Hi @ylavi
Storage:
I would not suggest using Proxmox directly as share for SMB. It’s possible, but compared with the rather comfortable WebGUIs you have for adminisrating PVE, the File Sharig would have NO GUI…
It would make more sense to add in a couple of disks as “Passthru”, so you could eg install a TrueNAS inside Proxmox, but using it’s own dedicated disks. The “System” disk of TrueNAS could be an ordinary VM Disk in Proxmox, the Storage of TrueNAS using passthru.
Cluster / Fast-Migration
Clusters can be used for full High Availability, but also “lesser” things come out of the box…
True that you need at least 2 nodes and a “voting” node eg as VM or a Raspberry, better is three full nodes, but hey, you get full High Availability!
But even without HA, or for those on the way to full HA:
For one, it makes managing VMs and VM-IDs much easier, especially on several Proxmox and PBS.
Secondly, this already gives you fast live migration between nodes!
Using a seperate 1 GB/S “Cluster” Network, it takes 90 seconds to live migrate a 200 GB VM with 12 GB RAM from one node to another…
Proxmox PVE does once in a while upgrade the kernel (much less often on the paid versions). PBS does not require a reboot, but PVE will (Due to VM usage). Using live Migration, the VMs running inside do not need to worry about downtime - just move the VMs on to another Proxmod, upgrade the server and reboot, then live migrate your VMs back… Really cool!
Networking
The more Proxmox, the more you want to think and plan your networking options.
Best would be a 10 GBE for your LAN, a seperate 10 GBE for Cluster-Network and maybe a 10 GBE as storage and another as Backup-Network.
I’m thinking here of shared storage for VMs (A requirement for fast Migration!) and Backups going via it’s own network, as these can generate high network loads.
That said, you can use anything from 1 GBE upwards, add BONDING or change NICs to 2.5 GBE or 10 GBE NICs…
Note:
A common mistake: BONDING 2 x 1 GBE will not allow a datastream running with 2 GB/S, but will allow 2 datastreams with each 1 GB/S… This is NOT the same thing!
Internal Security
Depending on your planned Environment, I would not overdo “internal security”. Keep your perimeter security top, I use a dedicated OPNsense box as hardware firewall protecting my Networks and also providing DHCP / DNS for all internal networks and also VPN services (I use both IPsec and OpenVPN, IPsec is my preference for site2site, and OpenVPN for RoadWarriors. Next up may be Wireguard, also available in OPNsense).
If you’re in an educational environment, or in some form of public WAN, by all means, treat each internal the same as external, top security.
In an Enterprise sort of environment, I would not place a firewall between clients and servers, unless you’re in a secure financial / military environment.
OPNsense
OPNsense is a great firewall, and the “official” successor to the M0n0wall system. I am known here on this Forum as a great fan of OPNsense, I also used the older M0n0wall. I only looked at PF-Sense, never really used it…
However, and this is valid for all BSD systems: While Linux has no issues distributing all routing an port forwarding CPU tasks to all cores available, BSD will allocate a single core for this task!
That has the great disadvantage of requireing a higher speed CPU, the amount of cores are fairly irrelevant.
In that sense, using eg DD-WRT or OpenWRT (Which I use at home) as a VM Router / Firewall may make more sense, at least performance wise.
However, and here are the big “gotchas”…
Both DD-WRT and OpenWRT are optimized as WiFi Routers on low levelhardware and do that well. But even here, where they are optimized, the GUIs are rather lacking…
Both can easily do firewalling and port-forwarding, also DNS and DHCP and even all three VPNs are available, from IPsec, OpenVPN and Wireguard. However, the GUIs are tendentially error-prone and errors are easily overseen. One notices, that these boxes aren’t optimized for firewall / router usage. And errors in security tend to be more dangerous than an unaccessible WiFi access point!
I do use several networks internally on Proxmox, often enough I do use an “internal” OPNsense to connect these, but in my case, it serves more LAB useses or emergency recovery, where I have to emulate a clients network rather than purely security needs.
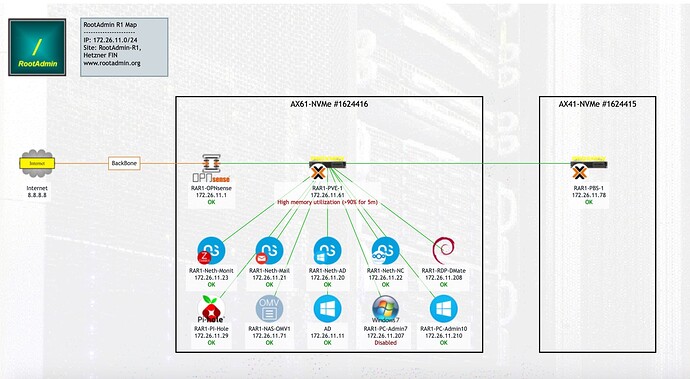
Here’s a sample of a “hosted” environment at Hetzner (Finnland): Two AMD Ryzen Servers, one as Proxmox, the other as PBS, with a second PBS at my Home.
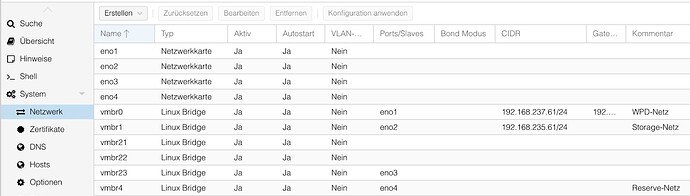
Networking on Proxmox at a client of mine:
Proxmox Cluster for SME, Home and LAB environments
Concept:
2 decent powered servers, to be used as full HA capable Proxmox PVE.These have plenty of RAM.
1 third, lesser server, to be used principally as Proxmox Backup Server (PBS) with enough storage space. A third Proxmox PVE runs also here, but normally no running VMs, only as voting member of the cluster to achieve a full cluster Quorum (=working and functioning cluster with voting capability.)…
Hope this is somewhat understandable…
My 2 cents
Andy