Continuing the discussion from Bandwith problem:
I think we should separate this discussion
Continuing the discussion from Bandwith problem:
I think we should separate this discussion
IMHO, snort defaults in 6.7 protect against a very low number of threats. But security needs many layers, one more is always better. And you may have customized snort as I did.
To use snort with an high bandwidth link as yours, you need a lot of cpu power.
The tests made by @EddieA seem to prove that the number of rules is not affecting a lot bandwidth cutoff, but my old tests (with much lower bandwidth) told another story: rules number made a substantial difference.
I’m working on snort on 7, but I still haven’t tested performances. With a few rules and a weak cpu I can reach 30 mibt/s.
May be interesting:
Suricata is much better because it can use multiple cores (snort 3 will, but it’s in alpha).
As I said in the past, it wasn’t stable enough when we had to take a decision on NethServer 6.5.
I think that it’s now much better, it even landed in epel, so it will be a metter of minutes to have it on NS.
But I’m exploring application ID on snort for 7 and AFAIK suricata is still missign such a feature.
suricata have much more interessing features like ip reputation, and perform much better on multicpu.
flowbit:
https://redmine.openinfosecfoundation.org/projects/suricata/wiki/Flow-keywords
ip rep:
https://redmine.openinfosecfoundation.org/projects/suricata/wiki/IP_Reputation
this is an old (2010) article on suricata performance…
As result, Suricata is Multi-threaded so, it may be faster.
That’s what I think too. Can anybody help with howto install suricata on nethserver?
That’s a great idea, does anyone want to give it a try?
Now I’m using suricata on my pfsense firewall (now a VM in nethserver!  ) and works great…i use both ET open and VRT paid rules (18600+ rules)…no problem with my slow 20 mbps connection
) and works great…i use both ET open and VRT paid rules (18600+ rules)…no problem with my slow 20 mbps connection 
Never crashed in one year 
I’ll have to give it a try sometime once I get the time
Me too 
Uh don’t fight guys  There’s room for all @bwdjames
There’s room for all @bwdjames
Please share your achivements and notes as soon as possibile. I’m eager to know how things are going
Start testing with:
yum -y install gcc libpcap-devel pcre-devel libyaml-devel file-devel
zlib-devel jansson-devel nss-devel libcap-ng-devel libnet-devel tar make
libnetfilter_queue-devel lua-devel
wget http://www.openinfosecfoundation.org/download/suricata-3.0.1.tar.gz
tar -xvzf suricata-3.0.tar.gz
cd suricata-3.0
./configure --prefix=/usr --sysconfdir=/etc --localstatedir=/var --enable-nfqueue --enable-lua
make install-full
LD_LIBRARY_PATH=/usr/lib /usr/bin/suricata -c /etc/suricata//suricata.yaml -i eth0
For now all ok (install) =) i have to test if it work ![]() …no more time today
…no more time today ![]()
NB: clamav show the rules as virus (false positive)…so if you have a proxy with clamav scan will block it! ![]()
Nice job, let’s keep the ball rolling
I’d use a much “simpler” command:
yum install http://codemonkey.net/files/rpm/suricata/stable/epel-7-x86_64/suricata-3.0-0.1.el7.x86_64.rpm
You’ll get 3.0.0 instead of 3.0.1, but it’s a matter of time for the latest version to be released.
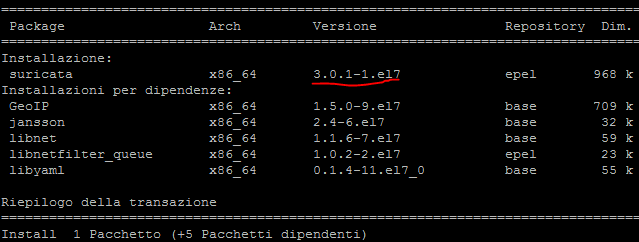
=)
Install suricata and download oinkmaster:
yum install suricata -y
wget http://prdownloads.sourceforge.net/oinkmaster/oinkmaster-2.0.tar.gz
tar xzf oinkmaster-2.0.tar.gz
mkdir /etc/oinkmaster
mv oinkmaster-2.0/* /etc/oinkmaster/
yum install nano -y
Edit oinkmaster config:
nano /etc/oinkmaster/oinkmaster.conf
Add: “url = http://rules.emergingthreats.net/open/suricata/emerging.rules.tar.gz”
Run oinkmaster:
/etc/oinkmaster/oinkmaster.pl -C /etc/oinkmaster/oinkmaster.conf -o /etc/suricata/rules
Edit suricata config:
nano /etc/suricata/suricata.yaml
My NIC (or VM?) need this change to avoid SURICATA TCPv4 invalid checksum [**] [Classification: (null)] [Priority: 3] rule to be triggered:
checksum-validation: yes -> checksum-validation: no
search for:
# Set the default rule path here to search for the files.
# if not set, it will look at the current working dir
default-rule-path: /etc/suricata/rules
rule-files:
and change the list of rule to use according to your needs (this is mine):
- botcc.rules
- ciarmy.rules
- compromised.rules
- drop.rules
- dshield.rules
- emerging-activex.rules
- emerging-attack_response.rules
# - emerging-chat.rules
# - emerging-current_events.rules
- emerging-dns.rules
- emerging-dos.rules
- emerging-exploit.rules
# - emerging-ftp.rules
# - emerging-games.rules
# - emerging-icmp_info.rules
# - emerging-icmp.rules
- emerging-imap.rules
- emerging-inappropriate.rules
- emerging-malware.rules
- emerging-misc.rules
- emerging-mobile_malware.rules
# - emerging-netbios.rules
- emerging-p2p.rules
# - emerging-policy.rules
- emerging-pop3.rules
# - emerging-rpc.rules
# - emerging-scada.rules
- emerging-scan.rules
# - emerging-shellcode.rules
- emerging-smtp.rules
# - emerging-snmp.rules
- emerging-sql.rules
# - emerging-telnet.rules
# - emerging-tftp.rules
- emerging-trojan.rules
# - emerging-user_agents.rules
# - emerging-voip.rules
- emerging-web_client.rules
- emerging-web_server.rules
# - emerging-web_specific_apps.rules
- emerging-worm.rules
- tor.rules
- decoder-events.rules # available in suricata sources under rules dir
- stream-events.rules # available in suricata sources under rules dir
- http-events.rules # available in suricata sources under rules dir
- smtp-events.rules # available in suricata sources under rules dir
- dns-events.rules # available in suricata sources under rules dir
- tls-events.rules # available in suricata sources under rules dir
# - modbus-events.rules # available in suricata sources under rules dir
- app-layer-events.rules # available in suricata sources under rules dir
then:
suricata -i eth0
To autoupdate rules, cron: /etc/oinkmaster/oinkmaster.pl -C /etc/oinkmaster/oinkmaster.conf -o /etc/suricata/rules
and restart suricata 
Note you can simply:
yum install suricata -y
wget http://rules.emergingthreats.net/open/suricata/emerging.rules.tar.gz
tar xzf emerging.rules.tar.gz
mv rules/* /etc/suricata/rules/
em rules
suricata -i eth0
but will use the standard suricata config
Sorry it’s a bit confusing 

Thanks guys! I’ll give this a try sometime. I would try it straight away but I have something urgent work-related tasks to complete first. Will be providing feedback once I have given it a try
in this way, and with only one NIC, it work as IDS…some one can try it in IPS mode? 