Hello everyone, I have been using smsart relay for a long time on Nethserver on smtp microsoft, with my mail account, also downloading mail via the connector. Due to Google’s restrictions, I activated the full forward of emails from Gmail ver Outlook and as written before, via the server downloading everything. I occasionally get some samples from the Microsoft Team of unauthorized imap access and looking at the logs on my account on the Microsoft site, I occasionally see an access (strangely you belong to the Microsophot network with IMAP access). I changed the passworx, but nothing new. Is there a correlation between nethserver in smart hosts and imap cnnettor to all this? I also have 2 devices configured in SOGO in active sync,
Please, would you rewrite in a simple and schematic way?
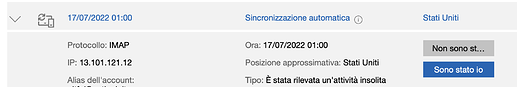
Arrangement, “unwanted behaviour” (with the device is signaling it) and IP address source of the unwanted behaviour.
I’d rather not assume the wrong thing because I misunderstood the situation…
Ok, I use the nethserver smarthost with microsoft servers and the imap connector to download mail from the microsoft account. I receive emails from Microsoft where I am notified of an IMAP synchronization from a US address (which is sempore microsoft). Looking at the login logs from the mail account on the Microsoft site, I see nethserver and this address. He asks me if there can be a correlation between the use of nethservers in imap and smart with all this.
These days I’m monitoring the server having first disabled the imap connector for downloading emails and synchronizing them. I have no longer received any notice of abnormal login regarding the email account. I didn’t deactivate the smart host of the same account for sending mail.
Therefore, IMO, the “acces violated” notification might be an inaccurate classification of traffic from Microsoft servers…
Hello, so how should the fact that I had those “Microsoft” ip alerts be interpreted? Loop ?
Maybe you should ask Microsoft?
I reported the suspicious activity, but a technical colleague wrote to me that in his opinion it could be the connector that in still unclear conditions generates loops.
As you read addresses are always and only “Microsoft” network, that’s why the colleague wrote that it could be an unstable connection that generate loops and then signal unauthorized access over an existing pre-connect. Also on abuse site, I found. another user with the same problem.
At the moment I have been deactivating the connector for several days, and no reports received. Consider everything I have written only and exclusively of verifications …