I will do so asap. But first things first. What is it all about with this share.
We have a local server A with its shares where users can access with read-write permissions, server A also provides the roaming profiles and redirected folders among other things.
Then there is remote server B which has a share that should only be accessible limitedly. Domain users should not be able to write to this share. With a cronjob on server B the folders from server A are rsynced every quarter of an hour.
The corresponding command for the rsync job is:
sync -a -e ‘ssh -p customportnumber’ root@servera:/var/lib/nethserver/ibay/Folder1/ && sync -a -e ‘ssh -p customportnumber’ root@servera:/var/lib/nethserver/ibay/Folder2/ and so on.
On weekends we add the option --delete to rsync so deleted files on server A get deleted once a week on server B.
I started asking myself if it could be because on server A the users have read-write access - could that be the reason why the users can still write on the share on server B is the resync after all?
Would I have to modify the rsync options in order to keep access rights of the destination folder instead?
In any case I check and write down the share and sub-folder permissions but will have to do the reset later.
Share:
ls -l /var/lib/nethserver/ibay/
total 0
drwxrws—+ 6 root domain admins@ourdomain.tld 56 Jan 4 16:27 nethshare
getfacl /var/lib/nethserver/ibay/nethshare
getfacl: Removing leading '/' from absolute path names
# file: var/lib/nethserver/ibay/nethshare
# owner: root
# group: domain\040admins@ourdomain.tld
# flags: -s-
user::rwx
group::rwx
group:domain\040users@ourdomain.tld:r-x
mask::rwx
other::---
default:user::rwx
default:group::rwx
default:group:domain\040users@ourdomain.tld:r-x
default:mask::rwx
default:other::---
Subfolder:
ls -l /var/lib/nethserver/ibay/nethshare/subfolder1/
total 40
drwxrwsr-x+ 50 root domain users@ourdomain.tld 8192 Dec 28 16:27 Folder2
ls -l /var/lib/nethserver/ibay/nethshare/subfolder1/Folder2
-rw-rw----+ 1 user2@ourdomain.tld domain users@ourdomain.tld 0 Aug 16 2009 filename.pdf
(...)
getfacl /var/lib/nethserver/ibay/nethshare/subfolder1/
getfacl: Removing leading '/' from absolute path names
# file: var/lib/nethserver/ibay/nethshare/subfolder1/
# owner: root
# group: domain\040users@ourdomain.tld
# flags: -s-
user::rwx
group::rwx
group:domain\040users@ourdomain.tld:r-x
mask::rwx
other::---
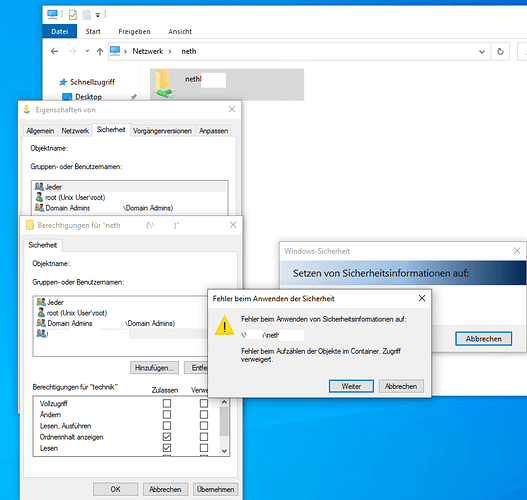
I checked again and while I indeed cannot create a subfolder in windows under \\serverb\nethshare I can create files and folders under \\serverb\nethshare\subfolders
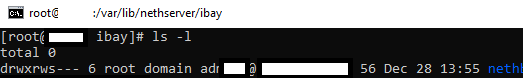
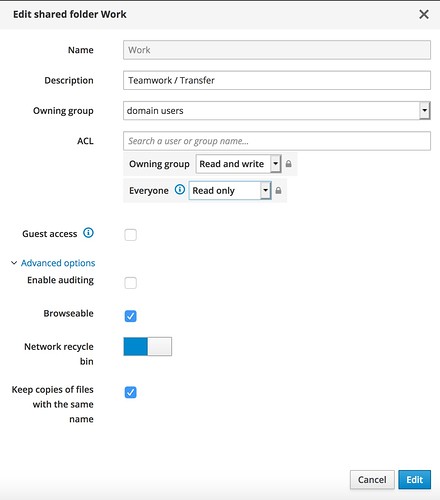
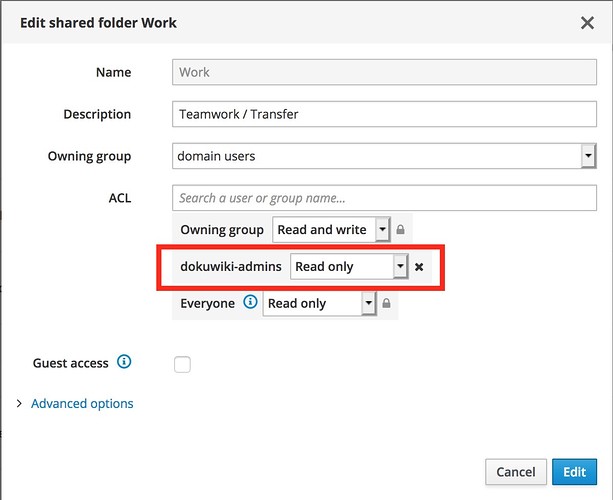
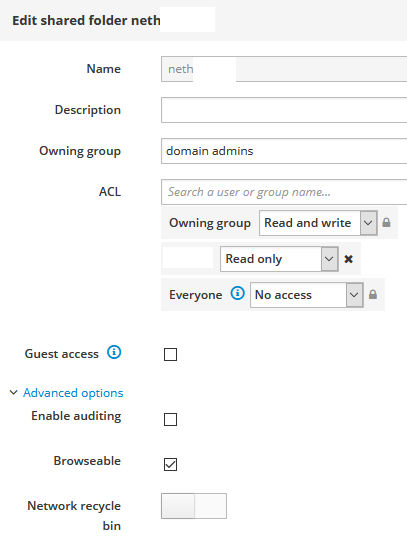
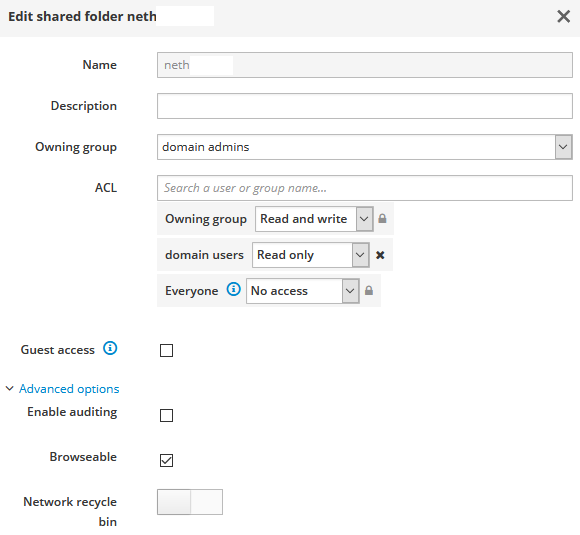
 - as I must admit I overlooked the ACL line. So I added a group there and configured read-only access for it.
- as I must admit I overlooked the ACL line. So I added a group there and configured read-only access for it.