Is it possible to have clamav scanning samba shares automatically? I have setup an AD on one nethserver and added a second nethserver as memberserver to the created domain, which provides the fileshares. Is it possible to have clamav on the fileserver monitor the providing shares for viruses? How can this be configured if possible? I did not see an option in cockpit for that.
Thanks Stephdl, I’ll have a look. Will this package make it to official repo? I am asking, as we are going prod right now, and I don’t know, if it is a good idea to use unofficial package in a production environment. I think this feature is worth being available in main repo. I’ll make a backup before testing it.
Hello again,
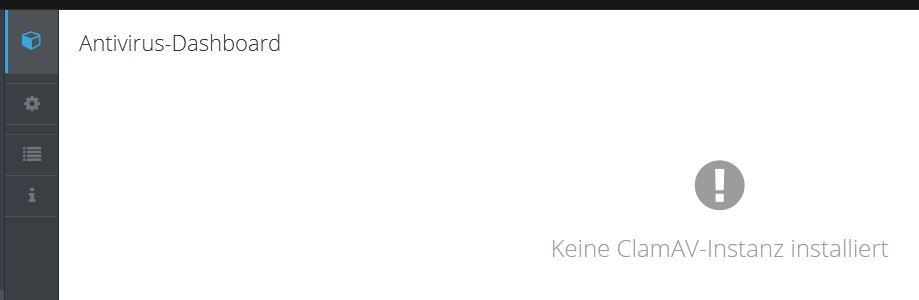
besides the already asked questions, I’d like to know, if it is normal that after installing and configuring clamscan if I go to applications / antivirus, I see the message: no ClamAV-Instanz installed. Is that normal?
No, because nethserver-clamscan installs nethserver-antivirus so it should be there. Maybe you need to clear browser cache?
Install from terminal:
yum install nethserver-antivirus
Far from a laptop, but after the installation IIRC the database is empty, it needs to be downloaded
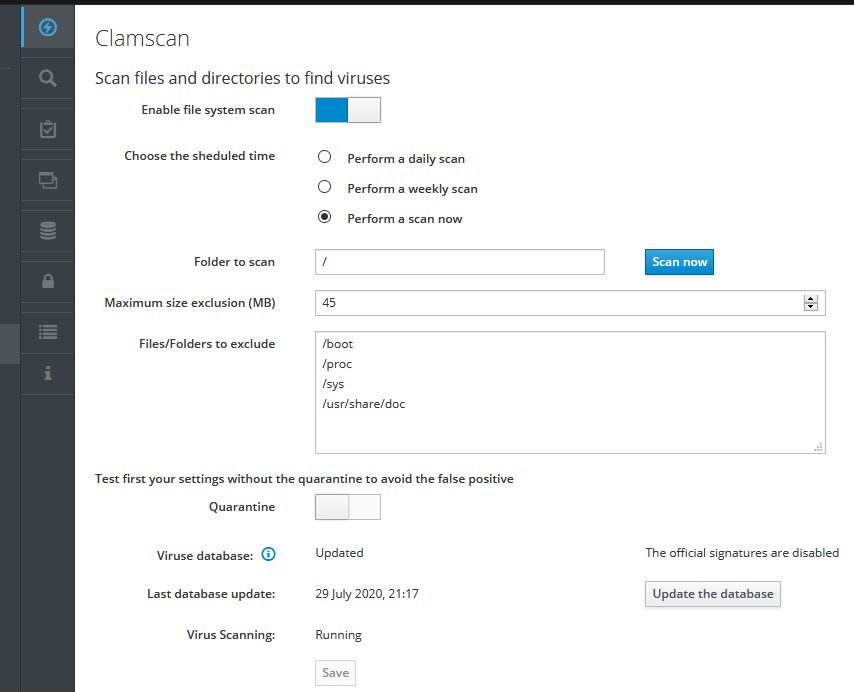
yum install nethserver-antivirus says nothing to do as its already installed the latest version. Runing clamscan seems to work. Its running for some hours now. Before I started perform scan now, I did update the database. I did not activate quarantine as mentioned in gui on the first run. Printscreens from other pc so should not be related to browser cache? Will this package make it to official repo? Should this be used in productive environnement. Having activated stephedl’s repo will not affect normal updates I hope?
top:
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
4188 root 30 10 1231012 1.1g 4184 R 98.0 7.0 243:04.83 clamscan
So there is apparently no realtime protection but the possibility to run the scan once a day or week as it seems? I am not comlaining, just asking 
I created a file /etc/e-smith/templates/etc/freshclam.conf/30securiteinfo with the links for freshclam.conf and then issued expand-template /etc/freshclam.conf. The lines were accordingly added to freshclam.conf. Is that all that needs to be done ? I am not yet familiar with e-smith thingy thus the question 
While running the initial scan, I added securiteinfo basic subspriction and issued a db update again. According to top freshclam now is running for for over 11 minutes. Is that normal? Ah now, while writing this it disapeared from top so it probably has done its thing. I also have changed the value of third party signatures to high in antivirus settings.
Thanks for all your great work, guys. Keep it up please 
OK, from your screenshot I can see that I completely misunderstood “no ClamAV-Instanz installed”. Everything is ok with your clamav/clamscan.
The Dashboard is empty because no clamav instance is installed/running. It could run with rspamd or with web proxy but you seem to have both disabled.
It is a good idea, because it’s the only way for unofficial packages to evolve to official ones.
You may test them in a VM before using in production.
As regards clamscan, it already is used on production systems.
Exactly.
The template file naming and location looks alright but which links did you add and why?
From the [docs](http://[quote=“Elleni, post:7, topic:15946”] I also have changed the value of third party signatures to high in antivirus settings. [/quote]) only low and medium is recommended.
You are right, as clamav for rspamd and proxy are on different nethservers. This is our fileserver nethserver thus it had no clamav installed until I added stephedl’s package to scan the shares this fileserver is providing. I directly installed it on our prod system  I just hope that having additional repo installed will not interfere with the normal repo. I created a basic subspription to securiteinfo to get their signatures additionally as linked in stephedl’s wiki about clamscan. I have seen that the value high is prone to more false positives, but thought, it would be more secure. If there are, I will change back to medium. Is there a recommended way to test if clamav is correctly doing its job? I mean as long as I see no warning or log entry whatsoever I am not sure it is doing anything after all. Maybe I will see anything in clamlog after the initial scan has finished…
I just hope that having additional repo installed will not interfere with the normal repo. I created a basic subspription to securiteinfo to get their signatures additionally as linked in stephedl’s wiki about clamscan. I have seen that the value high is prone to more false positives, but thought, it would be more secure. If there are, I will change back to medium. Is there a recommended way to test if clamav is correctly doing its job? I mean as long as I see no warning or log entry whatsoever I am not sure it is doing anything after all. Maybe I will see anything in clamlog after the initial scan has finished… 
Usually not. If there really are update issues, you may just disable problematic repos.
There is the eicar test file. Put it on your fileserver and check if clamscan catches it.
Good idea, will do so after the initial scan has finished, thanks! As its running for about 315 minutes now, I also wonder how long this could take. This nethserver show 433 GB used diskspace but it is running on a performant proxmox (zfs mirror with 2TB nvme disks with 64 GB of ram and this vm has 16GB assigned). Maybe the scan restarts from the beginning when I update the signature db?
You may check only a subfolder for testing.
ok, it finally finished and and I see it did its thing in the log:
----------- SCAN SUMMARY -----------
Known viruses: 8268152
Engine version: 0.102.3
Scanned directories: 23979
Scanned files: 173581
Infected files: 208
Data scanned: 222804.18 MB
Data read: 472845.72 MB (ratio 0.47:1)
Time: 19630.396 sec (327 m 10 s)
Most of the “infected” files are just: Heuristics.OLE2.ContainsMacros FOUND (so I disabled Mark OLE2 files containing VBA macros as viruses) and some are Heuristics.Phishing.Email.SpoofedDomain FOUND.
But what about those?
/var/lib/clamav-unofficial-sigs/dbs-lmd/sigpack.tgz: Php.Exploit.C99-27 FOUND
/var/lib/clamav-unofficial-sigs/dbs-lmd/rfxn.yara: Php.Exploit.C99-27 FOUND
False positive?
Yes, see ClamAV Alert about new config version - #40 by filippo_carletti
You may exclude /var/lib/clamav-unofficial-sigs from scan in GUI.
thanks again, will do so.
The only one worrying me a bit is:
/var/ib/nethserver/ibay/…/Downloads/tcpview/Tcpview.exe: Win.Trojan.Ldpinch-2067 FOUND
A quick google shearch did not show a known false positive ![]()
Well it was just copied over during migration. Hope as it was not executed, it did not compromise the system… ![]()
It already was a false positive some time ago.
Maybe you can check it with another virus scanner.
Oh, thanks, thats reassuring. Yeah, or directly delete it if not needed. Atm it is quarantined 
Edit to add that with unofficial on high, I had many false positives (Sanesecurity.Foxhole.Zip) so I changed to medium as recommended by documentation and by you