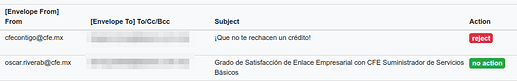
What can I do to have this sender’s emails accepted on my server?
We have an service provider that has misconfigured their server or maybe my own server has it blocked; and I can’t receive their emails.
This appears in the blocked mail
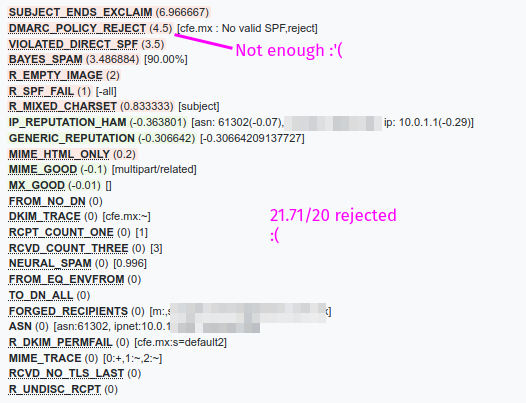
FUZZY_DENIED (15) [1:fc284e33f6:1.00:txt]
DMARC_POLICY_REJECT (12) [xyz.mx : No valid SPF,reject]
BAYES_SPAM (8.092517) [99.98%]
VIOLATED_DIRECT_SPF (3.5)
R_SPF_FAIL (1) [-all:c]
IP_REPUTATION_HAM (-0.334835) [no useful because my dmz/firewall]
GENERIC_REPUTATION (-0.289587) [-0.2895866339342]
MIME_HTML_ONLY (0.2)
RCVD_NO_TLS_LAST (0.1)
MIME_BASE64_TEXT (0.1)
MX_GOOD (-0.01) []
HAS_LIST_UNSUB (-0.01)
FROM_NO_DN (0)
DKIM_TRACE (0) [xyz.mx:~]
R_DKIM_PERMFAIL (0) [xyz.mx:s=default2]
RCPT_COUNT_ONE (0) [1]
PREVIOUSLY_DELIVERED (0) [myuser@miserver.com]
TO_DN_NONE (0)
ASN (0) [not useful by dmz/firewall]
NEURAL_SPAM (0) [0.900]
TO_MATCH_ENVRCPT_ALL (0)
MIME_TRACE (0) [0:~]
RCVD_COUNT_THREE (0) [3]
FROM_EQ_ENVFROM (0)
This was from yesterday to today morning, at noon I added it to the “Accept from” filter, and it changed a little bit but still rejecting them.
Symbol "FUZZY_DENIED (15) [1:fc284e33f6:1.00:txt]" has disappeared but still blocking
DMARC_POLICY_REJECT (12) [xyz.mx : No valid SPF,reject]
BAYES_SPAM (8.09739) [99.99%]
VIOLATED_DIRECT_SPF (3.5)
R_SPF_FAIL (1) [-all]
IP_REPUTATION_HAM (-0.333909) [not useful by dmz/firewall]
GENERIC_REPUTATION (-0.288753) [-0.28875315363048]
MIME_HTML_ONLY (0.2)
RCVD_NO_TLS_LAST (0.1)
MIME_BASE64_TEXT (0.1)
MX_GOOD (-0.01) []
HAS_LIST_UNSUB (-0.01)
FROM_NO_DN (0)
DKIM_TRACE (0) [xyz.mx:~]
RCPT_COUNT_ONE (0) [1]
PREVIOUSLY_DELIVERED (0) [myuser@miserver.com]
TO_DN_NONE (0)
R_DKIM_PERMFAIL (0) [xyz.mx:s=default2]
ASN (0) [not useful by dmz/firewall]
TO_MATCH_ENVRCPT_ALL (0)
MIME_TRACE (0) [0:~]
NEURAL_SPAM (0) [0.773]
RCVD_COUNT_THREE (0) [3]
FROM_EQ_ENVFROM (0)
Interestingly, an email did arrive from someone else from the same server; I suspect they have more than one server and one of them is misconfigured (spf) hence the rejection.
This is from yesterday:
SUBJ_ALL_CAPS (1.2) [50]
BAYES_HAM (-0.545883) [80.81%]
DMARC_POLICY_ALLOW_WITH_FAILURES (-0.5)
IP_REPUTATION_HAM (-0.331496) [not useful by dmz/firewall]
GENERIC_REPUTATION (-0.287315) [-0.28731519734701]
R_DKIM_ALLOW (-0.2) [xyz.mx:s=selector1]
MIME_GOOD (-0.1) [multipart/mixed,multipart/alternative,text/plain]
MX_GOOD (-0.01) []
DKIM_TRACE (0) [xyz.mx:+]
RCVD_TLS_LAST (0)
FROM_HAS_DN (0)
R_SPF_FAIL (0) [-all]
NEURAL_HAM (0) [-0.999]
ASN (0) [not useful by dmz/firewall]
FROM_EQ_ENVFROM (0)
RCPT_COUNT_TWO (0) [2]
TO_DN_SOME (0)
TO_DN_EQ_ADDR_SOME (0)
MIME_TRACE (0) [0:+,1:+,2:+,3:~,4:~]
DMARC_POLICY_ALLOW (0) [xyz.mx,reject]
RCVD_COUNT_THREE (0) [3]
TO_MATCH_ENVRCPT_SOME (0)
HAS_ATTACHMENT (0)
Thanks in advance and best regards.
Edit 1.
I have looked for a way to delete that FUZZY_DENIED (15) [1:fc284e33f6:1.00:txt], but I have not been able to find an example or something very detailed to see if this is the cause.
And I don’t even know if it is possible to simulate the sending of that sender to check that I could receive it
(I’m thinking of something, I’ll try and comment).
I will see if editing the code of the accepted mail I can simulate the sending of the blocked sender.
Ediit 2.
It seems to have worked, but we will see if their mails arrive.
I wonder if bad emails will arrive with this. ![]()