now i am confused
i try to keep it simple 
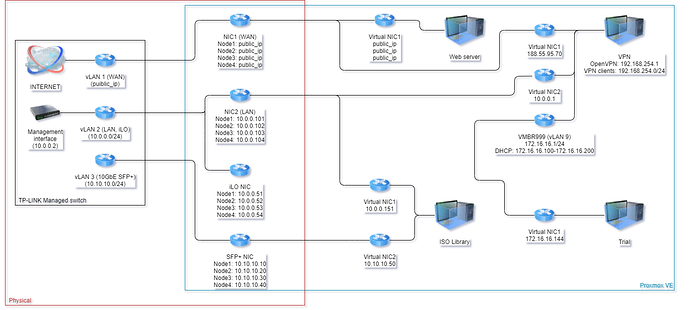
so my setup exist of the following
it is located in a datacenter
1 uplink to switch
3 connections from switch to a node
1 public ip assigned to the node for remote acces ( and web based novnc console )
few other things setup on there for Ceph and HA and communication betwean the 4 nodes
every node is in a cluster , so no mather where i create a vps on , it works on all of them
as the network is just a bridge ( virtual bridge ) to the vps servers ( virtual machines )
so i get the following layout
uplink -> switch -> node --> vps
uiplink is gateway for internet
switch just switch to the right ports and vlan
node contains public ip for remote access ( and novnc console )
vps contains public ip as stand alone ( webserver for example ) but move freely betwean the 4 nodes (cluster + HA + Ceph )
Cluster/HA/Ceph use a 10Gbit network on local ip range ( 10.10.10.0/24 ) and serperate Vlan , else my network get really fast overloaded
i do not want that other users got access to my switch or ilo , so they are on a local ip ( 10.0.0.0/24 ) and serperate Vlan
at this poiint everything works like i need to have it
but for protection i want to have a firewall betwean it
port forwarding to a single node does not going work , as the vps servers freely move betwean nodes ( High Avaiblity/Fail Over )
so if i can set it up that a public ip can be used , then it does not mather where the vps is located as it will always be able to communicate to the internet
and then the firewall is just a transparant firewall that does block attacks , but nothing else
but before i can place a hardware firewall do i need to make sure it works
else i am totaly locked out of my network, and that is what i try to prevent 
maybe i make things to complicated ? but this is what i try to archive
and if the firewall contains a vpn , then i like to also use that to access my other vlans ( need then 2 ports to connect to the switch as it are differend vlans )
or is there a other way to get the setup i have ? or a easyer way to do this ?
Greets from PowerChaos