172.17.0.12|25|25|45.133.1.99|59425|WAN1|
|172.17.0.12|25|25|45.133.1.99|59478|WAN1|
|172.17.0.12|25|25|45.133.1.99|59482|WAN1|
|172.17.0.12|25|25|45.133.1.99|59489|WAN1|
|172.17.0.12|25|25|45.133.1.99|59490|WAN1|
|172.17.0.12|25|25|85.202.169.52|62509|WAN1|
|172.17.0.12|25|25|45.133.1.99|59548|WAN1|
|172.17.0.12|25|25|85.202.169.52|62581|WAN1|
|172.17.0.12|25|25|45.133.1.99|59623|WAN1|
|172.17.0.12|25|25|45.133.1.99|59750|WAN1|
|172.17.0.12|25|25|85.202.169.52|62769|WAN1|
|172.17.0.12|25|25|45.133.1.99|59768|WAN1|
|172.17.0.12|25|25|45.133.1.99|59800|WAN1|
|172.17.0.12|25|25|45.133.1.99|59949|WAN1|
|172.17.0.12|25|25|45.133.1.99|59957|WAN1|
|172.17.0.12|25|25|85.202.169.52|63001|WAN1|
|172.17.0.12|25|25|45.133.1.99|60007|WAN1|
|172.17.0.12|25|25|45.133.1.99|60019|WAN1|
|172.17.0.12|25|25|85.202.169.52|63085|WAN1|
|172.17.0.12|25|25|45.133.1.99|60089|WAN1|
|172.17.0.12|25|25|45.133.1.99|60113|WAN1|
|172.17.0.12|25|25|85.202.169.52|63157|WAN1|
|172.17.0.12|25|25|45.133.1.99|60179|WAN1|
|172.17.0.12|25|25|45.133.1.99|60211|WAN1|
|172.17.0.12|25|25|45.133.1.99|60303|WAN1|
|172.17.0.12|25|25|45.133.1.99|60348|WAN1|
|172.17.0.12|65151|33919|1.1.1.1|53|WAN1|
|172.17.0.12|65151|33919|8.8.8.8|53|WAN1|
|172.17.0.12|25|25|45.133.1.99|60376|WAN1|
|172.17.0.12|25|25|85.202.169.52|63443|WAN1|
|172.17.0.12|25|25|85.202.169.52|63485|WAN1|
|172.17.0.12|25|25|45.133.1.99|60489|WAN1|
|172.17.0.12|25|25|85.202.169.52|63521|WAN1|
|172.17.0.12|25|25|45.133.1.99|60513|WAN1|
|172.17.0.12|25|25|45.133.1.99|60616|WAN1|
|172.17.0.12|25|25|45.133.1.99|60688|WAN1|
|172.17.0.12|25|25|45.133.1.99|60689|WAN1|
|172.17.0.12|25|25|45.133.1.99|60782|WAN1|
|172.17.0.12|25|25|45.133.1.99|60827|WAN1|
|172.17.0.12|25|25|45.133.1.99|60835|WAN1|
|172.17.0.12|25|25|45.133.1.99|60848|WAN1|
|172.17.0.12|25|25|45.133.1.99|60878|WAN1|
|172.17.0.12|25|25|45.133.1.99|60886|WAN1|
|172.17.0.12|25|25|45.133.1.99|60887|WAN1|
|172.17.0.12|25|25|45.133.1.99|60935|WAN1|
|172.17.0.12|25|25|45.133.1.99|61048|WAN1|
|172.17.0.12|25|25|45.133.1.99|61153|WAN1|
|172.17.0.12|25|25|45.133.1.99|61206|WAN1|
|172.17.0.12|25|25|45.133.1.99|61230|WAN1|
|172.17.0.12|25|25|45.133.1.99|61320|WAN1|
|172.17.0.12|25|25|45.133.1.99|61408|WAN1|
|172.17.0.12|25|25|45.133.1.99|61418|WAN1|
|172.17.0.12|25|25|195.133.40.113|60600|WAN1|
|172.17.0.12|25|25|45.133.1.99|61541|WAN1|
|172.17.0.12|25|25|45.133.1.99|61572|WAN1|
|172.17.0.12|25|25|45.133.1.99|61614|WAN1|
|172.17.0.12|25|25|45.133.1.99|61667|WAN1|
|172.17.0.12|25|25|45.133.1.99|61672|WAN1|
|172.17.0.12|25|25|85.202.169.52|64687|WAN1|
|172.17.0.12|25|25|45.133.1.99|61741|WAN1|
|172.17.0.12|25|25|45.133.1.99|61746|WAN1|
|172.17.0.12|33809|35345|162159200123|123|WAN1|
|172.17.0.12|25|25|45.133.1.99|61823|WAN1|
|172.17.0.12|25|25|85.202.169.52|64844|WAN1|
|172.17.0.12|25|25|45.133.1.99|61843|WAN1|
|172.17.0.12|25|25|45.133.1.99|61897|WAN1|
|172.17.0.12|25|25|45.133.1.99|61940|WAN1|
|172.17.0.12|34023|35559|130.60.204.10|123|WAN1|
|172.17.0.12|25|25|45.133.1.99|61994|WAN1|
|172.17.0.12|25|25|45.133.1.99|62018|WAN1|