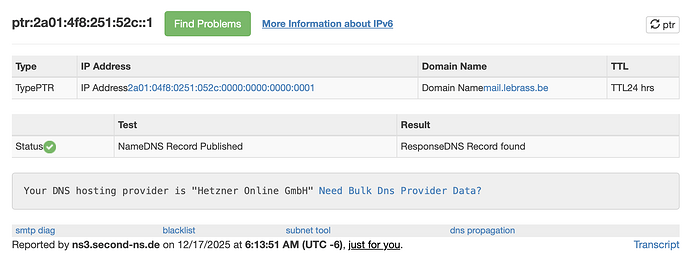
Without DQS (as per @mrmarkuz ‘s first instructions), the SMTP (connection) test and Content test are failing - all their junk emails are passing the filter.
SMTP test :
C: <Establish TCP connection>
S: 220-mail.redacted.be ESMTP Postfix
S: 220 mail.redacted.be ESMTP Postfix
C: EHLO pbl-pub.blt.spamhaus.net
S: 250-mail.redacted.be
S: 250-PIPELINING
S: 250-SIZE 100000000
S: 250-VRFY
S: 250-ETRN
S: 250-STARTTLS
S: 250-ENHANCEDSTATUSCODES
S: 250-8BITMIME
S: 250-DSN
S: 250 CHUNKING
C: MAIL FROM:<test@pbl-pub.blt.spamhaus.net>
S: 250 2.1.0 Ok
C: RCPT TO:<matthieu@redacted.be>
S: 250 2.1.5 Ok
C: DATA
S: 354 End data with <CR><LF>.<CR><LF>
C: Content-Type: text/plain; charset="utf-8"
C: Content-Transfer-Encoding: 7bit
C: MIME-Version: 1.0
C: Date: Wed, 17 Dec 2025 12:54:31 +0000
C: Message-ID: <176597607165.198160.13477353149981201691@blt.spamhaus.net>
C: Subject: BLT Public SMTP Test Email (65871:797868:pbl-pub-ip)
C: From: Spamhaus Blocklist Tester <test@pbl-pub.blt.spamhaus.net>
C: To: matthieu@redacted.be
C:
C: This is a Spamhaus BLT public SMTP-test email which has been crafted
C: to be blocked by properly configured mail systems. If you're reading
C: this then your MX is not properly configured for the pbl-pub-ip test;
C: please see the BLT documentation at https://blt.spamhaus.com/docs for
C: tips on configuring your MX.
C:
C: Description of this test:
C:
C: This is a test of src IP blocking via the Public Mirrors Policy Blocklist (PBL):
C: https://docs.spamhaus.com/datasets/docs/source/10-data-type-documentation/datasets/030-datasets.html
C:
C: You can view more information about this test email at
C: https://blt.spamhaus.com/test/65871/email/797868
C:
C: Test parameters:
C: - MX: mail.redacted.be
C: - MX IP: 168.119.140.207
C: - SRC IP: 199.168.89.86
C: - EHLO: pbl-pub.blt.spamhaus.net
C: - MAIL FROM: test@pbl-pub.blt.spamhaus.net
C: - RCPT TO: matthieu@redacted.be
C: - TEST ID: 65871
C: - EMAIL ID: 797868
C: - TIER: public
C:
C: .
S: 250 2.0.0 Ok: queued as 35EC12228A1
C: QUIT
S: 221 2.0.0 Bye
C: <Close TCP connection>
- Our logs (filtered on their IP) :
2025-12-17T13:54:31+01:00 [1:mail1:postfix/postscreen] CONNECT from [199.168.89.86]:35117 to [myp.IP]:25
2025-12-17T13:54:33+01:00 [1:mail1:redis-persistent] DB saved on disk
2025-12-17T13:54:33+01:00 [1:mail1:redis-persistent] Fork CoW for RDB: current 0 MB, peak 0 MB, average 0 MB
2025-12-17T13:54:33+01:00 [1:mail1:redis-persistent] Background saving terminated with success
2025-12-17T13:54:35+01:00 [1:mail1:postfix/smtpd] connect from 177.218-201-80.adsl-dyn.isp.belgacom.be[80.201.218.177]
2025-12-17T13:54:35+01:00 [1:mail1:rspamd] (rspamd_proxy) <be9987>; proxy; proxy_accept_socket: accepted milter connection from 127.0.0.1 port 37604
2025-12-17T13:54:35+01:00 [1:mail1:postfix/smtpd] Anonymous TLS connection established from 177.218-201-80.adsl-dyn.isp.belgacom.be[80.201.218.177]: TLSv1.3 with cipher TLS_AES_256_GCM_SHA384 (256/256 bits) key-exchange X25519 server-signature RSA-PSS (4096 bits) server-digest SHA256
2025-12-17T13:54:36+01:00 [1:mail1:rspamd] (rspamd_proxy) <be9987>; milter; rspamd_milter_process_command: got connection from 80.201.218.177:38658
2025-12-17T13:54:36+01:00 [1:mail1:postfix/smtpd] disconnect from 177.218-201-80.adsl-dyn.isp.belgacom.be[80.201.218.177] ehlo=2 starttls=1 quit=1 commands=4
2025-12-17T13:54:36+01:00 [1:mail1:rspamd] (rspamd_proxy) <be9987>; proxy; proxy_milter_finish_handler: finished milter connection
2025-12-17T13:54:37+01:00 [1:mail1:postfix/postscreen] PASS NEW [199.168.89.86]:35117
2025-12-17T13:54:37+01:00 [1:mail1:postfix/smtpd] connect from pbl-pub.blt.spamhaus.net[199.168.89.86]
2025-12-17T13:54:37+01:00 [1:mail1:rspamd] (rspamd_proxy) <e9d3e2>; proxy; proxy_accept_socket: accepted milter connection from 127.0.0.1 port 37612
2025-12-17T13:54:38+01:00 [1:mail1:postfix/smtpd] 35EC12228A1: client=pbl-pub.blt.spamhaus.net[199.168.89.86]
2025-12-17T13:54:38+01:00 [1:mail1:rspamd] (rspamd_proxy) <e9d3e2>; milter; rspamd_milter_process_command: got connection from 199.168.89.86:35117
2025-12-17T13:54:38+01:00 [1:mail1:postfix/cleanup] 35EC12228A1: message-id=<176597607165.198160.13477353149981201691@blt.spamhaus.net>
2025-12-17T13:54:38+01:00 [1:mail1:rspamd] (normal) <54710a>; task; rspamd_worker_body_handler: accepted connection from ::1 port 43022, task ptr: 00007F9B4A8C5058
2025-12-17T13:54:38+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; rspamd_message_parse: loaded message; id: <176597607165.198160.13477353149981201691@blt.spamhaus.net>; queue-id: <35EC12228A1>; size: 1286; checksum: <ae3983f72c591afdfd0b6f491eefecfd>
2025-12-17T13:54:38+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; rspamd_mime_part_detect_language: detected part language: en
2025-12-17T13:54:38+01:00 [1:mail1:rspamd] (normal) <35EC12>; lua; clamav.lua:131: clamav: message or mime_part is clean
2025-12-17T13:54:38+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; rspamd_spf_maybe_return: stored SPF record for pbl-pub.blt.spamhaus.net (0x1ce2977d59eb1173) in LRU cache for 3600 seconds, 128/2000 elements in the cache
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; finalize_item: slow asynchronous rule: URIBL_MULTI(569): 519.00 ms; no idle timer is needed
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; finalize_item: slow synchronous rule: RBL_CALLBACK(581): 519.00 ms; enable 100ms idle timer to allow other rules to be finished
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; finalize_item: slow synchronous rule: NEURAL_CHECK(449): 1091.68 ms; idle timer has already been activated for this scan
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; finalize_item: slow asynchronous rule: HISTORY_SAVE(404): 1092.68 ms; no idle timer is needed
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; finalize_item: slow synchronous rule: MILTER_HEADERS(411): 1092.68 ms; idle timer has already been activated for this scan
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; finalize_item: slow asynchronous rule: NEURAL_LEARN(452): 1092.68 ms; no idle timer is needed
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; finalize_item: slow synchronous rule: RATELIMIT_UPDATE(464): 1092.68 ms; idle timer has already been activated for this scan
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; finalize_item: slow asynchronous rule: REPLIES_SET(582): 1092.68 ms; no idle timer is needed
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; rspamd_task_write_log: id: <176597607165.198160.13477353149981201691@blt.spamhaus.net>, qid: <35EC12228A1>, ip: 199.168.89.86, from: <test@pbl-pub.blt.spamhaus.net>, (default: F (no action): [-0.95/15.00] [BAYES_HAM(-1.25){89.72%;},MX_INVALID(0.50){},R_SPF_ALLOW(-0.20){+ip4:199.168.89.86/32;},MIME_GOOD(-0.10){text/plain;},ONCE_RECEIVED(0.10){},ARC_NA(0.00){},ASN(0.00){asn:54054, ipnet:199.168.88.0/22, country:US;},DBL_BLOCKED_OPENRESOLVER(0.00){spamhaus.com:url;redacted.be:url;redacted.be:email;spamhaus.net:url;spamhaus.net:email;pbl-pub.blt.spamhaus.net:helo;pbl-pub.blt.spamhaus.net:rdns;},DMARC_NA(0.00){spamhaus.net;},FROM_EQ_ENVFROM(0.00){},FROM_HAS_DN(0.00){},MID_RHS_MATCH_FROMTLD(0.00){},MIME_TRACE(0.00){0:+;},MISSING_XM_UA(0.00){},RCPT_COUNT_ONE(0.00){1;},RCVD_COUNT_ZERO(0.00){0;},R_DKIM_NA(0.00){},TO_DN_NONE(0.00){},TO_MATCH_ENVRCPT_ALL(0.00){}]), len: 1286, time: 1091.449ms, dns req: 43, digest: <ae3983f72c591afdfd0b6f491eefecfd>, rcpts: <matthieu@redacted.be>, mime_rcpts: <matthieu@redacted.be>
2025-12-17T13:54:39+01:00 [1:mail1:rspamd] (normal) <35EC12>; task; rspamd_protocol_http_reply: regexp statistics: 0 pcre regexps scanned, 2 regexps matched, 179 regexps total, 50 regexps cached, 0B scanned using pcre, 3.37KiB scanned total
2025-12-17T13:54:39+01:00 [1:mail1:postfix/qmgr] 35EC12228A1: from=<test@pbl-pub.blt.spamhaus.net>, size=1528, nrcpt=1 (queue active)
2025-12-17T13:54:39+01:00 [1:mail1:dovecot] lmtp(166998): Connect from local
2025-12-17T13:54:39+01:00 [1:mail1:postfix/smtpd] disconnect from pbl-pub.blt.spamhaus.net[199.168.89.86] ehlo=1 mail=1 rcpt=1 data=1 quit=1 commands=5
Content test
C: <Establish TCP connection>
S: 220 mail.redacted.be ESMTP Postfix
C: EHLO unlisted.blt.spamhaus.net
S: 250-mail.redacted.be
S: 250-PIPELINING
S: 250-SIZE 100000000
S: 250-VRFY
S: 250-ETRN
S: 250-STARTTLS
S: 250-ENHANCEDSTATUSCODES
S: 250-8BITMIME
S: 250-DSN
S: 250 CHUNKING
C: MAIL FROM:<test@unlisted.blt.spamhaus.net>
S: 250 2.1.0 Ok
C: RCPT TO:<matthieu@redacted.be>
S: 250 2.1.5 Ok
C: DATA
S: 354 End data with <CR><LF>.<CR><LF>
C: Content-Type: text/plain; charset="utf-8"
C: Content-Transfer-Encoding: 7bit
C: MIME-Version: 1.0
C: Date: Wed, 17 Dec 2025 13:24:51 +0000
C: Message-ID: <176597789131.198160.18132445613854290703@blt.spamhaus.net>
C: Subject: BLT DQS Content Test Email (65874:797892:sbl-dqs-body-ip)
C: From: Spamhaus Blocklist Tester <test@unlisted.blt.spamhaus.net>
C: To: matthieu@redacted.be
C:
C: This is a Spamhaus BLT DQS content-test email which has been
C: crafted to be flagged as spam by properly configured mail systems. If
C: your MX is correctly configured to do content filtering for the
C: sbl-dqs-body-ip test, then this email should be flagged as spam (check the
C: headers) or rejected outright. If this email was delivered, and not
C: classified as spam, then your MX is not correctly configured for the
C: sbl-dqs-body-ip test; please see the BLT documentation at
C: https://blt.spamhaus.com/docs for tips on configuring your MX.
C:
C: Description of this test:
C:
C: This is a test of bad-IP-in-body blocking
C: via the DQS Spamhaus Blocklist (SBL):
C: https://docs.spamhaus.com/datasets/docs/source/10-data-type-documentation/datasets/030-datasets.html
C:
C: The bad IP address is http://199.168.89.88.
C:
C: You can view more information about this test email at
C: https://blt.spamhaus.com/test/65874/email/797892
C:
C: Test parameters (some parameters omitted here to avoid accidental
C: flagging when the email body is scanned):
C: - MX: mail.redacted.be
C: - MX IP: My IP
C: - RCPT TO: matthieu@redacted.be
C: - TEST ID: 65874
C: - EMAIL ID: 797892
C: - TIER: DQS
C:
C: .
S: 250 2.0.0 Ok: queued as BE3222228A1
C: QUIT
S: 221 2.0.0 Bye
C: <Close TCP connection>
2025-12-17T14:24:51+01:00 [1:mail1:postfix/postscreen] CONNECT from [199.168.89.101]:43629 to [My.IP]:25
2025-12-17T14:24:51+01:00 [1:mail1:postfix/postscreen] PASS OLD [199.168.89.101]:43629
2025-12-17T14:24:51+01:00 [1:mail1:postfix/smtpd] connect from unlisted.blt.spamhaus.net[199.168.89.101]
2025-12-17T14:24:51+01:00 [1:mail1:rspamd] (rspamd_proxy) <75648b>; proxy; proxy_accept_socket: accepted milter connection from 127.0.0.1 port 40316
2025-12-17T14:24:51+01:00 [1:mail1:postfix/smtpd] BE3222228A1: client=unlisted.blt.spamhaus.net[199.168.89.101]
2025-12-17T14:24:51+01:00 [1:mail1:rspamd] (rspamd_proxy) <75648b>; milter; rspamd_milter_process_command: got connection from 199.168.89.101:43629
2025-12-17T14:24:52+01:00 [1:mail1:postfix/smtpd] lost connection after AUTH from unknown[119.96.209.119]
2025-12-17T14:24:52+01:00 [1:mail1:postfix/smtpd] disconnect from unknown[119.96.209.119] ehlo=1 auth=0/1 commands=1/2
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (rspamd_proxy) <866547>; milter; rspamd_milter_process_command: got connection from 119.96.209.119:52780
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (rspamd_proxy) <866547>; proxy; proxy_milter_finish_handler: finished milter connection
2025-12-17T14:24:52+01:00 [1:mail1:postfix/cleanup] BE3222228A1: message-id=<176597789131.198160.18132445613854290703@blt.spamhaus.net>
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <da044e>; task; rspamd_worker_body_handler: accepted connection from ::1 port 48410, task ptr: 00007F9B4B5E1098
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; rspamd_message_parse: loaded message; id: <176597789131.198160.18132445613854290703@blt.spamhaus.net>; queue-id: <BE3222228A1>; size: 1541; checksum: <936c50f85fc6c9327127c4a5a4c92854>
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; rspamd_mime_part_detect_language: detected part language: en
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; lua; spf.lua:163: use cached record for unlisted.blt.spamhaus.net (0xde7b60e403cd5031) in LRU cache for 1738 seconds
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; lua; rbl.lua:289: error looking up 101.89.168.199.bl.blocklist.de: server fail
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; lua; clamav.lua:131: clamav: message or mime_part is clean
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow asynchronous rule: URIBL_MULTI(569): 321.00 ms; no idle timer is needed
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow asynchronous rule: RSPAMD_URIBL(516): 364.00 ms; no idle timer is needed
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow synchronous rule: RBL_CALLBACK(581): 364.00 ms; idle timer has already been activated for this scan
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow synchronous rule: NEURAL_CHECK(449): 365.00 ms; idle timer has already been activated for this scan
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow asynchronous rule: HISTORY_SAVE(404): 365.00 ms; no idle timer is needed
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow synchronous rule: MILTER_HEADERS(411): 365.00 ms; idle timer has already been activated for this scan
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; lua; neural.lua:355: skip ham sample to keep spam/ham balance; probability 0.6458333333333333; 51 spam and 143 ham vectors stored
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow asynchronous rule: NEURAL_LEARN(452): 366.00 ms; no idle timer is needed
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow synchronous rule: RATELIMIT_UPDATE(464): 366.00 ms; idle timer has already been activated for this scan
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; finalize_item: slow asynchronous rule: REPLIES_SET(582): 366.00 ms; no idle timer is needed
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; rspamd_task_write_log: id: <176597789131.198160.18132445613854290703@blt.spamhaus.net>, qid: <BE3222228A1>, ip: 199.168.89.101, from: <test@unlisted.blt.spamhaus.net>, (default: F (no action): [-1.31/15.00] [BAYES_HAM(-1.61){92.54%;},MX_INVALID(0.50){},R_SPF_ALLOW(-0.20){+ip4:199.168.89.101/32:c;},MIME_GOOD(-0.10){text/plain;},ONCE_RECEIVED(0.10){},ARC_NA(0.00){},ASN(0.00){asn:54054, ipnet:199.168.88.0/22, country:US;},BLOCKLISTDE_FAIL(0.00){199.168.89.101:server fail;},DBL_BLOCKED_OPENRESOLVER(0.00){unlisted.blt.spamhaus.net:helo;unlisted.blt.spamhaus.net:rdns;blt.spamhaus.net:mid;redacted.be:url;redacted.be:email;spamhaus.com:url;},DMARC_NA(0.00){spamhaus.net;},FROM_EQ_ENVFROM(0.00){},FROM_HAS_DN(0.00){},MID_RHS_MATCH_FROMTLD(0.00){},MIME_TRACE(0.00){0:+;},MISSING_XM_UA(0.00){},RCPT_COUNT_ONE(0.00){1;},RCVD_COUNT_ZERO(0.00){0;},R_DKIM_NA(0.00){},TO_DN_NONE(0.00){},TO_MATCH_ENVRCPT_ALL(0.00){}]), len: 1541, time: 364.938ms, dns req: 37, digest: <936c50f85fc6c9327127c4a5a4c92854>, rcpts: <matthieu@redacted.be>, mime_rcpts: <matthieu@redacted.be>
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (normal) <BE3222>; task; rspamd_protocol_http_reply: regexp statistics: 0 pcre regexps scanned, 2 regexps matched, 179 regexps total, 50 regexps cached, 0B scanned using pcre, 4.10KiB scanned total
2025-12-17T14:24:52+01:00 [1:mail1:postfix/qmgr] BE3222228A1: from=<test@unlisted.blt.spamhaus.net>, size=1786, nrcpt=1 (queue active)
2025-12-17T14:24:52+01:00 [1:mail1:dovecot] lmtp(167211): Connect from local
2025-12-17T14:24:52+01:00 [1:mail1:postfix/smtpd] disconnect from unlisted.blt.spamhaus.net[199.168.89.101] ehlo=1 mail=1 rcpt=1 data=1 quit=1 commands=5
2025-12-17T14:24:52+01:00 [1:mail1:rspamd] (rspamd_proxy) <bf0250>; proxy; proxy_milter_finish_handler: finished milter connection
2025-12-17T14:24:52+01:00 [1:mail1:dovecot] lmtp(matthieu)<167211><mKeoHCSvQmkrjQIA/2Rcwg>: save: box=INBOX, uid=83193, msgid=<176597789131.198160.18132445613854290703@blt.spamhaus.net>, from=Spamhaus Blocklist Tester <test@unlisted.blt.spamhaus.net>, subject=BLT DQS Content Test Email (65874:797892:sbl-dqs-body-ip), flags=()
I should take more time to analyse this but can’t right now.