NethServer Version: NS 7.4.1708
Module: Accounts provider
Hi there,
I’ve got a failure when joining a NS7 instance to an existing NS7-AD.
Every time I press save this failure appears.
This is what happens in messages.log :
Feb 22 08:42:04 nethgate esmith::event[16102]: Event: nethserver-sssd-save
Feb 22 08:42:04 nethgate systemd: Stopping System Security Services Daemon...
Feb 22 08:42:04 nethgate sssd[be[jeckel.lan]]: Shutting down
Feb 22 08:42:04 nethgate sssd[nss]: Shutting down
Feb 22 08:42:04 nethgate sssd[pam]: Shutting down
Feb 22 08:42:04 nethgate systemd: Stopped System Security Services Daemon.
Feb 22 08:42:04 nethgate esmith::event[16102]: [NOTICE] wipe out sssd databases and configuration
Feb 22 08:42:05 nethgate esmith::event[16102]: Action: /etc/e-smith/events/nethserver-sssd-save/S01nethserver-sssd-cleanup SUCCESS [0.042585]
Feb 22 08:42:05 nethgate esmith::event[16102]: expanding /etc/backup-config.d/nethserver-sssd.include
Feb 22 08:42:05 nethgate esmith::event[16102]: expanding /etc/openldap/ldap.conf
Feb 22 08:42:05 nethgate esmith::event[16102]: expanding /etc/samba/smb.conf
Feb 22 08:42:05 nethgate esmith::event[16102]: expanding /etc/sssd/sssd.conf
Feb 22 08:42:05 nethgate esmith::event[16102]: Action: /etc/e-smith/events/actions/generic_template_expand SUCCESS [0.524114]
Feb 22 08:42:06 nethgate esmith::event[16102]: Action: /etc/e-smith/events/nethserver-sssd-save/S20nethserver-sssd-conf SUCCESS [0.582505]
Feb 22 08:42:07 nethgate esmith::event[16102]: [ERROR] /usr/libexec/nethserver/smbads: failed to add service primaries to system keytab
Feb 22 08:42:07 nethgate esmith::event[16102]: [ERROR] /usr/libexec/nethserver/smbads: failed to initialize keytabs
Feb 22 08:42:07 nethgate esmith::event[16102]: Action: /etc/e-smith/events/nethserver-sssd-save/S30nethserver-sssd-initkeytabs FAILED: 5 [1.043591]
Feb 22 08:42:07 nethgate esmith::event[16102]: [WARNING] DEPRECATED! Package nethserver-squid must subscribe nethserver-sssd-save event explicitly
Feb 22 08:42:07 nethgate esmith::event[16143]: Event: nethserver-squid-update
Feb 22 08:42:07 nethgate esmith::event[16143]: Migrating existing database configuration
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database certificates
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database networks
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database routes
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database accounts
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database hosts
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database proxypass
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database fwrules
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database fwservices
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database portforward
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database tc
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database dhcp
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database squid
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database contentfilter
Feb 22 08:42:08 nethgate esmith::event[16143]: Migrating existing database vpn
Feb 22 08:42:08 nethgate esmith::event[16143]: Action: /etc/e-smith/events/nethserver-squid-update/S00initialize-default-databases SUCCESS [0.790435]
Feb 22 08:42:08 nethgate esmith::event[16143]: expanding /etc/dnsmasq.conf
Feb 22 08:42:08 nethgate esmith::event[16143]: expanding /etc/hosts
Feb 22 08:42:08 nethgate esmith::event[16143]: expanding /etc/httpd/conf.d/wpad.conf
Feb 22 08:42:08 nethgate esmith::event[16143]: expanding /etc/squid/squid.conf
Feb 22 08:42:08 nethgate esmith::event[16143]: expanding /etc/squid/acls/no_cache.acl
Feb 22 08:42:08 nethgate esmith::event[16143]: expanding /etc/sysconfig/squid
Feb 22 08:42:08 nethgate esmith::event[16143]: expanding /var/www/html/wpad.dat
Feb 22 08:42:08 nethgate esmith::event[16143]: Action: /etc/e-smith/events/actions/generic_template_expand SUCCESS [0.669686]
Feb 22 08:42:10 nethgate esmith::event[16143]: [ERROR] /usr/libexec/nethserver/smbads: failed to add service primaries to system keytab
Feb 22 08:42:10 nethgate esmith::event[16143]: [ERROR] /usr/libexec/nethserver/smbads: failed to initialize keytabs
Feb 22 08:42:10 nethgate esmith::event[16143]: Action: /etc/e-smith/events/nethserver-squid-update/S20nethserver-sssd-initkeytabs FAILED: 5 [1.031963]
Feb 22 08:42:10 nethgate esmith::event[16143]: Action: /etc/e-smith/events/nethserver-squid-update/S30nethserver-squid-check-cache SUCCESS [0.299078]
Feb 22 08:42:10 nethgate esmith::event[16143]: Name: squid-bypass
Feb 22 08:42:10 nethgate esmith::event[16143]: Type: hash:ip
Feb 22 08:42:10 nethgate esmith::event[16143]: Revision: 1
Feb 22 08:42:10 nethgate esmith::event[16143]: Header: family inet hashsize 1024 maxelem 65536 timeout 43200
Feb 22 08:42:10 nethgate esmith::event[16143]: Size in memory: 16528
Feb 22 08:42:10 nethgate esmith::event[16143]: References: 2
Feb 22 08:42:10 nethgate esmith::event[16143]: Members:
Feb 22 08:42:10 nethgate esmith::event[16143]: Action: /etc/e-smith/events/nethserver-squid-update/S50nethserver-squid-ipset SUCCESS [0.012119]
Feb 22 08:42:10 nethgate systemd: Reloading.
Feb 22 08:42:10 nethgate esmith::event[16143]: [INFO] service dnsmasq restart
Feb 22 08:42:10 nethgate systemd: Stopping DNS caching server....
Feb 22 08:42:10 nethgate dnsmasq[15949]: exiting on receipt of SIGTERM
Feb 22 08:42:10 nethgate systemd: Starting DNS caching server....
Feb 22 08:42:10 nethgate nethserver-squid-ipset: Name: squid-bypass
Feb 22 08:42:10 nethgate nethserver-squid-ipset: Type: hash:ip
Feb 22 08:42:10 nethgate nethserver-squid-ipset: Revision: 1
Feb 22 08:42:10 nethgate nethserver-squid-ipset: Header: family inet hashsize 1024 maxelem 65536 timeout 43200
Feb 22 08:42:10 nethgate nethserver-squid-ipset: Size in memory: 16528
Feb 22 08:42:10 nethgate nethserver-squid-ipset: References: 2
Feb 22 08:42:10 nethgate nethserver-squid-ipset: Members:
Feb 22 08:42:10 nethgate systemd: Started DNS caching server..
Feb 22 08:42:10 nethgate dnsmasq[16188]: started, version 2.76 cachesize 4000
Feb 22 08:42:10 nethgate dnsmasq[16188]: compile time options: IPv6 GNU-getopt DBus no-i18n IDN DHCP DHCPv6 no-Lua TFTP no-conntrack ipset auth no-DNSSEC loop-detect inotify
Feb 22 08:42:10 nethgate dnsmasq-tftp[16188]: TFTP root is /var/lib/tftpboot
Feb 22 08:42:10 nethgate dnsmasq[16188]: using nameserver 192.168.0.237#53 for domain ad.jeckel.lan
Feb 22 08:42:10 nethgate dnsmasq[16188]: using nameserver 8.8.4.4#53
Feb 22 08:42:10 nethgate dnsmasq[16188]: using nameserver 8.8.8.8#53
Feb 22 08:42:10 nethgate dnsmasq[16188]: using nameserver 192.168.0.236#53
Feb 22 08:42:10 nethgate dnsmasq[16188]: read /etc/hosts - 7 addresses
Feb 22 08:42:10 nethgate systemd: Reloading.
Feb 22 08:42:11 nethgate esmith::event[16143]: [INFO] service httpd reload
Feb 22 08:42:11 nethgate systemd: Reloaded The Apache HTTP Server.
Feb 22 08:42:11 nethgate systemd: Reloading.
Feb 22 08:42:11 nethgate esmith::event[16143]: [INFO] service squid restart
Feb 22 08:42:11 nethgate systemd: Stopping Squid caching proxy...
Feb 22 08:42:11 nethgate squid: 2018/02/22 08:42:11| Warning: empty ACL: acl no_cache dstdomain "/etc/squid/acls/no_cache.acl"
Feb 22 08:42:11 nethgate systemd: Starting Squid caching proxy...
Feb 22 08:42:11 nethgate squid: 2018/02/22 08:42:11| Warning: empty ACL: acl no_cache dstdomain "/etc/squid/acls/no_cache.acl"
Feb 22 08:42:11 nethgate squid[16248]: Squid Parent: will start 1 kids
Feb 22 08:42:11 nethgate squid[16248]: Squid Parent: (squid-1) process 16250 started
Feb 22 08:42:11 nethgate systemd: Started Squid caching proxy.
Feb 22 08:42:11 nethgate esmith::event[16143]: Action: /etc/e-smith/events/actions/adjust-services SUCCESS [1.354494]
Feb 22 08:42:11 nethgate esmith::event[16143]: Event: nethserver-squid-update FAILED
Feb 22 08:42:11 nethgate esmith::event[16102]: Action: /etc/e-smith/events/nethserver-sssd-save/S80nethserver-sssd-notifyclients FAILED: 1 [4.530151]
Feb 22 08:42:12 nethgate systemd: Reloading.
Feb 22 08:42:12 nethgate systemd: Starting System Security Services Daemon...
Feb 22 08:42:12 nethgate sssd: Starting up
Feb 22 08:42:12 nethgate sssd[be[jeckel.lan]]: Starting up
Feb 22 08:42:12 nethgate sssd[nss]: Starting up
Feb 22 08:42:12 nethgate sssd[pam]: Starting up
Feb 22 08:42:12 nethgate systemd: Started System Security Services Daemon.
Feb 22 08:42:12 nethgate esmith::event[16102]: [INFO] sssd has been started
Feb 22 08:42:12 nethgate esmith::event[16102]: Action: /etc/e-smith/events/actions/adjust-services SUCCESS [0.906522]
Feb 22 08:42:12 nethgate esmith::event[16102]: Event: nethserver-sssd-save FAILED
Feb 22 08:42:13 nethgate sssd: tkey query failed: GSSAPI error: Major = Unspecified GSS failure. Minor code may provide more information, Minor = Server not found in Kerberos database.
Feb 22 08:42:13 nethgate sssd: tkey query failed: GSSAPI error: Major = Unspecified GSS failure. Minor code may provide more information, Minor = Server not found in Kerberos database.
Feb 22 08:42:13 nethgate sssd: tkey query failed: GSSAPI error: Major = Unspecified GSS failure. Minor code may provide more information, Minor = Server not found in Kerberos database.
Feb 22 08:42:13 nethgate sssd: tkey query failed: GSSAPI error: Major = Unspecified GSS failure. Minor code may provide more information, Minor = Server not found in Kerberos database.
Feb 22 08:42:13 nethgate sssd: tkey query failed: GSSAPI error: Major = Unspecified GSS failure. Minor code may provide more information, Minor = Server not found in Kerberos database.
The “nethgate” is to join. It’s a gateway with Firewall, proxy, webfiltering and so on, red and green interface. “ns7ad1” is a NS7 AD with fileserver, nextcloud, sogo, and so on, only green interface.
The “ldap-nethgate” user is a user I created on the AD only for this purpose, as in the docs discribed.
What did I do wrong??? 

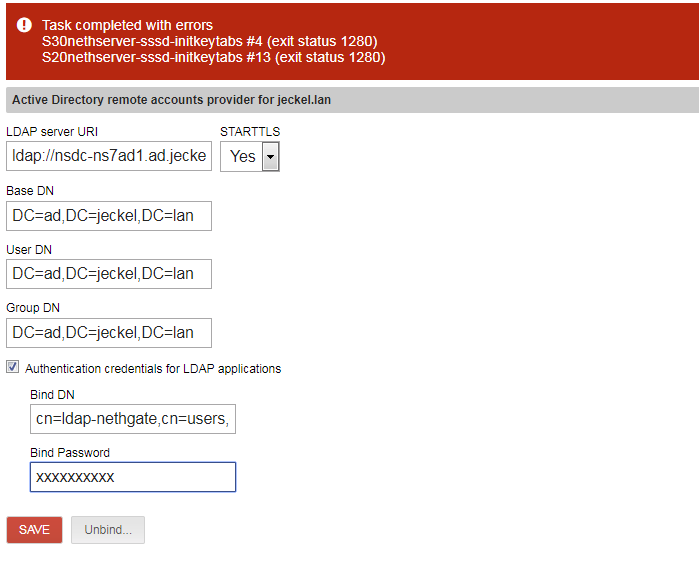
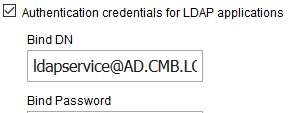
 and until tomorrow.
and until tomorrow. 