So as is often the case, one thing leads to another, which leads to another, and now I’m starting to look at SSO/IAM software. There appear to be a number of F/OSS solutions in this field, and it’s looking like it’s something that could improve system security quite a bit.
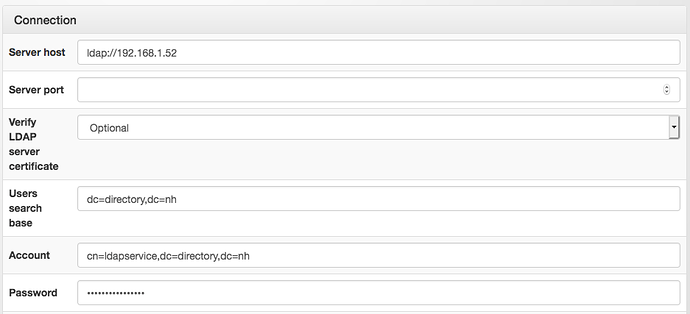
Right now, Neth uses LDAP (either a local OpenLDAP server, a remote one, or AD) for authentication. Applications take the username and password, validate them against the LDAP server, and grant access. It’s fairly simple, it’s widely supported, and it’s pretty easy to implement. But…
Every application that requires login is now at risk to compromise user credentials, because each of those applications handles those credentials. And if you want to implement 2FA, each application needs to support it, and you can only use the methods supported by that application.
By contrast, the SSO application handles authentication directly. When you click the Login button in Nextcloud, for example, you’re redirected to the SSO app, which authenticates you (including 2FA if desired), and then returns you to Nextcloud. Nextcloud never sees your password, so it can’t leak it. And if you want to use hardware authenticators like YubiKeys, Nextcloud doesn’t need to support FIDO2, U2F, or whatever. In addition, they typically support authentication mechanisms like SAML and OpenID Connect, allowing them to handle additional scenarios that LDAP won’t handle (the particular one I have in mind being using Step CA to issue SSH certificates).
So why aren’t we using them already? I expect there are a few major reasons:
- Complexity of installation
- Resource requirements
- Complexity of configuration–both for the SSO software, and for the client app
- Many web apps don’t support more involved authentication mechanisms like SAML or OIDC
I think the security benefit still makes them worth some investigation, and there are (as I said above) a few F/OSS options. I know of:
- Gluu (we already have the beginnings of a how-to on Gluu at How to install Gluu server, and I’ve been able to configure Gluu to pull users from Neth’s LDAP installation)
- WSO2 IS
- Keycloak
- LemonLDAP::NG
- ORY Hydra
AFAIK, all of these can authenticate against the LDAP database Neth is already using (being able to add users to that database, as Martin had been asking for, seems less common), so user creation wouldn’t necessarily need to change, but we would need to investigate having all of our other web apps use one of these other authenticators.
- Nextcloud is reported to have good support for SAML
- So is SOGo
- Other software would take some research
Here’s the start of a comparison table among the F/OSS products I know of. Feel free to suggest rows to add or corrections (unless a mod can make this a wiki post):
| Gluu | WSO2 IS | Keycloak | LemonLDAP::NG | ORY Hydra | |
|---|---|---|---|---|---|
| Client Authentication Technologies | |||||
| OpenID Connect |  |
 |
 |
 |
 |
| SAML |  |
 |
 |
 |
|
| CAS |  |
 |
|||
| HTTP Headers |  |
||||
| Other | |||||
| Written In | Java | Java | Java | Perl | Go |
| License | Apache 2.0 | Apache 2.0 | Apache 2.0 | GPL2 | Apache 2.0 |
| Doctor Who? |  |