Andy gave us the answer here as a quick how to.
Step 1 - Create directory for host-to-net.conf template
mkdir -p /etc/e-smith/templates-custom/etc/openvpn/host-to-net.conf/
Step 2 - Copy template files to new directory
cp -r /etc/e-smith/templates/etc/openvpn/host-to-net.conf/* /etc/e-smith/templates-custom/etc/openvpn/host-to-net.conf/
Step 3 - Add desired configuration to file within new custom-templates directory
nano /etc/e-smith/templates-custom/etc/openvpn/host-to-net.conf/customDNSsettings
push "block-outside-dns"
push "register-dns"
#Royce was here
Save your edited file. NOTE the name is arbitrarily set (the CustomDNSsettings name can be labeled whatever you want).
Step 4 - Exapnd the template to include the custom settings into Road Warrior VPN
expand-template /etc/openvpn/host-to-net.conf
Step 5 - Restart Road Warrior service
systemctl restart openvpn@host-to-net
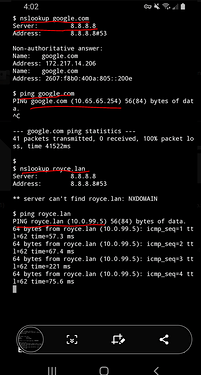
On a side note I did some testing with my Android phone & PoP_OS VM with Pi-Hole as the DNS server. I found that even though I was connected to the VPN when I used utilities like dig & nslookup I would have my primary DNS (or whatever the app has hard coded) respond with an authoritative answer but when I pinged the address the Pi-Hole was used for resolution on my split tunnel VPN. As a test in Pi-Hole I created a custom DNS entry for google.com as an A record of 10.65.65.254. This makes me think that the DNS to the Pi-Hole may be working as intended but I cannot 100% validate it. See picture for results:
NS LAN - 10.22.0.1/24 acting as a gateway/router with RED interface of 10.0.99.125.
Pi-Hole - 10.22.0.3
OpenVPN Network - 10.22.22.0/24
OpenVPN RoadWarror Config
dev tunrw
server 10.22.22.0 255.255.255.0
ifconfig-pool-persist host-to-net.pool 0
UDP server
port 1194
proto udp
topology subnet
client-connect /usr/libexec/nethserver/openvpn-connect
client-disconnect /usr/libexec/nethserver/openvpn-disconnect
script-security 3
float
multihome
dh /var/lib/nethserver/certs/dh1024.pem
ca /etc/pki/tls/certs/NSRV.crt
cert /etc/pki/tls/certs/NSRV.crt
key /etc/pki/tls/private/NSRV.key
crl-verify /var/lib/nethserver/certs/crl.pem
client-to-client
push “dhcp-option DOMAIN nethsa.ga”
push “dhcp-option DNS 10.22.0.3”
push “dhcp-option WINS 10.22.22.1”
push “dhcp-option NBDD 10.22.22.1”
push “dhcp-option NBT 2”
push “route 10.22.0.0 255.255.255.0”
Authentication: certificate
status /var/log/openvpn/host-to-net-status.log
log-append /var/log/openvpn/openvpn.log
passtos
keepalive 20 120
client-config-dir ccd
persist-key
persist-tun
management /var/spool/openvpn/host-to-net unix
verb 3
push “block-outside-dns”
push “register-dns”
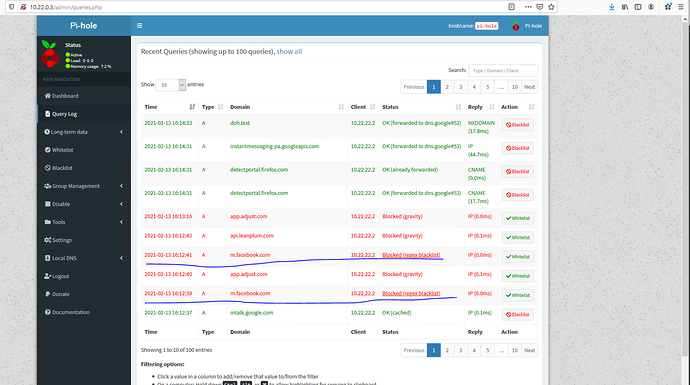
EDIT - further testing this on my Android OpenVPN connection I blacklisted Facebook.com with Wildcard and when connected to the VPN Facebook.com is unreachable on my android mobile device. Maybe the apps we are using for the nslookup/dig are just feeding us bad information and the VPN/DNS settings are working as expected?